2026-03-09 23:31:31
Agents are smarter when they can search the web - but with SerpApi, you don’t need to reinvent the wheel. SerpApi gives your AI applications clean, structured web data from major search engines and marketplaces, so your agents can research, verify, and answer with confidence.
Access real-time data with a simple API.
The AI open-source ecosystem has entered an extraordinary growth phase.
GitHub’s Octoverse 2025 report revealed that over 4.3 million AI-related repositories now exist on the platform, a 178% year-over-year jump in LLM-focused projects alone. In this environment, a select group of repositories has emerged as clear frontrunners, each amassing tens or even hundreds of thousands of stars by offering developers the tools to build autonomous agents, deploy models locally, and streamline AI-powered workflows.
Let’s look at the most impactful AI repositories trending on GitHub right now, covering what they do, why they matter, and how they fit into the broader AI landscape.
OpenClaw is the breakout star of 2026 and arguably the fastest-growing open-source project in GitHub history.
Created by PSPDFKit founder Peter Steinberger, it surged from 9,000 to over 60,000 stars in just a few days after going viral in late January 2026, and has since blown past 210,000 stars. The project was originally named Clawdbot, then Moltbot, and finally settled on OpenClaw.
At its core, OpenClaw is a personal AI assistant that runs entirely on your own devices. It operates as a local gateway connecting AI models to over 50 integrations, including WhatsApp, Telegram, Slack, Discord, Signal, and iMessage. Unlike cloud-based assistants, your data never leaves your machine. The assistant is always on, capable of browsing the web, filling out forms, running shell commands, writing and executing code, and controlling smart home devices. What sets it apart from other AI tools is its ability to write its own new skills, effectively extending its own capabilities without manual intervention.
OpenClaw has found use across developer workflow automation, personal productivity management, web scraping, browser automation, and proactive scheduling. On February 14, 2026, Steinberger announced he would be joining OpenAI, and the project would transition to an open-source foundation. Security researchers have raised valid concerns about the broad permissions the agent requires to function, and the skill repository still lacks rigorous vetting for malicious submissions, so users should be mindful of these risks when configuring their instances.
n8n is an open-source workflow automation platform that combines a visual, no-code interface with the flexibility of custom code, now enhanced with native AI capabilities. It has over 400 integrations and a self-hosted, fair-code license. This gives technical teams full control over their automation pipelines and data.
The platform stands out due to its AI-native approach. Users can incorporate large language models directly into their workflows via LangChain integration. They can build custom AI agent automations alongside traditional API calls, data transformations, and conditional logic. This bridges the gap between conventional business automation tools and cutting-edge AI agent workflows. For enterprises with strict data governance requirements, the self-hosting option is particularly valuable.
Common applications include AI-driven email triage, automated content pipelines, customer support agent flows, data enrichment workflows, and multi-step AI processing chains.
In a landscape dominated by cloud API subscriptions, Ollama took the opposite approach. It is a lightweight framework written in Go for running and managing large language models entirely on your own hardware. No data is sent to external services, and the entire experience is designed to work offline.
Ollama provides simple commands to download, run, and serve models locally, supporting Llama, Mistral, Gemma, DeepSeek, and a growing list of others. It includes desktop apps for macOS and Windows, which means even non-developers can get started with local AI. Its partnerships to support open-weight models from major research labs drove a massive surge of interest.
The project has become the backbone of the local AI movement, enabling developers to experiment with and deploy LLMs in privacy-critical or cost-sensitive environments. It pairs quite well with tools like Open WebUI to create a fully self-hosted alternative to commercial AI chat products.
AI coding tools are fast, capable, and completely context-blind. Even with rules, skills, and MCP connections, they generate code that misses your conventions, ignores past decisions, and breaks patterns. You end up paying for that gap in rework and tokens.
Unblocked changes the economics.
It builds organizational context from your code, PR history, conversations, docs, and runtime signals. It maps relationships across systems, reconciles conflicting information, respects permissions, and surfaces what matters for the task at hand. Instead of guessing, agents operate with the same understanding as experienced engineers.
You can:
Generate plans, code, and reviews that reflect how your system actually works
Reduce costly retrieval loops and tool calls by providing better context up front
Spend less time correcting outputs for code that should have been right in the first place
Langflow is a low-code platform for designing and deploying AI-powered agents and retrieval-augmented generation (RAG) workflows, built on top of the LangChain framework. It provides a drag-and-drop interface for constructing chains of prompts, tools, memory modules, and data sources, with support for all major LLMs and vector databases.
Developers can visually orchestrate multi-agent conversations, manage memory and retrieval layers, and then deploy those flows as APIs or standalone applications. This eliminates the need for extensive backend engineering when prototyping complex AI pipelines. What used to take weeks of coding can often be assembled in an afternoon.
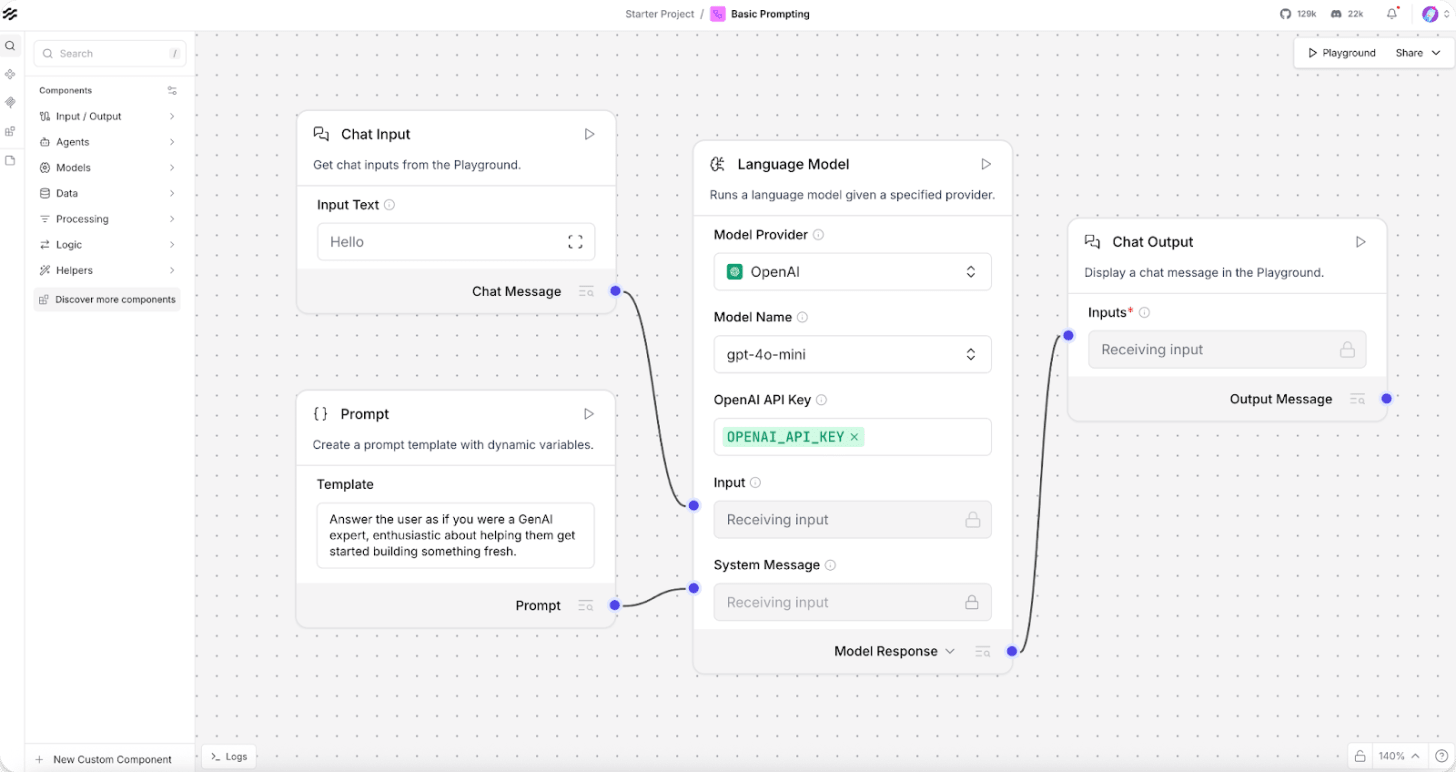
Langflow has attracted a significant community of data scientists and engineers. Its most common use cases include RAG pipeline prototyping, multi-agent conversation design, custom chatbot creation, and rapid LLM application development.
Dify is a production-ready platform for agentic workflow development, offering an all-in-one toolchain to build, deploy, and manage AI applications. Written primarily in TypeScript, it handles everything from enterprise QA bots to AI-driven custom assistants.
The platform includes a workflow builder for defining tool-using agents, built-in RAG pipeline management, support for multiple AI model providers, including OpenAI, Anthropic, and various open-source LLMs, usage monitoring, and both local and cloud deployment options. It also supports Model Context Protocol (MCP) integration. Dify handles the infrastructure boilerplate so teams can focus on crafting their agent logic.
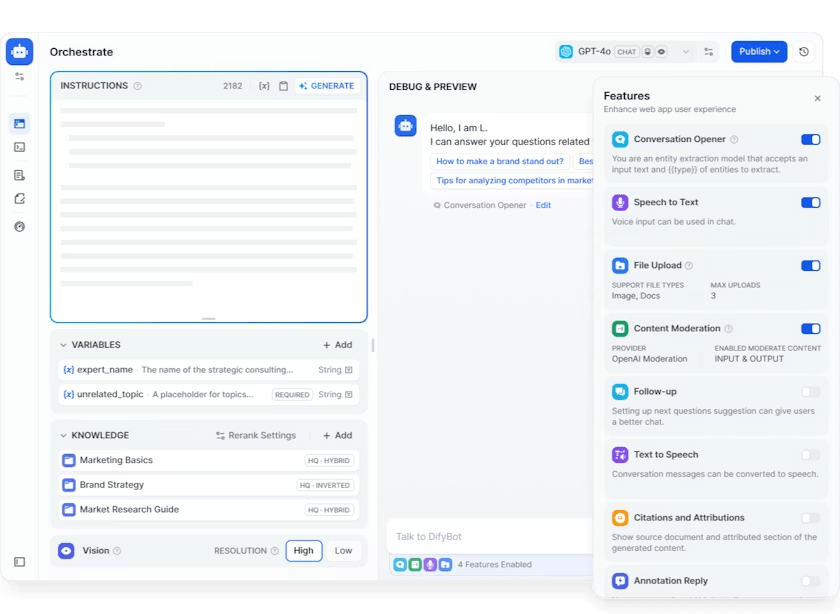
Dify fills a crucial gap for teams that want to stand up AI-powered services quickly under an open-source, self-hostable framework. Its use cases span enterprise chatbot deployment, AI-powered internal tools, customer support automation, and multi-model orchestration
LangChain has cemented its position as the foundational framework for building reliable AI agents in Python. It provides modular components for chains, agents, memory, retrieval, tool use, and multi-agent orchestration. Its companion project, LangGraph, extends this further with support for complex, stateful agent workflows that include cycles and conditional branching.
Many of the other projects on this list build on top of LangChain or integrate with it directly, making it the connective tissue of the AI agent ecosystem. It has great support from Anthropic, OpenAI, Google, and every major model provider.
Developers use LangChain for building multi-agent systems, tool-using AI agents, RAG pipelines, conversational AI applications, and structured data extraction.
Open WebUI is a self-hosted AI platform designed to operate entirely offline, with over 282 million downloads and 124k+ stars. It provides a polished, ChatGPT-style web interface that connects to Ollama, OpenAI-compatible APIs, and other LLM runners, all installable from a single pip command.
The feature set is extensive. It includes a built-in inference engine for RAG, hands-free voice and video call capabilities with multiple speech-to-text and text-to-speech providers, a model builder for creating custom agents, native Python function calling, and persistent artifact storage. For enterprise users, it offers SSO, role-based access control, and audit logs. A community marketplace of prompts, tools, and functions makes extending the platform straightforward.
If Ollama provides the engine for running local models, Open WebUI provides the interface. Together, they form a popular self-hosted AI stack. Its primary use cases include private ChatGPT replacements, multi-model comparison setups, team AI platforms, and RAG-powered document question-answering systems.
DeepSeek-V3 stunned the AI community by delivering benchmark results that rival frontier closed models like GPT-4, as a fully open-weight release.
Built on a Mixture-of-Experts (MoE) architecture, it is optimized for general-purpose reasoning and supports ultra-long 128K token contexts. The team introduced novel training techniques, including distilled reasoning chains, that set new standards in the open model community.
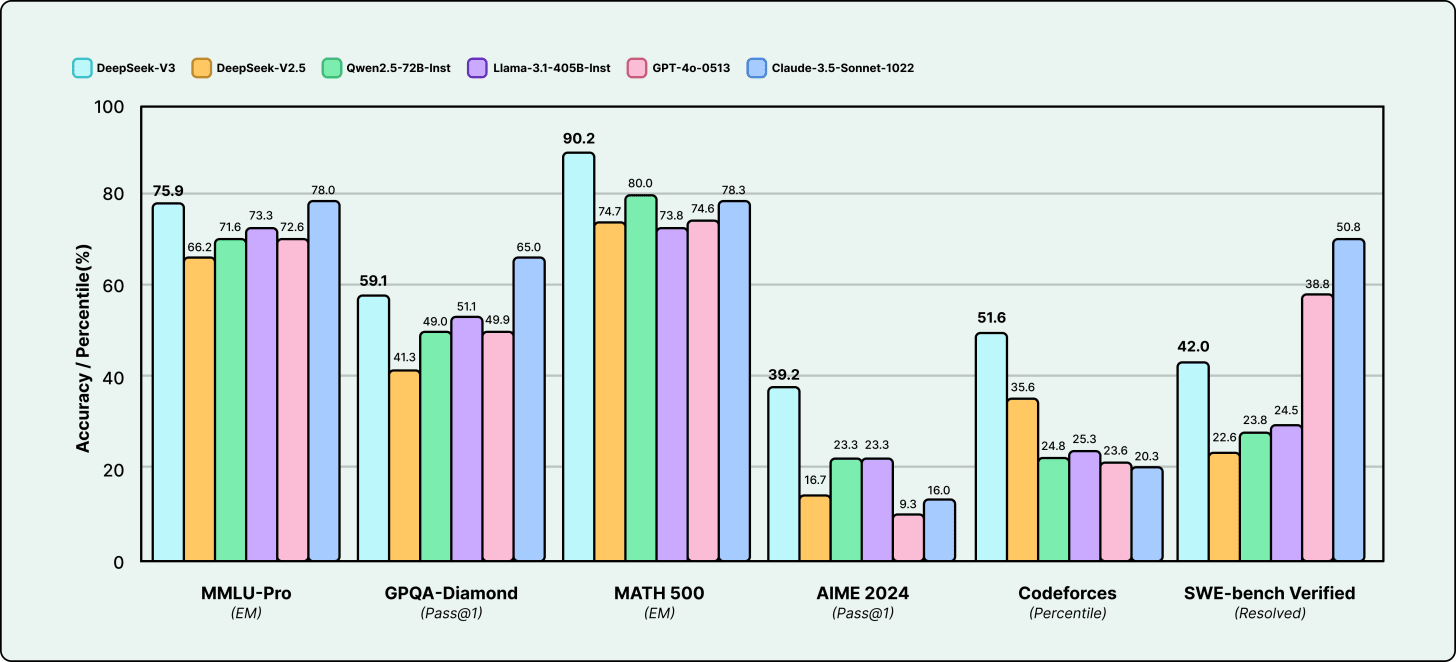
DeepSeek-V3 proved that the open-source community can produce models competitive with the best proprietary offerings. This has significant implications for developers who want high-capability AI without vendor lock-in, recurring API costs, or data privacy concerns. The model is available for free commercial use and can be fine-tuned for domain-specific applications. It runs locally via Ollama and has become a popular choice for powering custom AI agents and enterprise chatbots.
Gemini CLI is Google’s open-source contribution to the agentic coding space, bringing the Gemini multimodal model directly into developers’ terminals.
With a simple npx command, developers can chat with, instruct, and automate tasks using the Gemini model from the command line. It supports code assistance, natural language queries, integration with Google Cloud services, and can be embedded into scripts and CI/CD pipelines.
Basically, the tool abstracts away the complexity of API integration, making frontier AI capabilities immediately accessible from any terminal environment. Common uses include AI-assisted coding, command-line automation, batch file processing, and rapid prototyping.
RAGFlow is an open-source retrieval-augmented generation engine that combines advanced RAG techniques with agentic capabilities to create a robust context layer for LLMs.
The platform provides an end-to-end framework covering document ingestion, vector indexing, query planning, and tool-using agents that can invoke external APIs beyond simple text retrieval. It also supports citation tracking and multi-step reasoning, which are critical for enterprise applications where answer traceability matters.
As organizations move beyond basic chatbots toward production AI systems, RAGFlow addresses the hardest challenge: making AI answers grounded, traceable, and reliable. With 70k+ stars, it has become a key infrastructure component for enterprise knowledge bases, compliance-focused AI, research assistants, and multi-source data analysis workflows [10].
Claude Code is Anthropic’s agentic coding tool that operates from the terminal. Once installed, it understands the full codebase context and executes developer commands via natural language. You can ask it to refactor functions, explain files, generate unit tests, handle git operations, and carry out complex multi-file changes, all guided by conversation.
Claude Code distinguishes itself from simpler code completion tools via its ability to reason about an entire project, execute multi-step tasks, and maintain context across long coding sessions. It operates as an AI pair programmer that is deeply aware of your project structure and can act on code independently.
Its primary applications include full-codebase refactoring, automated test generation, code review and explanation, and git workflow automation.
Some common trends are shaping this landscape:
Ollama, Open WebUI, and OpenClaw collectively signal a massive shift: developers want to run AI on their own hardware.
Privacy concerns, API costs, and the desire for deep customization are driving this movement. The infrastructure for self-hosted AI has matured to the point where a single command can spin up a full-featured AI platform.
Nearly every repository on this list incorporates some form of autonomous agent behavior.
We have moved from AI that responds to AI that acts. Agents can now browse the web, execute code, manage files, orchestrate multi-step workflows, and even improve their own capabilities, all running continuously on your machine.
DeepSeek-V3’s success proved that open-weight models can compete with the best proprietary offerings.
Combined with efficient local runtimes like Ollama, this means developers can build high-capability applications without any API dependency. This trend is reshaping the economics of AI development fundamentally.
Langflow, Dify, and n8n show that drag-and-drop visual interfaces are becoming the preferred way to design AI agent pipelines.
This means domain experts, not just ML engineers, can create sophisticated AI applications. The barrier to entry for building production AI has never been lower.
The repositories profiled here are more than trending projects. They are the building blocks of a new AI infrastructure stack.
For developers, the takeaway is clear. Whether you are building an AI-powered product, automating internal workflows, or experimenting with frontier models, the tools in this list represent the most battle-tested, community-validated starting points available. Keep them on your radar. The pace of innovation in this space shows no signs of slowing down.
References:
OpenClaw - github.com/openclaw/openclaw
n8n - github.com/n8n-io/n8n
Ollama - github.com/ollama/ollama
Langflow - github.com/langflow-ai/langflow
Dify - github.com/langgenius/dify
LangChain - github.com/langchain-ai/langchain
Open WebUI - github.com/open-webui/open-webui
DeepSeek-V3 - github.com/deepseek-ai/DeepSeek-V3
Google Gemini CLI - github.com/google-gemini/gemini-cli
RAGFlow - github.com/infiniflow/ragflow
Claude Code - github.com/anthropics/claude-code
2026-03-08 00:31:24
If slow QA processes bottleneck you or your software engineering team and you’re releasing slower because of it — you need to check out QA Wolf.
QA Wolf’s AI-native service supports web and mobile apps, delivering 80% automated test coverage in weeks and helping teams ship 5x faster by reducing QA cycles to minutes.
QA Wolf takes testing off your plate. They can get you:
Unlimited parallel test runs for mobile and web apps
24-hour maintenance and on-demand test creation
Human-verified bug reports sent directly to your team
Zero flakes guarantee
The benefit? No more manual E2E testing. No more slow QA cycles. No more bugs reaching production.
With QA Wolf, Drata’s team of 80+ engineers achieved 4x more test cases and 86% faster QA cycles.
This week’s system design refresher:
CPU vs GPU vs TPU
How OAuth 2 Works
How Distributed Tracing Works at the High Level?
How GPUs Work at a High Level
Top 4 API Gateway Use Cases
Why does the same code run fast on a GPU, slow on a CPU, and leave both behind on a TPU? The answer is architecture. CPUs, GPUs, and TPUs are designed for different workloads.
CPU (Central Processing Unit): The CPU handles general-purpose computing. It's built for low latency and complex control flow, branching logic, system calls, interrupts, and decision-heavy code.
Operating systems, databases, and most applications run on the CPU because they need that flexibility.
GPU (Graphics Processing Unit): GPUs work differently. Instead of a few cores, they spread the work across thousands of cores that execute the same instruction across huge datasets (SIMT/SIMD-style).
If your workload is repetitive like matrix math, pixel shading, tensor operations, GPUs handle it quickly.
TPU (Tensor Processing Unit): TPUs are specialized hardware. The architecture is designed around matrix multiplication using systolic arrays, with compiler-controlled dataflow and on-chip buffers for weights and activations.
They are fast at neural network training and inference, as long as the workload fits the hardware well.
Over to you: When designing systems today, how do you decide what runs on CPU vs GPU vs specialized accelerators?
Authorization Code Flow (+ PKCE) - for user login:
User requests a protected resource
Server redirects to the Authorization Server (IdP)
Client generates a code_verifier and code_challenge (PKCE)
User authenticates and gives consent
IdP returns an authorization code
Server exchanges the code (with the verifier) for tokens
Server validates tokens and creates a session
PKCE prevents intercepted authorization codes from being reused. That’s why it’s the modern default for web and mobile apps.
Client Credentials Flow - for service-to-service:
A service requests an access token
The IdP authenticates the client
It issues a token
The service calls the API using a Bearer token
No user. Just machine identity.
Services generate telemetry data (traces, logs, metrics) as they handle requests.
The OpenTelemetry Collector receives this data from all services in a unified format.
The collector splits the data into three streams: traces, logs, and metrics.
Each stream is sent to a Receive & Process unit that prepares it for storage and analysis.
Processed data is stored in a Log Database for querying and long-term access.
Data from the database is visualized through a Visualization dashboard for monitoring and debugging.
Over to you: What else will you add to better understand distributed tracing?
When people say GPUs are powerful, what they really mean is this: GPUs are built for massive parallelism from the ground up.
Let’s break down what’s happening under the hood.
At the top level, a GPU chip is made up of many Streaming Multiprocessors (SMs). Think of SMs as mini parallel engines replicated across the chip. Instead of one big brain, you get dozens of smaller ones working simultaneously.
Inside each SM:
A Warp Scheduler decides which group of threads (a warp) runs next.
Dozens of CUDA Cores execute instructions in parallel.
A Register File stores thread-local data at ultra-low latency.
Load/Store units move data between registers and memory.
Texture units handle specialized memory operations.
L1 Cache provides fast, on-SM data access.
Each SM works independently, but they’re connected through an on-chip interconnect. Below that sits the L2 Cache, shared across all SMs. This is the coordination layer. If one SM misses in L1, it checks L2 before going to global memory.
Then come the Memory Controllers, which interface with Global Memory. This is where things get interesting:
Extremely high bandwidth
Much higher latency than on-chip memory
That’s why GPUs rely on massive parallelism. While some threads wait on memory, thousands of others keep executing.
An API Gateway sits between your clients and your services, and it does a lot more than just routing. Here are four use cases where it actually matters:
Handling Traffic Spikes: Without rate limiting, one misbehaving client can take down your entire system. The API Gateway enforces rate limits based on policies you define, such as per user, per IP, per subscription tier and so on. Exceed the limit? You get a 429 Too Many Requests.
Your backend services never even see that traffic. They stay healthy while the gateway takes the hit.
Securing Public APIs: Every request hits the gateway first. It checks the bearer token, validates it against the Identity Provider (IdP), and makes the access decision right there. No need to duplicate auth logic across every microservice. The gateway handles AuthN and AuthZ in one place.
Reducing Client-Server Roundtrips: A dashboard page might need user data, order history, and payment info. Without a gateway, the client makes three separate calls. With request aggregation, the client sends one GET /dashboard request. The gateway fans out to user-service, order-service, and payment-service internally, then combines everything into a single JSON response back to the client.
Supporting Multiple Clients: Web and mobile apps don't need the same data. A web client might call GET /v2/home and get a rich payload with full details. A mobile client hits GET /v1/home and gets a lighter response that doesn't burn through data.
The gateway handles versioning and payload transformation so your backend services don't need to know which client is calling.
Over to you: Are you running an API gateway in production? What's the biggest win it gave you?
2026-03-06 00:30:58
When we build software systems, one of the most important goals is making sure they can handle large amounts of work efficiently.
High-throughput systems are capable of processing vast quantities of data or transactions in a given timeframe. Throughput refers to the amount of work a system completes in a specific time period. For example, a web server might process 10K requests per second, or a database might handle 50K transactions per minute. The higher the throughput, the more work gets done in the same amount of time.
Throughput is different from latency. Latency measures how long it takes to complete a single operation, from start to finish. While throughput measures the volume of operations the system handles over time. For example, a system can have low latency but low throughput if it processes each request quickly but can only handle a few at once. Conversely, a system might have high throughput but high latency if it processes many requests simultaneously, but each request takes longer to complete.
There is often a tradeoff between these two metrics. When we batch multiple operations together, we increase throughput because the system processes many items at once. However, this batching introduces waiting time for individual operations, which increases latency. Similarly, processing every request immediately reduces latency but may limit throughput if the system becomes overwhelmed.
In this article, we will go through the fundamental concepts and practical strategies for building systems that can handle high volumes of work without breaking down under pressure.
2026-03-05 00:30:49
Building with LangChain agents is easy. Running them reliably in production is not. As agent workflows grow in complexity, you need visibility, fault tolerance, retries, scalability, and human oversight. Orkes Conductor provides a durable orchestration layer that manages multi agent workflows with state management, error handling, observability, and enterprise grade reliability. Instead of stitching together fragile logic, you can coordinate agents, tools, APIs, and human tasks through a resilient workflow engine built for scale. Learn how to move from experimental agents to production ready systems with structured orchestration.
2026 has already started strong. In January alone, Moonshot AI open-sourced Kimi K2.5, a trillion-parameter model built for multimodal agent workflows. Alibaba shipped Qwen3-Coder-Next, an efficient coding model designed for agentic coding. OpenAI launched a macOS app for its Codex coding assistant. These are recent moves in trends that have been building for months.
This article covers five key trends that will likely shape how teams build with AI this year.
Early language models like GPT-4 generated answers directly. You asked a question, and the model started producing text token by token. This works for simple tasks, but it often fails on harder problems where the first attempt is wrong, like advanced math or multi-step logic.
Newer models, starting with OpenAI’s o1, changed this by spending time “thinking” before answering. Instead of jumping straight to the final response, they generate intermediate steps and then produce the answer. The model spends more time and computing power, but it can solve much harder problems in logic and multi-step planning.
After o1, many teams focused on training reasoning models. By early 2026, most major AI labs had either released a reasoning model or added reasoning to its main product.
A key method that made model training practical at scale was Reinforcement Learning with Verifiable Rewards (RLVR). Although first introduced by AI2’s Tülu 3, DeepSeek-R1 brought the approach to mainstream attention by applying it at scale. To understand how RLVR improves on previous methods, it helps to look at the standard training pipeline.
LLM training has two main stages: pre-training and post-training. During post-training, a Reinforcement Learning (RL) algorithm lets the model practice. The model generates responses, and the algorithm updates its weights so better responses become more likely over time.
To decide which responses are better, AI labs traditionally trained a separate reward model as a proxy for human preferences. This involved collecting preference data from humans, training the reward model on that data, and using it to guide the LLM. This approach is known as Reinforcement Learning from Human Feedback (RLHF).
RLHF creates a bottleneck. It depends on humans labeling data, which is slow and expensive at large scale. It also gets harder when the task is complex, because people cannot reliably judge long reasoning traces.
RLVR removes this bottleneck. It still uses reinforcement learning, but the reward comes from checking correctness instead of predicting what a human would prefer. In domains like math or coding, many tasks have answers that can be checked automatically. The system checks if the code runs or if the math solution matches the ground truth. If it does, the model gets a reward. No separate reward model is needed.
RLVR enables scalable training because correctness checks can run quickly and automatically. The model can practice on millions of problems with immediate feedback. DeepSeek-R1 showed that this approach could reach frontier-level reasoning, shifting the main bottleneck from human labeling to available compute.
Today, most major AI labs use reasoning in training, and many use RLVR. As a result, reasoning alone is no longer a differentiator. The focus has shifted to efficiency.
AI teams are now working on adaptive reasoning, where the model adjusts its effort based on how hard a prompt is. Instead of spending many tokens on a simple greeting, models reserve deep thinking for problems that actually need it. Gemini 3 is a concrete example. It supports a thinking_level control and uses dynamic thinking by default, so it can vary how much reasoning it applies across prompts. This focus on efficiency will make reasoning models practical for real-world use cases where speed and cost matter.
Early language models were good at generating text, but they could not take actions. If you asked a model to book a flight, it could describe the steps but could not use a booking system. And because it could not check the real world, it often guessed. If you asked “Is the restaurant open right now?”, it might answer from old information instead of checking live hours.
These limits led to the rise of AI agents. An agent combines an LLM with tools and runs it in a loop, allowing it to plan and act. Instead of directly generating the final answer, an agent can take a goal, break it into steps, run tools, and use the results to decide what to do next.
Most agents share the same structure. A language model interprets the request and picks the next step. Tools connect the model to external systems like search, calendars, files, or APIs. A loop runs actions, inspects results, and retries or changes course when something fails.
Agents are no longer experimental. They are shipping in real products. OpenAI’s ChatGPT agent can browse the web and complete tasks on your behalf. Anthropic’s Claude can use tools, write and run code, and work through multi-step problems.
Three developments made this possible. First, reasoning improved. Models got better at planning multi-step work, keeping track of intermediate results, and choosing the next action instead of jumping to a final answer.
Second, tool connections became easier. In the past, every tool integration was custom. Protocols like Anthropic’s Model Context Protocol (MCP) reduced the friction of connecting models to external systems. Adding a new tool now takes just a few lines of code.
Third, frameworks like LangChain and LlamaIndex matured. They made it easier to build agents without starting from scratch. They provide ready-made components for tool use, multi-step flows, and logging. This lowered the barrier and let more teams experiment with agents.
from langchain_ollama import ChatOllama
from langchain.agents import create_agent
# Create an LLM instance
llm = ChatOllama(model=“gemma3:1b”)
# Create your tool list
tools = [get_weather, web_search]
# Create your agent
agent = create_agent(llm, tools)
# Call your agent using agent.invoke
agent.invoke({”messages”:
[{”role”: “user”, “content”: “Events in SF”}]
})Agents are good at short workflows, but they still struggle when tasks run long. Over dozens of steps, they can lose context and make mistakes that compound. They are also limited by default access. Many agents run in sandboxed environments and cannot see your email, files, or local apps unless you connect them.
A likely trend in 2026 is persistent agents that address both problems. These are always-on assistants designed to handle longer workflows over extended periods. Many will run locally, making it easier to connect with your files, apps, and system settings while keeping data under your control. OpenClaw is an early example of this shift toward personal agents that run on your own hardware.

More access also increases risk. When agents can read personal data and take actions, mistakes matter more. So a major focus in 2026 will be reliability and security. Reliability means staying on track, recovering from errors, and behaving predictably over long tasks. Security means protecting data, resisting prompt injection, and avoiding irreversible actions without explicit approval.
AI started helping software engineers with simple autocomplete. But the capability was limited. The model could only see the immediate area around your cursor, maybe a few lines before and after. It did not understand the full codebase, the project structure, or what you were trying to build.
That changed when AI labs applied the agent approach to coding. Rather than relying on general-purpose models, they trained specialized LLMs through extensive fine-tuning on code repositories, documentation, and programming patterns. They also replaced generic tools with coding-specific ones like read_file, search_codebase, edit_file, run_terminal_command, and execute_tests.
The result is a model that understands software engineering practices like project structure, dependencies, and debugging, and knows how to use its tools to complete tasks. When you give it a complex task, it decides which tools to call and in what order to finish the job.
Powerful proprietary coding agents like Anthropic’s Claude Code and OpenAI’s Codex are driving this shift. They can read an entire repository and understand complex project structures. At the same time, open-source models have narrowed the gap. Qwen3-Coder-Next, an 80B-parameter model released in early 2026, reached performance close to top closed models while running locally on consumer hardware.
Coding agents are one of the most visible places where AI has already changed day-to-day work. Engineers can ask for repo-level fixes and improvements and get working patches much faster. These tools also lowered the barrier to entry. People with less coding experience can build working apps using services built on top of these agents, like Replit and Lovable.
The baseline for coding agents is no longer just writing code. It is managing software at scale. Three areas will likely see the most progress.
Deeper repository-level understanding. Current agents sometimes lose track of how files relate to each other in large codebases. Better tracking of dependencies, architecture, and cross-file context will let agents handle bigger and more complex projects reliably.
Security-aware coding. As agents write more production code, catching vulnerabilities before they ship becomes critical. Expect agents to build security scanning and automated test generation directly into their workflow, rather than treating them as separate steps.
Faster completions. Today’s agents can be slow on complex tasks, sometimes taking minutes to plan and execute a multi-file change. AI labs are actively working on reducing the time from request to working code, making agents practical for more real-time development work.
For the first few years of the LLM era, the most capable models were closed. If you wanted top performance, you used APIs from labs like OpenAI, Anthropic, or Google. You could not access the weights, run models locally, or fine-tune them. Open-weight models existed but they lagged behind.
That gap did not last long. It narrowed faster than most people expected in two phases: a defining DeepSeek moment, followed by rapid momentum.
In January 2025, DeepSeek released DeepSeek-R1 and open-sourced its weights, code, and training approach. The reasoning model matched or exceeded closed competitors on key benchmarks. It showed that frontier-level reasoning did not require a proprietary API. People started calling similar breakthroughs a “DeepSeek moment.”
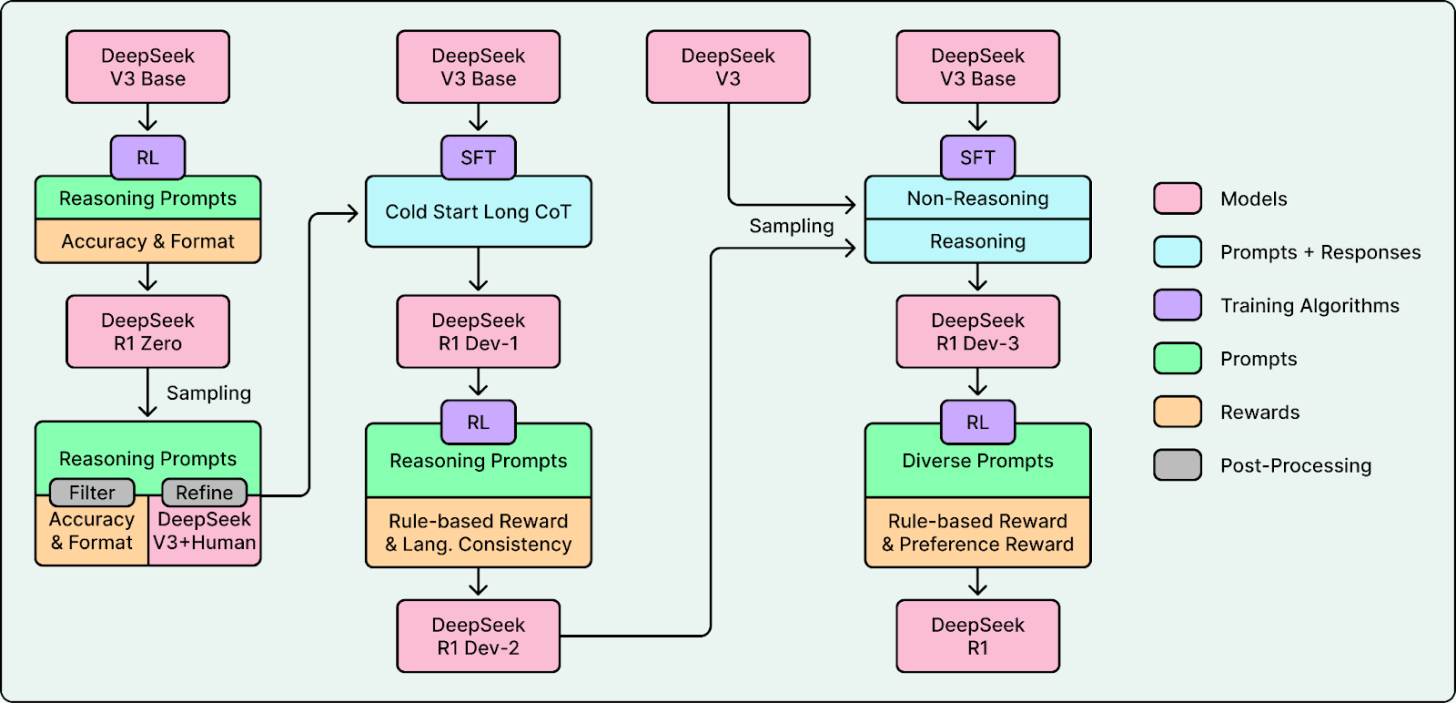
A key reason R1 stood out was its training approach. Before this, many chatbots leaned heavily on RLHF during post-training, the approach popularized by early ChatGPT. DeepSeek leaned heavily on RLVR, which scales better on verifiable tasks like math and coding. That made it easier to train reasoning ability with much less human labeling.
After that, more labs released full weights and training details. Alibaba’s Qwen family became a major base for open development. GLM from Z.ai pushed multilingual and multimodal capability into the open ecosystem. Moonshot’s Kimi family shipped strong agentic and tool-use features. With this momentum, more teams entered and the open-weight ecosystem got much stronger.

In August 2025, OpenAI released gpt-oss, its first open-weight models since GPT-2. The release included 120B and 20B parameter models under the Apache 2.0 license. Mistral, Meta, and the Allen Institute also shipped competitive releases.
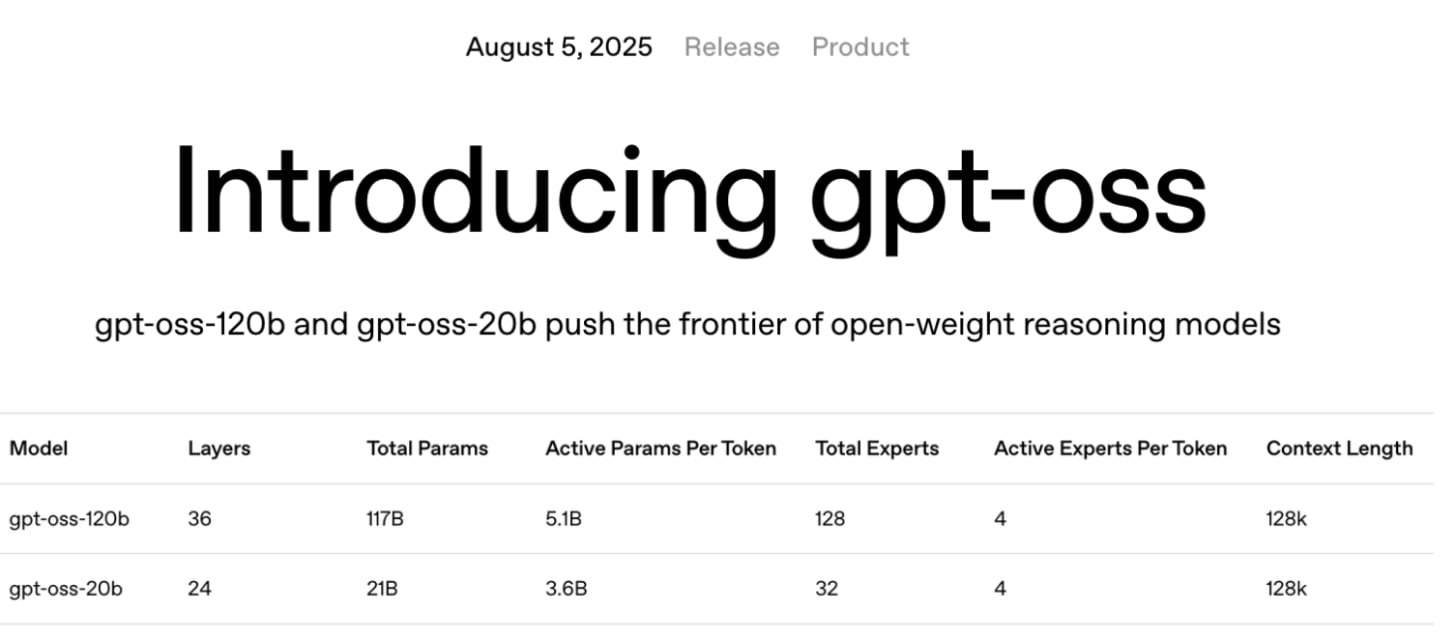
With detailed technical reports and working recipes, techniques spread quickly. Teams replicated results, improved them, and shipped variants. Today, open-weight models are close to top closed models on many standard benchmarks.
In 2026, open-weight releases are no longer surprising. The next wave of progress will focus less on scale and more on efficiency, practical deployment, and agent capabilities.
Architectural Efficiency. Architectures are getting more efficient, often using sparse MoE designs plus long context so only a small part of the model is active per token. Qwen3-Coder-Next is one example, with an ultra-sparse setup and a 256k native context window.
Agent Readiness. Open-weight models are being trained for agent use, not just chat. Tool use, structured outputs, and long-context reasoning are designed in from the start. As agents become central to how AI delivers value, agent-ready open-weight models will power more autonomous workflows.
Easier deployment. Lower barriers to running these models are emerging through new inference formats and compression techniques. Hardware vendors are also stepping up with direct support for open-weight models at launch, treating them as first-class deployment targets.
Most early chatbots were text-in, text-out. Even as they improved, they stayed text-centric. Images, audio, and video were often handled by separate systems. Early image generators could produce striking visuals, but results were inconsistent and hard to control.
This changed in two ways: chatbots became natively multimodal, and generation models improved dramatically.
The era of text-only models ended as leading models became natively multimodal. Gemini 3 and ChatGPT-5 can handle text and images in a single system, and their products also support richer media interactions. On the open-weight side, Qwen2.5-VL shows similar vision-language capability with strong visual understanding across modalities.
This unified approach enables more natural interactions and new use cases. For example, you can upload a diagram, ask questions about specific elements, and get answers that reference visual details, all within one conversation.
Image and video generation also improved, moving from demos to real tools. OpenAI’s Sora 2 showed video generation at a level that forced the industry to take it seriously. Google’s Veo 3.1, released in October 2025 and updated in January 2026, pushed video generation with richer audio and stronger editing controls like object insertion. Nano Banana Pro (Gemini 3 Pro Image), launched in November 2025, improved image generation and editing, especially text rendering and control.
Two trends will likely define the next phase of multimodal progress: physical AI and world models.
Physical AI like robots are moving from research into real deployments. CES 2026 featured a wave of humanoid robot demos across many companies. Boston Dynamics unveiled its electric Atlas and announced a partnership with Google DeepMind to integrate Gemini Robotics models. Tesla has also said it plans to ramp Optimus, targeting very high production over time.

These systems combine vision-language understanding, reinforcement learning, and planning. As Jensen Huang put it around CES 2026, “The ChatGPT moment for robotics is here,” pointing to physical AI models that can understand the real world and plan actions.
The video generation systems described above are learning something deeper than how to produce realistic pixels. They are building basic models of how the physical world works, systems that can simulate physics, predict outcomes, and reason about the real world.
In November 2025, Yann LeCun left Meta to launch AMI Labs, raising €500M to build AI systems that understand physics rather than just predicting text. Google DeepMind released Genie 3, the first real-time interactive world model generating persistent 3D environments. NVIDIA’s Cosmos Predict 2.5, trained on 200 million curated video clips, unifies text-to-world, image-to-world, and video-to-world generation for training robots and autonomous vehicles in simulated environments.

Training better world models will likely continue through 2026. If models can simulate environments reliably, they become a foundation for training robots, autonomous vehicles, and other systems that must operate in the physical world. Video generation, robotics, and simulation are starting to converge into one direction. 2026 will show whether that convergence accelerates or stalls.
2026 will not be defined by a single breakthrough. It will be shaped by capabilities that now exist together and reinforce each other. These capabilities are already combining to enable new workflows, from autonomous code refactoring to robots learning tasks through simulated environments. It will be an interesting year to watch.
2026-03-04 00:30:27
Start reading the latest version of the book everyone is talking about.
The second edition of Designing Data-Intensive Applications was just published – with significant revisions for AI and cloud-native!
Martin Kleppmann and Chris Riccomini help you navigate the options and tradeoffs for processing and storing data for data-intensive applications. Whether you’re exploring how to design data-intensive applications from the ground up or looking to optimize an existing real-time system, this guide will help you make the right choices for your application.
Peer under the hood of the systems you already use, and learn how to use and operate them more effectively
Make informed decisions by identifying the strengths and weaknesses of different approaches and technologies
Understand the distributed systems research upon which modern databases are built
Go behind the scenes of major online services and learn from their architectures
We’re offering 3 complete chapters. Start reading it today.
Agoda generates and processes millions of financial data points (sales, costs, revenue, and margins) every day.
These metrics are fundamental to daily operations, reconciliation, general ledger activities, financial planning, and strategic evaluation. They not only enable Agoda to predict and assess financial outcomes but also provide a comprehensive view of the company’s overall financial health.
Given the sheer volume of data and the diverse requirements of different teams, the Data Engineering, Business Intelligence, and Data Analysis teams each developed their own data pipelines to meet their specific demands. The appeal of separate data pipeline architectures lies in their simplicity, clear ownership boundaries, and ease of development.
However, Agoda soon discovered that maintaining separate financial data pipelines, each with its own logic and definitions, could introduce discrepancies and inconsistencies that could impact the company’s financial statements. In other words, there is no single source of truth, which is not a good situation for financial data.
In this article, we will look at how the Agoda engineering team built a single source of truth for its financial data and the challenges encountered.
Disclaimer: This post is based on publicly shared details from the Agoda Engineering Team. Please comment if you notice any inaccuracies.
A data pipeline is an automated system that extracts data from source systems, transforms it according to business rules, and loads it into databases where analysts can use it.
The high-level architecture of multiple data pipelines, each owned by different teams, introduced several fundamental problems that affected both data quality and operational efficiency.
First, duplicate sources became a significant issue. Many pipelines pulled data from the same upstream systems independently. This led to redundant processing, synchronization issues, data mismatches, and increased maintenance overhead. When three different teams all read from the same booking database but at slightly different times or with different queries, this wastes computational resources and can lead to scenarios where teams are looking at slightly different versions of the same underlying data.
Second, inconsistent definitions and transformations created confusion across the organization. Each team applied its own logic and assumptions to the same data sources. As a result, financial metrics could differ depending on which pipeline produced them. For instance, the Finance team might calculate revenue differently from the Analytics team, leading to conflicting reports when executives ask fundamental questions about business performance. This undermined data reliability and created a lack of trust in the numbers.
Third, the lack of centralized monitoring and quality control resulted in inconsistent practices across teams. The absence of a unified system for tracking pipeline health and enforcing data standards meant that each team implemented its own quality checks. This resulted in duplicated effort, inconsistent practices, and delays in identifying and resolving issues. When problems did occur, it was difficult to determine which pipeline was the source of the issue.
See the diagram below:
During a recent review, Agoda observed that differences in data handling and transformation across these pipelines led to inconsistencies in reporting, as well as operational delays.
AI coding tools are fast, capable, and completely context-blind. Even with rules, skills, and MCP connections, they generate code that misses your conventions, ignores past decisions, and breaks patterns. You end up paying for that gap in rework and tokens.
Unblocked changes the economics.
It builds organizational context from your code, PR history, conversations, docs, and runtime signals. It maps relationships across systems, reconciles conflicting information, respects permissions, and surfaces what matters for the task at hand. Instead of guessing, agents operate with the same understanding as experienced engineers.
You can:
Generate plans, code, and reviews that reflect how your system actually works
Reduce costly retrieval loops and tool calls by providing better context up front
Spend less time correcting outputs for code that should have been right in the first place
To overcome these challenges, Agoda developed a centralized financial data pipeline known as FINUDP, which stands for Financial Unified Data Pipeline.
This system delivers both high data availability and data quality. Built on Apache Spark, FINUDP processes all financial data from millions of bookings each day. It makes this data reliably available to downstream teams for reconciliation, ledger, and financial activities.
The architecture consists of several key components.
Source tables contain raw data from upstream systems such as bookings and payments.
The execution layer is where the actual data processing happens, running on Apache Spark for distributed computing power. This layer sends email and Slack alerts when jobs fail and uses an internally developed tool called GoFresh to monitor if data is updated on schedule.
The data lake is where processed data is stored, with validation mechanisms ensuring data quality.
Finally, downstream teams (including Finance, Planning, and Ledger teams) consume the data for their specific needs.
See the diagram below:
For this centralized pipeline, three non-functional requirements stood out.
Data freshness: The pipeline is designed to update data every hour, aligned with strict service level agreements for downstream consumers. To ensure these targets are never missed, Agoda uses GoFresh, which monitors table update timestamps. If an update is delayed, the system flags it, prompting immediate action to prevent any breaches of these agreements.
Reliability: Data quality checks run automatically as soon as new data lands in a table. A suite of automated validation checks investigates each column against predefined rules. Any violation triggers an alert, stopping the pipeline and allowing the team to address data issues before they cascade downstream.
Maintainability: Each change begins with a strong, peer-reviewed design. Code reviews are mandatory, and all changes undergo shadow testing, which runs on real data in a non-production environment for comparison.
Agoda implemented several technical practices to ensure the reliability of FINUDP. Understanding these practices provides insight into how production-grade data systems are built and maintained.
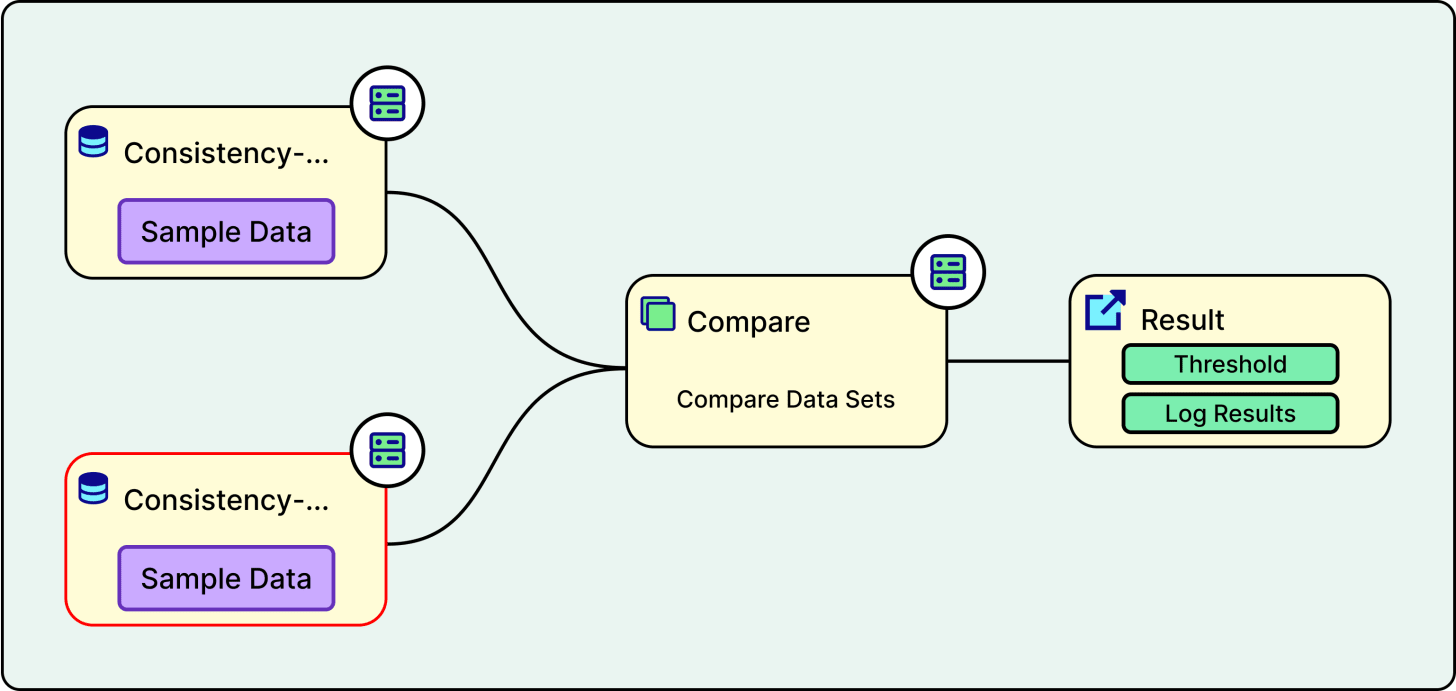
Shadow testing is one of the most important practices. When a developer makes a change to the pipeline code, the system runs both the old version and the new version on the same production data in a test environment. The outputs from both versions are then compared, and a summary of the differences is shared directly within the code review process. This provides reviewers with clear visibility into the impact of proposed changes on the data. It is an excellent way to catch unexpected side effects before they reach production.
See the diagram below:
The staging environment serves as a safety net between development and production. It closely mirrors the production setup, allowing Agoda to test new features, pipeline logic, schema changes, and data transformations in a controlled setting before releasing them to all users. By running the full pipeline with realistic data in staging, the team can identify and resolve issues such as data quality problems, integration errors, or performance bottlenecks without risking the integrity of production data. This approach reduces the likelihood of unexpected failures and builds confidence that every change has been thoroughly validated before going live.
Proactive monitoring for data reliability includes several mechanisms.
Daily snapshots are taken to preserve historical states of the data.
Partition count checks ensure that all expected data partitions are present. A partition is a way of dividing large tables into smaller chunks, typically by date, so queries only need to scan relevant portions of the data.
Automated alerts detect spikes in corrupted data, ensuring that row counts align with expectations.
The multi-level alerting system ensures that failures are caught quickly and the right people are notified:
Email alerts are the first level, where any pipeline failure triggers an email to developers via the coordinator, enabling quick awareness and response.
Slack alerts form the second level, where a dedicated backend service monitors all running jobs and sends notifications about successes or failures directly to the development team’s Slack channels, categorized by hourly and daily frequency.
The third level involves GoFresh continuously checking the freshness of specific columns in target tables. If data is not updated within a predetermined timeframe, GoFresh notifies the Network Operations Center, a 24/7 support team that monitors all critical Agoda alerts, notifies the correct team, and coordinates emergency response sessions.
Data integrity is verified using a third-party data quality tool called Quilliup. Agoda executes predefined test cases that utilize SQL queries to compare data in target tables with their respective source tables. Quilliup measures the variation between source and target data and alerts the team if the difference exceeds a set threshold. This ensures consistency between the original data and its downstream representation.
Data contracts establish formal agreements with upstream teams that provide source data. These contracts define required data rules and structure. If incoming source data violates the contract, the source team is immediately alerted and asked to resolve the issue. There are two types of data contracts.
Detection contracts monitor real production data and alert when violations occur.
Preventative contracts are integrated into the continuous integration pipelines of upstream data producers, catching issues before data is even published.
Lastly, anomaly detection utilizes machine learning models to monitor data patterns and identify unusual fluctuations or spikes in the data. When anomalies are detected, the team investigates the root cause and provides feedback to improve model accuracy, distinguishing between valid alerts and false positives.
Throughout the journey of building FINUDP and migrating multiple data pipelines into one, Agoda encountered several key challenges:
Stakeholder management proved to be more complex than anticipated. Centralizing multiple data pipelines into a single platform meant that each output still served its own set of downstream consumers. This created a broad and diverse stakeholder landscape across product, finance, and engineering teams.
Performance issues emerged as a significant technical challenge. Bringing together several large pipelines and consolidating high-volume datasets into FINUDP initially incurred a performance cost. The end-to-end runtime was approximately five hours, which was far from ideal for daily financial reporting. Through a series of optimization cycles covering query tuning, partitioning strategy, pipeline orchestration, and infrastructure adjustments, Agoda was able to reduce the runtime from five hours to approximately 30 minutes.
Data inconsistency was perhaps the most conceptually challenging problem. Each legacy pipeline had evolved with its own set of assumptions, business rules, and data definitions. When these were merged into FINUDP, those differences surfaced as data inconsistencies and mismatches. To address this, Agoda went back to first principles. The team documented the intended meaning of each key metric and field, conducted detailed gap analyses comparing the outputs of different pipelines, and facilitated workshops with stakeholders to agree on a single definition for each dataset.
Centralizing data pipelines came with clear benefits but also required navigating key trade-offs between competing priorities:
The most significant trade-off involved velocity. In the previous decentralized approach, independent small datasets could move through their separate pipelines without waiting on each other. With the centralized setup, Agoda established data dependencies to ensure that all upstream datasets are ready before proceeding with the entire data pipeline.
Data quality requirements also affected development speed. Since the unified pipeline includes multiple data sources and components, changes to any component require testing and a data quality check of the whole pipeline. This causes a slowness in velocity, but it is a trade-off accepted in exchange for the numerous benefits of having a unified pipeline, including consistency, reliability, and a single source of truth.
Data governance became more rigorous and time-consuming. Migrating to a single pipeline required that every transformation be meticulously documented and reviewed. Since financial data is at stake, full alignment and approval from all stakeholders are needed before changing upstream processes. The need for thorough vetting and consensus slowed implementation, but ultimately built a foundation for trust and integrity in the new unified system. In essence, centralization increases reliability and transparency, but it demands tighter coordination and careful change management at every step.
Consolidating financial data pipelines at Agoda has made a real difference in how the company handles and trusts its financial metrics.
Through FINUDP, Agoda has established a single source of truth for all financial metrics. By introducing centralized monitoring, automated testing, and robust data quality checks, the team has significantly improved both the reliability and availability of data. This setup means downstream teams always have access to accurate and consistent information.
Last year, the data pipeline achieved 95.6% uptime (with a goal to reach 99.5% data availability). Maintaining such high data standards is always a work in progress, but with these systems in place, Agoda is better equipped to catch issues early and collaborate across teams.
References:
2026-03-03 00:30:50
npx workos launches an AI agent, powered by Claude, that reads your project, detects your framework, and writes a complete auth integration directly into your existing codebase. It’s not a template generator. It reads your code, understands your stack, and writes an integration that fits.
The WorkOS agent then typechecks and builds, feeding any errors back to itself to fix.
In December 2024, DeepSeek released V3 with the claim that they had trained a frontier-class model for $5.576 million. They used an attention mechanism called Multi-Head Latent Attention that slashed memory usage. An expert routing strategy avoided the usual performance penalty. Aggressive FP8 training cuts costs further.
Within months, Moonshot AI’s Kimi K2 team openly adopted DeepSeek’s architecture as their starting point, scaled it to a trillion parameters, invented a new optimizer to solve a training stability challenge that emerged at that scale, and competed with it across major benchmarks.
Then, in February 2026, Zhipu AI’s GLM-5 integrated DeepSeek’s sparse attention mechanism into their own design while contributing a novel reinforcement learning framework.
This is how the open-weight ecosystem actually works: teams build on each other’s innovations in public, and the pace of progress compounds. To understand why, you need to look at the architecture.
In this article, we will cover various open-source models and the engineering bets that define each one.
Every major open-weight LLM released at the frontier in 2025 and 2026 uses a Mixture-of-Experts (MoE) transformer architecture.
See the diagram below that shows the concept of the MoE architecture:
The reason is that dense transformers activate all parameters for every token. To make a denser model smarter, if you add more parameters, the computational cost scales linearly. With hundreds of billions of parameters, this becomes prohibitive.
MoE solves this by replacing the monolithic feed-forward layer in each transformer block with multiple smaller “expert” networks and a learned router that decides which experts handle each token. This result is a model that can, for example, store the knowledge of 671 billion parameters but only compute 37 billion per token.
This is why two numbers matter for every model:
Total parameters (memory footprint, knowledge capacity)
Active parameters (inference speed, per-token cost).
Think of a specialist hospital with 384 doctors on staff, but only 8 in the room for any given patient. You benefit from the knowledge of 384 specialists while only paying for 8 at a time. The triage nurse (the router) decides who gets called.
That’s also why a trillion-parameter model and a 235-billion-parameter model cost roughly the same per query. For example, Kimi K2 activates 32 billion parameters per token, while Qwen3 activates 22 billion. In other words, you’re comparing the active counts, not the totals.
Take your meeting context to new places
If you’re already using Claude or ChatGPT for complex work, you know the drill: you feed it research docs, spreadsheets, project briefs... and then manually copy-paste meeting notes to give it the full picture.
What if your AI could just access your meeting context automatically?
Granola’s new Model Context Protocol (MCP) integration connects your meeting notes to your AI app of choice.
Ask Claude to review last week’s client meetings and update your CRM. Have ChatGPT extract tasks from multiple conversations and organize them in Linear. Turn meeting insights into automated workflows without missing a beat.
Perfect for engineers, PMs, and operators who want their AI to actually understand their work.
-> Try the MCP integration for free here or use the code BYTEBYTEGO
Almost every model marketed as “open source” is technically open weight. This means that the trained parameters are public, but the training data and often the full training code are not. In traditional software, however, “open source” means code is available, modifiable, and redistributable.
What does this mean in practice?
You can download, fine-tune, and commercially deploy all six of these models. However, you cannot see or audit their training data, and you cannot reproduce their training runs from scratch. For most engineering teams, the first part is what matters. But the distinction is worth knowing.
The license landscape also varies. DeepSeek V3 and GLM-5 use the MIT license. Qwen3 and Mistral Large 3 use Apache 2.0. Both are fully permissive for commercial use. Kimi K2 uses a modified MIT license. Llama 4 uses a custom community license that restricts usage for companies with over 700 million monthly users and prohibits using the model to train competing models.
Transparency also varies. Some teams publish detailed technical reports with architecture diagrams, ablation studies, and hyperparameters. Others provide weights and a blog post with less architectural detail. More transparency enables the “borrow and build” dynamic described above, which is part of why it works.
Every time a model generates a token, it needs to “remember” keys and values for all previous tokens in the conversation. This storage, called the KV-cache, grows linearly with sequence length and becomes a memory bottleneck for long contexts. Different models use three different strategies to deal with it.
Grouped-Query Attention (GQA) shares key-value pairs across groups of query heads. It’s the industry default, offering straightforward implementation and moderate memory savings. Qwen3 and Llama 4 both use GQA.
Multi-Head Latent Attention (MLA) compresses key-value pairs into a low-dimensional latent space before caching, then decompresses when needed. It was introduced in DeepSeek V2 and used in both DeepSeek V3 and Kimi K2. MLA saves more memory than GQA but adds computational overhead for the compress/decompress step.
Sparse Attention skips attending to all previous tokens and instead selects the most relevant ones. DeepSeek introduced DeepSeek Sparse Attention (DSA) in V3.2, and GLM-5 openly adopted DSA in its architecture. Since sparse attention optimizes the attention layers while MoE optimizes the feed-forward layers, the two techniques compound. Therefore, GLM-5 benefits from both.
See the diagram below that shows DeepSeek’s Multi-Head Latent Attention approach:
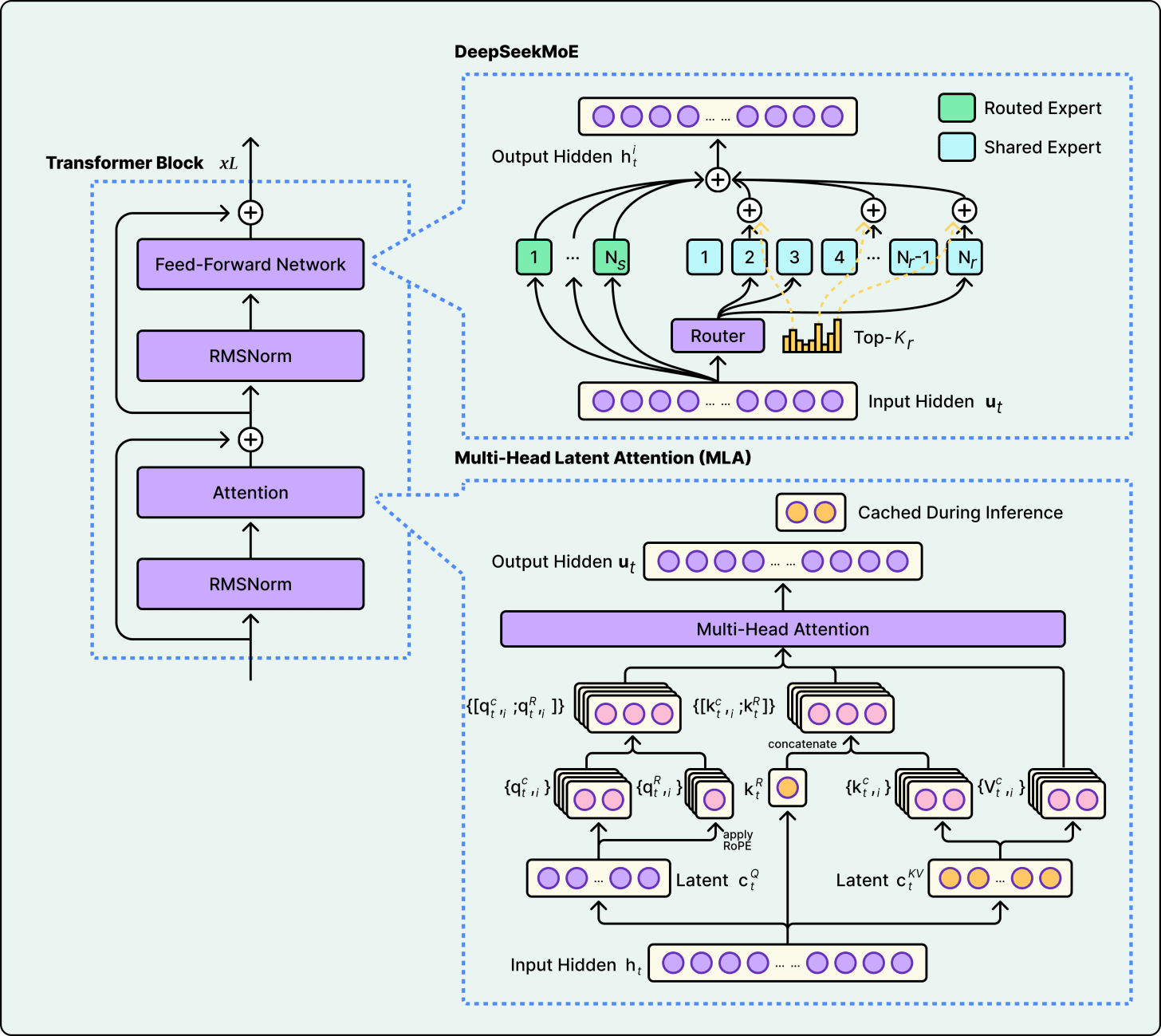
The tradeoff comes down to what matters most in your deployment. GQA is simpler and proven. MLA is more memory-efficient but more complex to engineer. Sparse attention reduces compute for long contexts but requires careful design to avoid missing important tokens. The strategy a model chooses depends on whether the bottleneck is memory, compute, or context length.
The six models range from 16 to 384 experts, reflecting a fundamental disagreement about how far sparsity should be pushed.
At a fixed compute budget, increasing the number of experts can improve both training and validation loss. However, the report also notes that this gain comes with increased infrastructure complexity. More total experts means more total parameters stored in memory, and Kimi K2’s trillion parameters require a multi-GPU cluster regardless of how few fire per token. By contrast, Llama 4 Scout’s 109 billion total parameters can fit on a single high-memory server.
Two other design choices stand out:
First, the shared expert question. DeepSeek V3, Llama 4, and Kimi K2 include a shared expert that processes every token, providing a baseline capability floor. Qwen3’s technical report notes that, unlike their earlier Qwen2.5-MoE, they dropped the shared expert, but doesn’t disclose why. There is no consensus in the field on whether shared experts are worth the compute cost.
Second, Llama 4 takes a unique approach. Rather than making every layer MoE, Llama 4 alternates between dense and MoE layers, and routes each token to only 1 expert (plus the shared) rather than 8. This means fewer active experts per token, but each expert is larger.
See the diagram below that shows Llama’s approach:
Architecture determines capacity, but training determines what a model actually does with it.
Pre-training, where the model learns by predicting the next token across trillions of tokens, gives the model its base knowledge. The scale varies (14.8 trillion tokens for DeepSeek V3, up to 36 trillion for Qwen3), but the approach is similar. Post-training is where models diverge, and it’s now the primary differentiator.
Reinforcement learning with verifiable rewards checks whether the model’s output is objectively correct.
Did the code compile? Is the math answer right? The model is rewarded for correct outputs and penalized for wrong ones. This was the breakthrough behind DeepSeek R1, and elements of it were distilled into DeepSeek V3.
Distillation from a larger teacher trains a massive model and uses its outputs to teach smaller ones. Llama 4 co-distilled from Behemoth, a 2-trillion-parameter teacher model, during pre-training itself. Qwen3 distills from its flagship down to smaller models in the family.
See the diagram below that shows Qwen’s post-training flow:
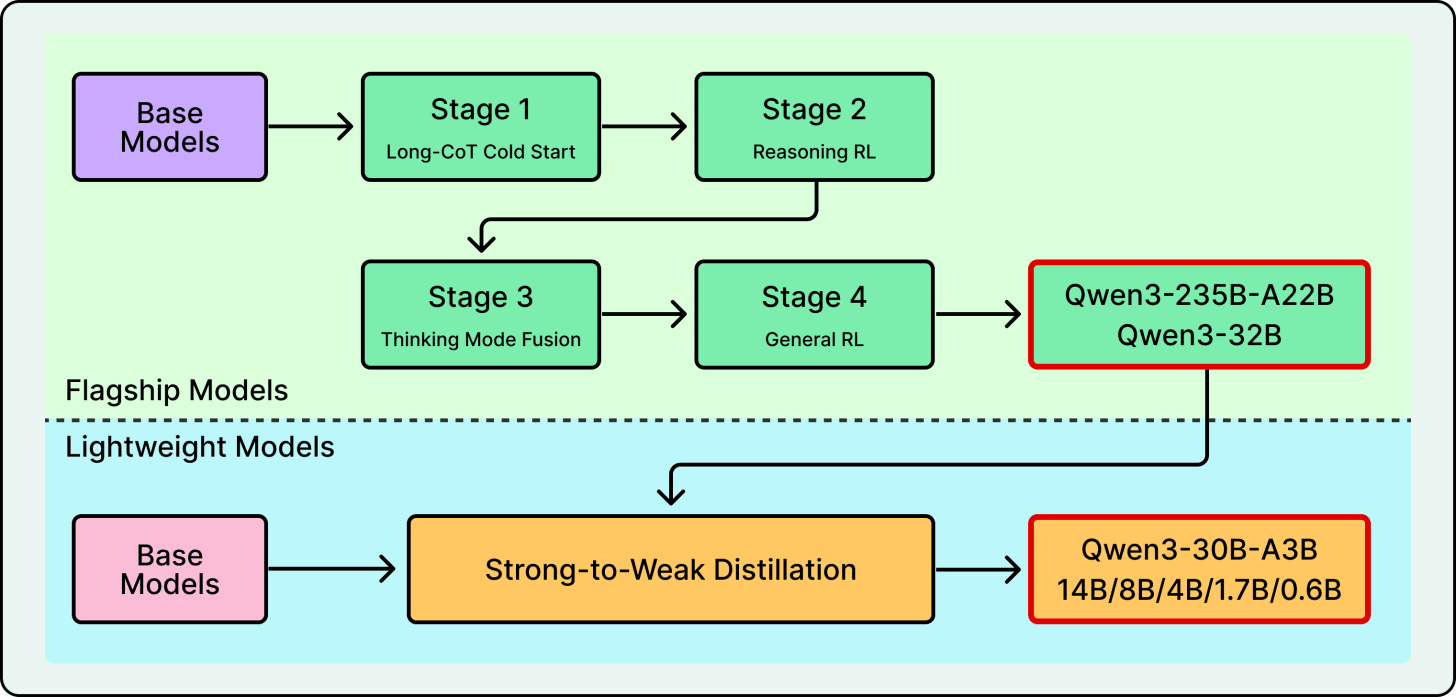
Synthetic agentic data involves building simulated environments loaded with real tools like APIs, shells, and databases, then rewarding the model for completing tasks in those environments. For example, Kimi K2’s technical report describes a large-scale pipeline that systematically generates tool-use demonstrations across simulated and real-world environments.
Novel RL infrastructure can be a contribution in itself. GLM-5 developed “Slime,” a new asynchronous reinforcement learning framework that improves training throughput for post-training, enabling more iterations within the same compute budget.
Training stability also deserves attention here. At this scale, a single training crash can waste days of GPU time. To counter this, Kimi K2 developed the MuonClip optimizer specifically to prevent exploding attention logits, enabling them to train on 15.5 trillion tokens without a single loss spike. DeepSeek V3 similarly reported zero irrecoverable loss spikes across its entire training run. These engineering contributions may prove more reusable than any particular architectural choice.
Architectures are converging. Everyone is building MoE transformers. Training approaches are diverging, with teams placing different bets on reinforcement learning, distillation, synthetic data, and new optimizers.
The specific models covered here will be overtaken in months. However, the framework for evaluating them likely won’t change.
Important questions would still be about active parameter count and not just the total. Also, what attention tradeoff did they make, and does it match the context-length needs? How many experts fire per token, and can the infrastructure handle the total? How was it post-trained, and does that approach align with your use case? What does the license actually permit?
References: