2026-03-10 19:00:22

There have been many questions about what direction Arduino would take after being bought by Qualcomm. Now it would seem that we’re getting a clearer picture. Perhaps unsurprisingly the answer appears to be ‘AI’, with the new Arduino VENTUNO Q SBC being advertised as ‘democratizing AI’ in the Qualcomm press release, although it also references robotics.
This new board is based around the Dragonwing IQ-8275 SoC along with an STM32H5F5 MCU, making it somewhat of a beefier brother of the previously covered Arduino Uno Q, which also offers an SoC/MCU hybrid solution. On the product page we can see the overall specifications for this new board, where the release date is specified as ‘soon’.
Its IQ-8275 SoC is part of Qualcomm’s IQ8 series, with eight 2.35 GHz ARM cores and an Adreno 623 GPU, paired with 16 GB of LPDDR5. The Cortex M33-based STM32H5F5 MCU comes with its own 4 MB of Flash and 1.5 MB of RAM, all on a board that’s significantly larger than the Uno Q and isn’t crippled by a single USB-C port as SoC I/O.
Although clearly more aimed at industrial and automation applications than the solution-in-search-of-a-problem Uno Q board, it remains to be seen whether this board will catch on with Arduino fans, or whether Qualcomm’s goal is more to break into whole new markets under the Arduino brand.
2026-03-10 16:00:19
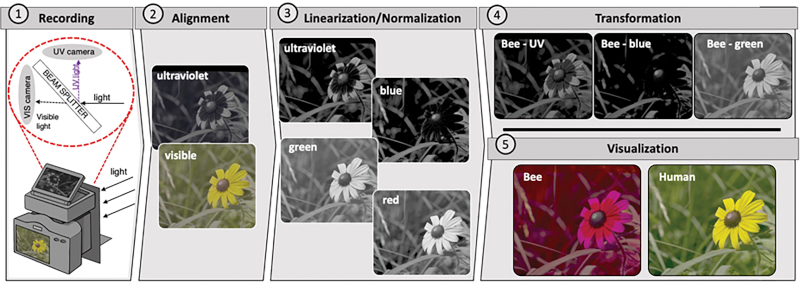
If you think about it, you can’t be sure that what you see for the color red, for example, is what anyone else in the world actually sees. All you can be sure of is that we’ve all been trained to identify whatever we do see as red just like everyone else. Now, think about animal vision. Most people know that dogs don’t see as many colors as we do. On the other hand, the birds and the bees can see into ultraviolet. What would the world look like with extra colors? That’s the question researchers want to answer with this system for duplicating different animals’ views of the world.
Of course, this would be easy if you were thinking about dogs or cats. They can’t see the difference between red and green, making them effectively colorblind by human standards. Researchers are using modified commercial cameras and sophisticated video processing to produce images that sense blue, green, red, and UV light. Then they modify the image based on knowledge of different animal photoreceptors.
We were somewhat surprised that the system didn’t pick up IR. As we know snakes, for example, can sense IR. You’d think more sophisticated animals would have better color vision, but that seems to be untrue. The mantis shrimp, for example, has 12-16 types of photoreceptors. Even male and female humans have different vision systems that make them see colors differently.
Maybe you need a photospectrometer. You wonder if animals dream in color, too.
2026-03-10 13:00:00


Recently [TheRetroChannel] came across an interesting failure mode on a Commodore 1541 5.25″ floppy disk drive, in the form of the activity LED blinking just once after power-up with the drive motor continuously spinning. Since the Flash Codes that Commodore implemented and bothered to document start at 2 flashes (for RAM-related Zero Page), this raised the question of what fault this drive had, and whether a single flash is some kind of undocumented error code.
A cursory check showed that the heads were okay and not shorted, ruling out a common fault with the used floppy mechanism. Cleaning up the corrosion on IC sockets and similar basic operations were performed next, without making a change, nor did removing the ICs to induce it to produce the documented error codes, but this helped narrow down the potential causes. Especially after swapping in known-good ICs failed to make a difference. One possibility was that the drive was boot looping, as the activity LED is lit up once on boot.
Some probing around with an oscilloscope between the faulty and a working drive seemed to point to a faulty RAM IC, but while probing the faulty drive suddenly initialized successfully. After some more poking around it appeared that the drive was fine after it had a chance to warm up, which just deepened the mystery.
The drive did talk to a C64 with diagnostic cartridge at this point, but would often glitch out. Ultimately it appears that a dodgy IC socket and a few bad traces were to blame for the behavior, making it an ‘obvious in hindsight’ repair. The bottom of the PCB had some clear corrosion on it, but the affected traces were apparently still hanging on for dear life with the drive still initializing once warmed up.
2026-03-10 10:00:23
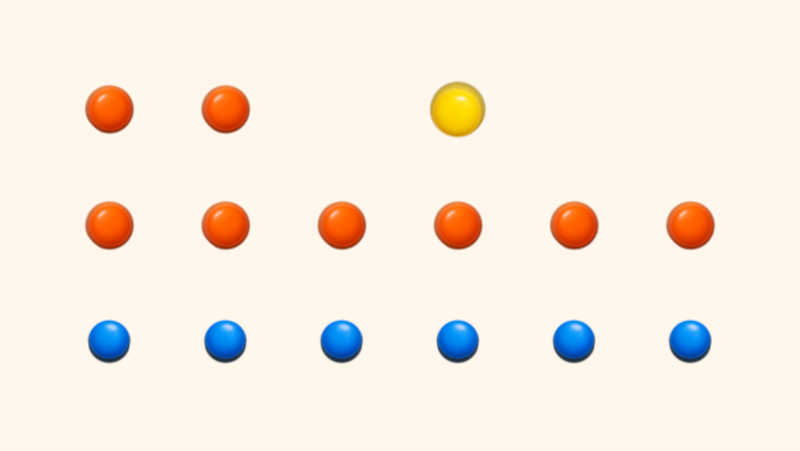
Admit it. If you haven’t created your own little programming language, you’ve probably at least thought about it. [Muffed] decided to create a unique — and sweet — programming language that uses M&M (or, at least, M&M-like) candies as the building block of programs.
If this sounds strange, it is because, honestly, it is. It all started when a packet of GEMS (the Cadbury’s version of M&Ms) spilled and randomly fell in the shape of an arrow. There are only six symbols corresponding to the colors in a package. You create your program by arranging the candies and creating a digital image of the result. In practice, you’ll probably use ASCII text to represent your candy layout and let the compiler render the image for you.
The main way of encoding things is by the number of colored candy pixels in a row. So three blue morsels in an opcode, while four is a different opcode. Red candies encode integer literals with one candy being zero, two being one, and so on. Blue indicates control flow, green candy handles variables and stack operations, yellow is for math, and so on.
Since building things like strings. So, sadly, the M&M program isn’t complete without a run-time data file in JSON format. The title graphic shows a Hello World program that you can run in the web page, but it doesn’t show the JSON file. That’s here:
{
"strings": ["Hello, world!"],
"variables": [],
"inputs": {
"int": [],
"str": []
}
}
We don’t know of any other language where you can literally eat your mistakes. There’s something to be said for that. If you want to try it, you can just write over one of the examples on the web page. Or download from GitHub.
We have seen graphic input languages before. Plus many other weird languages.
2026-03-10 07:00:09

Most people see that garden shed as little more than a place to store some gardening tools in, but if you’re like [Dr. Semiconductor], then what you see is a potential cleanroom for semiconductor manufacturing. As ridiculous as this may sound, the basic steps behind the different levels of cleanrooms work just as well for a multi-million dollar fab as they do for for a basic shed.
Key to everything is HEPA filtration along with positive pressure, to constantly push clean air into the cleanroom, while preventing dirty air from flowing in. The shed was also split into two sections, the first room once you enter it being the the gowning room. This is where you change into cleanroom gear before you transition into the cleanroom.
In addition to the flame-resistant drywalls, a water-based epoxy coating was applied to the insides of the cleanroom walls to make it smooth and free of debris. The HEPA filtration system constantly filters the shed’s air along with some fresh outside air, while an airconditioning unit ensures that the temperature remains constant.
The measured >0.5 µm particle contamination inside the shed turned out to be enough for a FED STD 209E equivalent of Class 100, which is ISO 5 class with a maximum of 3,520 particles/m3. For comparison, room air is ISO 9 with max 35,200,000 particles/m3. At ISO 5 it’s good enough to do some semiconductor R&D laboratory things, which is what [Dr. Semiconductor]’s channel is – shockingly – about.
Thanks to [Thayer] for the tip.
2026-03-10 04:00:54

What hardware hacker doesn’t have a soft spot for transparent cases? While they may have fallen out of mainstream favor, they have an undeniable appeal to anyone with an interest in electronic or mechanical devices. Which is why the Orbigator built by [wyojustin] stands out among similar desktop orbital trackers we’ve seen.
Conceptually, it’s very similar to the International Space Station tracking lamp that [Will Dana] built in 2025. In fact, [wyojustin] cites it specifically as one of the inspirations for this project. But unlike that build, which saw a small model of the ISS moving across the surface of the globe, a transparent globe is rotated around the internal mechanism. This not only looks gorgeous, but solves a key problem in [Will]’s design — that is, there’s no trailing servo wiring that needs to be kept track of.
 For anyone who wants an Orbigator of their own, [wyojustin] has done a fantastic job of documenting the hardware and software aspects of the build, and all the relevant files are available in the project’s GitHub repository.
For anyone who wants an Orbigator of their own, [wyojustin] has done a fantastic job of documenting the hardware and software aspects of the build, and all the relevant files are available in the project’s GitHub repository.
The 3D printable components have been created with OpenSCAD, the firmware responsible for calculating the current position of the ISS on the Raspberry Pi Pico 2 is written in MicroPython, and the PCB was designed in KiCad. Incidentally, we noticed that Hackaday alum [Anool Mahidharia] appears to have been lending a hand with the board design.
As much as we love these polished orbital trackers, we’ve seen far more approachable builds if you don’t need something so elaborate. If you’re more interested in keeping an eye out for planes and can get your hands on a pan-and-tilt security camera, it’s even easier.