2026-03-10 18:00:04
:::info Astounding Stories of Super-Science October, 1994, by Astounding Stories is part of HackerNoon’s Book Blog Post series. You can jump to any chapter in this book here. The Picture of Dorian Gray - Chapter XVI
\ By Oscar Wilde
:::
\ A cold rain began to fall, and the blurred street-lamps looked ghastly in the dripping mist. The public-houses were just closing, and dim men and women were clustering in broken groups round their doors. From some of the bars came the sound of horrible laughter. In others, drunkards brawled and screamed.
Lying back in the hansom, with his hat pulled over his forehead, Dorian Gray watched with listless eyes the sordid shame of the great city, and now and then he repeated to himself the words that Lord Henry had said to him on the first day they had met, “To cure the soul by means of the senses, and the senses by means of the soul.” Yes, that was the secret. He had often tried it, and would try it again now. There were opium dens where one could buy oblivion, dens of horror where the memory of old sins could be destroyed by the madness of sins that were new.
The moon hung low in the sky like a yellow skull. From time to time a huge misshapen cloud stretched a long arm across and hid it. The gas-lamps grew fewer, and the streets more narrow and gloomy. Once the man lost his way and had to drive back half a mile. A steam rose from the horse as it splashed up the puddles. The sidewindows of the hansom were clogged with a grey-flannel mist.
“To cure the soul by means of the senses, and the senses by means of the soul!” How the words rang in his ears! His soul, certainly, was sick to death. Was it true that the senses could cure it? Innocent blood had been spilled. What could atone for that? Ah! for that there was no atonement; but though forgiveness was impossible, forgetfulness was possible still, and he was determined to forget, to stamp the thing out, to crush it as one would crush the adder that had stung one. Indeed, what right had Basil to have spoken to him as he had done? Who had made him a judge over others? He had said things that were dreadful, horrible, not to be endured.
On and on plodded the hansom, going slower, it seemed to him, at each step. He thrust up the trap and called to the man to drive faster. The hideous hunger for opium began to gnaw at him. His throat burned and his delicate hands twitched nervously together. He struck at the horse madly with his stick. The driver laughed and whipped up. He laughed in answer, and the man was silent.
The way seemed interminable, and the streets like the black web of some sprawling spider. The monotony became unbearable, and as the mist thickened, he felt afraid.
Then they passed by lonely brickfields. The fog was lighter here, and he could see the strange, bottle-shaped kilns with their orange, fanlike tongues of fire. A dog barked as they went by, and far away in the darkness some wandering sea-gull screamed. The horse stumbled in a rut, then swerved aside and broke into a gallop.
After some time they left the clay road and rattled again over rough-paven streets. Most of the windows were dark, but now and then fantastic shadows were silhouetted against some lamplit blind. He watched them curiously. They moved like monstrous marionettes and made gestures like live things. He hated them. A dull rage was in his heart. As they turned a corner, a woman yelled something at them from an open door, and two men ran after the hansom for about a hundred yards. The driver beat at them with his whip.
It is said that passion makes one think in a circle. Certainly with hideous iteration the bitten lips of Dorian Gray shaped and reshaped those subtle words that dealt with soul and sense, till he had found in them the full expression, as it were, of his mood, and justified, by intellectual approval, passions that without such justification would still have dominated his temper. From cell to cell of his brain crept the one thought; and the wild desire to live, most terrible of all man’s appetites, quickened into force each trembling nerve and fibre. Ugliness that had once been hateful to him because it made things real, became dear to him now for that very reason. Ugliness was the one reality. The coarse brawl, the loathsome den, the crude violence of disordered life, the very vileness of thief and outcast, were more vivid, in their intense actuality of impression, than all the gracious shapes of art, the dreamy shadows of song. They were what he needed for forgetfulness. In three days he would be free.
Suddenly the man drew up with a jerk at the top of a dark lane. Over the low roofs and jagged chimney-stacks of the houses rose the black masts of ships. Wreaths of white mist clung like ghostly sails to the yards.
“Somewhere about here, sir, ain’t it?” he asked huskily through the trap.
Dorian started and peered round. “This will do,” he answered, and having got out hastily and given the driver the extra fare he had promised him, he walked quickly in the direction of the quay. Here and there a lantern gleamed at the stern of some huge merchantman. The light shook and splintered in the puddles. A red glare came from an outward-bound steamer that was coaling. The slimy pavement looked like a wet mackintosh.
He hurried on towards the left, glancing back now and then to see if he was being followed. In about seven or eight minutes he reached a small shabby house that was wedged in between two gaunt factories. In one of the top-windows stood a lamp. He stopped and gave a peculiar knock.
After a little time he heard steps in the passage and the chain being unhooked. The door opened quietly, and he went in without saying a word to the squat misshapen figure that flattened itself into the shadow as he passed. At the end of the hall hung a tattered green curtain that swayed and shook in the gusty wind which had followed him in from the street. He dragged it aside and entered a long low room which looked as if it had once been a third-rate dancing-saloon. Shrill flaring gas-jets, dulled and distorted in the fly-blown mirrors that faced them, were ranged round the walls. Greasy reflectors of ribbed tin backed them, making quivering disks of light. The floor was covered with ochre-coloured sawdust, trampled here and there into mud, and stained with dark rings of spilled liquor. Some Malays were crouching by a little charcoal stove, playing with bone counters and showing their white teeth as they chattered. In one corner, with his head buried in his arms, a sailor sprawled over a table, and by the tawdrily painted bar that ran across one complete side stood two haggard women, mocking an old man who was brushing the sleeves of his coat with an expression of disgust. “He thinks he’s got red ants on him,” laughed one of them, as Dorian passed by. The man looked at her in terror and began to whimper.
At the end of the room there was a little staircase, leading to a darkened chamber. As Dorian hurried up its three rickety steps, the heavy odour of opium met him. He heaved a deep breath, and his nostrils quivered with pleasure. When he entered, a young man with smooth yellow hair, who was bending over a lamp lighting a long thin pipe, looked up at him and nodded in a hesitating manner.
“You here, Adrian?” muttered Dorian.
“Where else should I be?” he answered, listlessly. “None of the chaps will speak to me now.”
“I thought you had left England.”
“Darlington is not going to do anything. My brother paid the bill at last. George doesn’t speak to me either…. I don’t care,” he added with a sigh. “As long as one has this stuff, one doesn’t want friends. I think I have had too many friends.”
Dorian winced and looked round at the grotesque things that lay in such fantastic postures on the ragged mattresses. The twisted limbs, the gaping mouths, the staring lustreless eyes, fascinated him. He knew in what strange heavens they were suffering, and what dull hells were teaching them the secret of some new joy. They were better off than he was. He was prisoned in thought. Memory, like a horrible malady, was eating his soul away. From time to time he seemed to see the eyes of Basil Hallward looking at him. Yet he felt he could not stay. The presence of Adrian Singleton troubled him. He wanted to be where no one would know who he was. He wanted to escape from himself.
“I am going on to the other place,” he said after a pause.
“On the wharf?”
“Yes.”
“That mad-cat is sure to be there. They won’t have her in this place now.”
Dorian shrugged his shoulders. “I am sick of women who love one. Women who hate one are much more interesting. Besides, the stuff is better.”
“Much the same.”
“I like it better. Come and have something to drink. I must have something.”
“I don’t want anything,” murmured the young man.
“Never mind.”
Adrian Singleton rose up wearily and followed Dorian to the bar. A half-caste, in a ragged turban and a shabby ulster, grinned a hideous greeting as he thrust a bottle of brandy and two tumblers in front of them. The women sidled up and began to chatter. Dorian turned his back on them and said something in a low voice to Adrian Singleton.
A crooked smile, like a Malay crease, writhed across the face of one of the women. “We are very proud to-night,” she sneered.
“For God’s sake don’t talk to me,” cried Dorian, stamping his foot on the ground. “What do you want? Money? Here it is. Don’t ever talk to me again.”
Two red sparks flashed for a moment in the woman’s sodden eyes, then flickered out and left them dull and glazed. She tossed her head and raked the coins off the counter with greedy fingers. Her companion watched her enviously.
“It’s no use,” sighed Adrian Singleton. “I don’t care to go back. What does it matter? I am quite happy here.”
“You will write to me if you want anything, won’t you?” said Dorian, after a pause.
“Perhaps.”
“Good night, then.”
“Good night,” answered the young man, passing up the steps and wiping his parched mouth with a handkerchief.
Dorian walked to the door with a look of pain in his face. As he drew the curtain aside, a hideous laugh broke from the painted lips of the woman who had taken his money. “There goes the devil’s bargain!” she hiccoughed, in a hoarse voice.
“Curse you!” he answered, “don’t call me that.”
She snapped her fingers. “Prince Charming is what you like to be called, ain’t it?” she yelled after him.
The drowsy sailor leaped to his feet as she spoke, and looked wildly round. The sound of the shutting of the hall door fell on his ear. He rushed out as if in pursuit.
Dorian Gray hurried along the quay through the drizzling rain. His meeting with Adrian Singleton had strangely moved him, and he wondered if the ruin of that young life was really to be laid at his door, as Basil Hallward had said to him with such infamy of insult. He bit his lip, and for a few seconds his eyes grew sad. Yet, after all, what did it matter to him? One’s days were too brief to take the burden of another’s errors on one’s shoulders. Each man lived his own life and paid his own price for living it. The only pity was one had to pay so often for a single fault. One had to pay over and over again, indeed. In her dealings with man, destiny never closed her accounts.
There are moments, psychologists tell us, when the passion for sin, or for what the world calls sin, so dominates a nature that every fibre of the body, as every cell of the brain, seems to be instinct with fearful impulses. Men and women at such moments lose the freedom of their will. They move to their terrible end as automatons move. Choice is taken from them, and conscience is either killed, or, if it lives at all, lives but to give rebellion its fascination and disobedience its charm. For all sins, as theologians weary not of reminding us, are sins of disobedience. When that high spirit, that morning star of evil, fell from heaven, it was as a rebel that he fell.
Callous, concentrated on evil, with stained mind, and soul hungry for rebellion, Dorian Gray hastened on, quickening his step as he went, but as he darted aside into a dim archway, that had served him often as a short cut to the ill-famed place where he was going, he felt himself suddenly seized from behind, and before he had time to defend himself, he was thrust back against the wall, with a brutal hand round his throat.
He struggled madly for life, and by a terrible effort wrenched the tightening fingers away. In a second he heard the click of a revolver, and saw the gleam of a polished barrel, pointing straight at his head, and the dusky form of a short, thick-set man facing him.
“What do you want?” he gasped.
“Keep quiet,” said the man. “If you stir, I shoot you.”
“You are mad. What have I done to you?”
“You wrecked the life of Sibyl Vane,” was the answer, “and Sibyl Vane was my sister. She killed herself. I know it. Her death is at your door. I swore I would kill you in return. For years I have sought you. I had no clue, no trace. The two people who could have described you were dead. I knew nothing of you but the pet name she used to call you. I heard it to-night by chance. Make your peace with God, for to-night you are going to die.”
Dorian Gray grew sick with fear. “I never knew her,” he stammered. “I never heard of her. You are mad.”
“You had better confess your sin, for as sure as I am James Vane, you are going to die.” There was a horrible moment. Dorian did not know what to say or do. “Down on your knees!” growled the man. “I give you one minute to make your peace—no more. I go on board to-night for India, and I must do my job first. One minute. That’s all.”
Dorian’s arms fell to his side. Paralysed with terror, he did not know what to do. Suddenly a wild hope flashed across his brain. “Stop,” he cried. “How long ago is it since your sister died? Quick, tell me!”
“Eighteen years,” said the man. “Why do you ask me? What do years matter?”
“Eighteen years,” laughed Dorian Gray, with a touch of triumph in his voice. “Eighteen years! Set me under the lamp and look at my face!”
James Vane hesitated for a moment, not understanding what was meant. Then he seized Dorian Gray and dragged him from the archway.
Dim and wavering as was the wind-blown light, yet it served to show him the hideous error, as it seemed, into which he had fallen, for the face of the man he had sought to kill had all the bloom of boyhood, all the unstained purity of youth. He seemed little more than a lad of twenty summers, hardly older, if older indeed at all, than his sister had been when they had parted so many years ago. It was obvious that this was not the man who had destroyed her life.
He loosened his hold and reeled back. “My God! my God!” he cried, “and I would have murdered you!”
Dorian Gray drew a long breath. “You have been on the brink of committing a terrible crime, my man,” he said, looking at him sternly. “Let this be a warning to you not to take vengeance into your own hands.”
“Forgive me, sir,” muttered James Vane. “I was deceived. A chance word I heard in that damned den set me on the wrong track.”
“You had better go home and put that pistol away, or you may get into trouble,” said Dorian, turning on his heel and going slowly down the street.
James Vane stood on the pavement in horror. He was trembling from head to foot. After a little while, a black shadow that had been creeping along the dripping wall moved out into the light and came close to him with stealthy footsteps. He felt a hand laid on his arm and looked round with a start. It was one of the women who had been drinking at the bar.
“Why didn’t you kill him?” she hissed out, putting haggard face quite close to his. “I knew you were following him when you rushed out from Daly’s. You fool! You should have killed him. He has lots of money, and he’s as bad as bad.”
“He is not the man I am looking for,” he answered, “and I want no man’s money. I want a man’s life. The man whose life I want must be nearly forty now. This one is little more than a boy. Thank God, I have not got his blood upon my hands.”
The woman gave a bitter laugh. “Little more than a boy!” she sneered. “Why, man, it’s nigh on eighteen years since Prince Charming made me what I am.”
“You lie!” cried James Vane.
She raised her hand up to heaven. “Before God I am telling the truth,” she cried.
“Before God?”
“Strike me dumb if it ain’t so. He is the worst one that comes here. They say he has sold himself to the devil for a pretty face. It’s nigh on eighteen years since I met him. He hasn’t changed much since then. I have, though,” she added, with a sickly leer.
“You swear this?”
“I swear it,” came in hoarse echo from her flat mouth. “But don’t give me away to him,” she whined; “I am afraid of him. Let me have some money for my night’s lodging.”
He broke from her with an oath and rushed to the corner of the street, but Dorian Gray had disappeared. When he looked back, the woman had vanished also.
\
:::info About HackerNoon Book Series: We bring you the most important technical, scientific, and insightful public domain books.
This book is part of the public domain. Astounding Stories. (2009). ASTOUNDING STORIES OF SUPER-SCIENCE, OCTOBER 1994. USA. Project Gutenberg. Release date: October 1, 1994, from https://www.gutenberg.org/cache/epub/174/pg174-images.html
This eBook is for the use of anyone anywhere at no cost and with almost no restrictions whatsoever. You may copy it, give it away or re-use it under the terms of the Project Gutenberg License included with this eBook or online at www.gutenberg.org, located at https://www.gutenberg.org/policy/license.html.
:::
\
2026-03-10 17:30:04
:::info Astounding Stories of Super-Science October, 1994, by Astounding Stories is part of HackerNoon’s Book Blog Post series. You can jump to any chapter in this book here. The Picture of Dorian Gray - Chapter XV
\ By Oscar Wilde
:::
\ That evening, at eight-thirty, exquisitely dressed and wearing a large button-hole of Parma violets, Dorian Gray was ushered into Lady Narborough’s drawing-room by bowing servants. His forehead was throbbing with maddened nerves, and he felt wildly excited, but his manner as he bent over his hostess’s hand was as easy and graceful as ever. Perhaps one never seems so much at one’s ease as when one has to play a part. Certainly no one looking at Dorian Gray that night could have believed that he had passed through a tragedy as horrible as any tragedy of our age. Those finely shaped fingers could never have clutched a knife for sin, nor those smiling lips have cried out on God and goodness. He himself could not help wondering at the calm of his demeanour, and for a moment felt keenly the terrible pleasure of a double life.
It was a small party, got up rather in a hurry by Lady Narborough, who was a very clever woman with what Lord Henry used to describe as the remains of really remarkable ugliness. She had proved an excellent wife to one of our most tedious ambassadors, and having buried her husband properly in a marble mausoleum, which she had herself designed, and married off her daughters to some rich, rather elderly men, she devoted herself now to the pleasures of French fiction, French cookery, and French esprit when she could get it.
Dorian was one of her especial favourites, and she always told him that she was extremely glad she had not met him in early life. “I know, my dear, I should have fallen madly in love with you,” she used to say, “and thrown my bonnet right over the mills for your sake. It is most fortunate that you were not thought of at the time. As it was, our bonnets were so unbecoming, and the mills were so occupied in trying to raise the wind, that I never had even a flirtation with anybody. However, that was all Narborough’s fault. He was dreadfully short-sighted, and there is no pleasure in taking in a husband who never sees anything.”
Her guests this evening were rather tedious. The fact was, as she explained to Dorian, behind a very shabby fan, one of her married daughters had come up quite suddenly to stay with her, and, to make matters worse, had actually brought her husband with her. “I think it is most unkind of her, my dear,” she whispered. “Of course I go and stay with them every summer after I come from Homburg, but then an old woman like me must have fresh air sometimes, and besides, I really wake them up. You don’t know what an existence they lead down there. It is pure unadulterated country life. They get up early, because they have so much to do, and go to bed early, because they have so little to think about. There has not been a scandal in the neighbourhood since the time of Queen Elizabeth, and consequently they all fall asleep after dinner. You shan’t sit next either of them. You shall sit by me and amuse me.”
Dorian murmured a graceful compliment and looked round the room. Yes: it was certainly a tedious party. Two of the people he had never seen before, and the others consisted of Ernest Harrowden, one of those middle-aged mediocrities so common in London clubs who have no enemies, but are thoroughly disliked by their friends; Lady Ruxton, an overdressed woman of forty-seven, with a hooked nose, who was always trying to get herself compromised, but was so peculiarly plain that to her great disappointment no one would ever believe anything against her; Mrs. Erlynne, a pushing nobody, with a delightful lisp and Venetian-red hair; Lady Alice Chapman, his hostess’s daughter, a dowdy dull girl, with one of those characteristic British faces that, once seen, are never remembered; and her husband, a red-cheeked, white-whiskered creature who, like so many of his class, was under the impression that inordinate joviality can atone for an entire lack of ideas.
He was rather sorry he had come, till Lady Narborough, looking at the great ormolu gilt clock that sprawled in gaudy curves on the mauve-draped mantelshelf, exclaimed: “How horrid of Henry Wotton to be so late! I sent round to him this morning on chance and he promised faithfully not to disappoint me.”
It was some consolation that Harry was to be there, and when the door opened and he heard his slow musical voice lending charm to some insincere apology, he ceased to feel bored.
But at dinner he could not eat anything. Plate after plate went away untasted. Lady Narborough kept scolding him for what she called “an insult to poor Adolphe, who invented the menu specially for you,” and now and then Lord Henry looked across at him, wondering at his silence and abstracted manner. From time to time the butler filled his glass with champagne. He drank eagerly, and his thirst seemed to increase.
“Dorian,” said Lord Henry at last, as the chaud-froid was being handed round, “what is the matter with you to-night? You are quite out of sorts.”
“I believe he is in love,” cried Lady Narborough, “and that he is afraid to tell me for fear I should be jealous. He is quite right. I certainly should.”
“Dear Lady Narborough,” murmured Dorian, smiling, “I have not been in love for a whole week—not, in fact, since Madame de Ferrol left town.”
“How you men can fall in love with that woman!” exclaimed the old lady. “I really cannot understand it.”
“It is simply because she remembers you when you were a little girl, Lady Narborough,” said Lord Henry. “She is the one link between us and your short frocks.”
“She does not remember my short frocks at all, Lord Henry. But I remember her very well at Vienna thirty years ago, and how décolletée she was then.”
“She is still décolletée,” he answered, taking an olive in his long fingers; “and when she is in a very smart gown she looks like an édition de luxe of a bad French novel. She is really wonderful, and full of surprises. Her capacity for family affection is extraordinary. When her third husband died, her hair turned quite gold from grief.”
“How can you, Harry!” cried Dorian.
“It is a most romantic explanation,” laughed the hostess. “But her third husband, Lord Henry! You don’t mean to say Ferrol is the fourth?”
“Certainly, Lady Narborough.”
“I don’t believe a word of it.”
“Well, ask Mr. Gray. He is one of her most intimate friends.”
“Is it true, Mr. Gray?”
“She assures me so, Lady Narborough,” said Dorian. “I asked her whether, like Marguerite de Navarre, she had their hearts embalmed and hung at her girdle. She told me she didn’t, because none of them had had any hearts at all.”
“Four husbands! Upon my word that is trop de zêle.”
“Trop d’audace, I tell her,” said Dorian.
“Oh! she is audacious enough for anything, my dear. And what is Ferrol like? I don’t know him.”
“The husbands of very beautiful women belong to the criminal classes,” said Lord Henry, sipping his wine.
Lady Narborough hit him with her fan. “Lord Henry, I am not at all surprised that the world says that you are extremely wicked.”
“But what world says that?” asked Lord Henry, elevating his eyebrows. “It can only be the next world. This world and I are on excellent terms.”
“Everybody I know says you are very wicked,” cried the old lady, shaking her head.
Lord Henry looked serious for some moments. “It is perfectly monstrous,” he said, at last, “the way people go about nowadays saying things against one behind one’s back that are absolutely and entirely true.”
“Isn’t he incorrigible?” cried Dorian, leaning forward in his chair.
“I hope so,” said his hostess, laughing. “But really, if you all worship Madame de Ferrol in this ridiculous way, I shall have to marry again so as to be in the fashion.”
“You will never marry again, Lady Narborough,” broke in Lord Henry. “You were far too happy. When a woman marries again, it is because she detested her first husband. When a man marries again, it is because he adored his first wife. Women try their luck; men risk theirs.”
“Narborough wasn’t perfect,” cried the old lady.
“If he had been, you would not have loved him, my dear lady,” was the rejoinder. “Women love us for our defects. If we have enough of them, they will forgive us everything, even our intellects. You will never ask me to dinner again after saying this, I am afraid, Lady Narborough, but it is quite true.”
“Of course it is true, Lord Henry. If we women did not love you for your defects, where would you all be? Not one of you would ever be married. You would be a set of unfortunate bachelors. Not, however, that that would alter you much. Nowadays all the married men live like bachelors, and all the bachelors like married men.”
“Fin de siêcle,” murmured Lord Henry.
“Fin du globe,” answered his hostess.
“I wish it were fin du globe,” said Dorian with a sigh. “Life is a great disappointment.”
“Ah, my dear,” cried Lady Narborough, putting on her gloves, “don’t tell me that you have exhausted life. When a man says that one knows that life has exhausted him. Lord Henry is very wicked, and I sometimes wish that I had been; but you are made to be good—you look so good. I must find you a nice wife. Lord Henry, don’t you think that Mr. Gray should get married?”
“I am always telling him so, Lady Narborough,” said Lord Henry with a bow.
“Well, we must look out for a suitable match for him. I shall go through Debrett carefully to-night and draw out a list of all the eligible young ladies.”
“With their ages, Lady Narborough?” asked Dorian.
“Of course, with their ages, slightly edited. But nothing must be done in a hurry. I want it to be what The Morning Post calls a suitable alliance, and I want you both to be happy.”
“What nonsense people talk about happy marriages!” exclaimed Lord Henry. “A man can be happy with any woman, as long as he does not love her.”
“Ah! what a cynic you are!” cried the old lady, pushing back her chair and nodding to Lady Ruxton. “You must come and dine with me soon again. You are really an admirable tonic, much better than what Sir Andrew prescribes for me. You must tell me what people you would like to meet, though. I want it to be a delightful gathering.”
“I like men who have a future and women who have a past,” he answered. “Or do you think that would make it a petticoat party?”
“I fear so,” she said, laughing, as she stood up. “A thousand pardons, my dear Lady Ruxton,” she added, “I didn’t see you hadn’t finished your cigarette.”
“Never mind, Lady Narborough. I smoke a great deal too much. I am going to limit myself, for the future.”
“Pray don’t, Lady Ruxton,” said Lord Henry. “Moderation is a fatal thing. Enough is as bad as a meal. More than enough is as good as a feast.”
Lady Ruxton glanced at him curiously. “You must come and explain that to me some afternoon, Lord Henry. It sounds a fascinating theory,” she murmured, as she swept out of the room.
“Now, mind you don’t stay too long over your politics and scandal,” cried Lady Narborough from the door. “If you do, we are sure to squabble upstairs.”
The men laughed, and Mr. Chapman got up solemnly from the foot of the table and came up to the top. Dorian Gray changed his seat and went and sat by Lord Henry. Mr. Chapman began to talk in a loud voice about the situation in the House of Commons. He guffawed at his adversaries. The word doctrinaire—word full of terror to the British mind—reappeared from time to time between his explosions. An alliterative prefix served as an ornament of oratory. He hoisted the Union Jack on the pinnacles of thought. The inherited stupidity of the race—sound English common sense he jovially termed it—was shown to be the proper bulwark for society.
A smile curved Lord Henry’s lips, and he turned round and looked at Dorian.
“Are you better, my dear fellow?” he asked. “You seemed rather out of sorts at dinner.”
“I am quite well, Harry. I am tired. That is all.”
“You were charming last night. The little duchess is quite devoted to you. She tells me she is going down to Selby.”
“She has promised to come on the twentieth.”
“Is Monmouth to be there, too?”
“Oh, yes, Harry.”
“He bores me dreadfully, almost as much as he bores her. She is very clever, too clever for a woman. She lacks the indefinable charm of weakness. It is the feet of clay that make the gold of the image precious. Her feet are very pretty, but they are not feet of clay. White porcelain feet, if you like. They have been through the fire, and what fire does not destroy, it hardens. She has had experiences.”
“How long has she been married?” asked Dorian.
“An eternity, she tells me. I believe, according to the peerage, it is ten years, but ten years with Monmouth must have been like eternity, with time thrown in. Who else is coming?”
“Oh, the Willoughbys, Lord Rugby and his wife, our hostess, Geoffrey Clouston, the usual set. I have asked Lord Grotrian.”
“I like him,” said Lord Henry. “A great many people don’t, but I find him charming. He atones for being occasionally somewhat overdressed by being always absolutely over-educated. He is a very modern type.”
“I don’t know if he will be able to come, Harry. He may have to go to Monte Carlo with his father.”
“Ah! what a nuisance people’s people are! Try and make him come. By the way, Dorian, you ran off very early last night. You left before eleven. What did you do afterwards? Did you go straight home?”
Dorian glanced at him hurriedly and frowned.
“No, Harry,” he said at last, “I did not get home till nearly three.”
“Did you go to the club?”
“Yes,” he answered. Then he bit his lip. “No, I don’t mean that. I didn’t go to the club. I walked about. I forget what I did…. How inquisitive you are, Harry! You always want to know what one has been doing. I always want to forget what I have been doing. I came in at half-past two, if you wish to know the exact time. I had left my latch-key at home, and my servant had to let me in. If you want any corroborative evidence on the subject, you can ask him.”
Lord Henry shrugged his shoulders. “My dear fellow, as if I cared! Let us go up to the drawing-room. No sherry, thank you, Mr. Chapman. Something has happened to you, Dorian. Tell me what it is. You are not yourself to-night.”
“Don’t mind me, Harry. I am irritable, and out of temper. I shall come round and see you to-morrow, or next day. Make my excuses to Lady Narborough. I shan’t go upstairs. I shall go home. I must go home.”
“All right, Dorian. I dare say I shall see you to-morrow at tea-time. The duchess is coming.”
“I will try to be there, Harry,” he said, leaving the room. As he drove back to his own house, he was conscious that the sense of terror he thought he had strangled had come back to him. Lord Henry’s casual questioning had made him lose his nerve for the moment, and he wanted his nerve still. Things that were dangerous had to be destroyed. He winced. He hated the idea of even touching them.
Yet it had to be done. He realized that, and when he had locked the door of his library, he opened the secret press into which he had thrust Basil Hallward’s coat and bag. A huge fire was blazing. He piled another log on it. The smell of the singeing clothes and burning leather was horrible. It took him three-quarters of an hour to consume everything. At the end he felt faint and sick, and having lit some Algerian pastilles in a pierced copper brazier, he bathed his hands and forehead with a cool musk-scented vinegar.
Suddenly he started. His eyes grew strangely bright, and he gnawed nervously at his underlip. Between two of the windows stood a large Florentine cabinet, made out of ebony and inlaid with ivory and blue lapis. He watched it as though it were a thing that could fascinate and make afraid, as though it held something that he longed for and yet almost loathed. His breath quickened. A mad craving came over him. He lit a cigarette and then threw it away. His eyelids drooped till the long fringed lashes almost touched his cheek. But he still watched the cabinet. At last he got up from the sofa on which he had been lying, went over to it, and having unlocked it, touched some hidden spring. A triangular drawer passed slowly out. His fingers moved instinctively towards it, dipped in, and closed on something. It was a small Chinese box of black and gold-dust lacquer, elaborately wrought, the sides patterned with curved waves, and the silken cords hung with round crystals and tasselled in plaited metal threads. He opened it. Inside was a green paste, waxy in lustre, the odour curiously heavy and persistent.
He hesitated for some moments, with a strangely immobile smile upon his face. Then shivering, though the atmosphere of the room was terribly hot, he drew himself up and glanced at the clock. It was twenty minutes to twelve. He put the box back, shutting the cabinet doors as he did so, and went into his bedroom.
As midnight was striking bronze blows upon the dusky air, Dorian Gray, dressed commonly, and with a muffler wrapped round his throat, crept quietly out of his house. In Bond Street he found a hansom with a good horse. He hailed it and in a low voice gave the driver an address.
The man shook his head. “It is too far for me,” he muttered.
“Here is a sovereign for you,” said Dorian. “You shall have another if you drive fast.”
“All right, sir,” answered the man, “you will be there in an hour,” and after his fare had got in he turned his horse round and drove rapidly towards the river.
\ \
:::info About HackerNoon Book Series: We bring you the most important technical, scientific, and insightful public domain books.
This book is part of the public domain. Astounding Stories. (2009). ASTOUNDING STORIES OF SUPER-SCIENCE, OCTOBER 1994. USA. Project Gutenberg. Release date: October 1, 1994, from https://www.gutenberg.org/cache/epub/174/pg174-images.html
This eBook is for the use of anyone anywhere at no cost and with almost no restrictions whatsoever. You may copy it, give it away or re-use it under the terms of the Project Gutenberg License included with this eBook or online at www.gutenberg.org, located at https://www.gutenberg.org/policy/license.html.
:::
\
2026-03-10 17:00:07
Aakriti Kharel, a graduate in Biology and current Master’s student in Artificial Intelligence, has traversed continents and disciplines on her path from Nepal to Texas. With professional experience in hospitals and research laboratories in both countries, and an active record of community science engagement, Kharel brings cross-cultural insight to the ongoing challenge of advancing women’s roles in STEM.
Her work foregrounds the value of empathy, leadership, and practical mentorship in an environment that remains defined by both immense progress and persistent gender disparities. The drive to increase women’s participation and leadership in science and technology is a global imperative. In regions like South Asia and Latin America, gender gaps in STEM persist despite notable advancements in education and advocacy.
The intersection of grassroots efforts and global journeys—like that of Kharel—reveals patterns of challenge and resilience, and points to innovative pathways poised to cultivate a new generation of women leaders in science.
Early education in Nepal shaped Kharel’s recognition of women’s unique contributions to healthcare. She observed that patients were often more comfortable and open with women in healthcare roles, especially women, children, and the elderly, and saw that empathy and cultural comfort play a vital role.
She explains, "This showed me early on that healthcare is not only about knowledge and treatment, but also about empathy, communication, and cultural comfort." Upon arriving in the United States, Kharel witnessed women confidently pursuing and leading in science, supported by institutional encouragement.
Her perspective evolved: "When women are given equal space and support, they bring not only strong clinical skills but also a unique ability to connect with patients, build trust, and improve the overall quality of care." These reflections parallel research indicating that near gender parity among researchers does not always translate to senior or leadership roles in STEM fields worldwide.
Transitioning across international STEM environments, Kharel navigated challenges of adaptation and often needed to assert herself in male-dominated spaces while away from her support networks. She notes, "I had to adjust to new academic cultures, communicate in unfamiliar environments, and sometimes prove my confidence in spaces that were still largely male-dominated."
To meet these challenges, "I navigated these challenges by staying focused on learning, surrounding myself with supportive mentors and peers, and embracing my background as a source of strength." This experience reflects broader barriers in STEM, such as a lack of role models, stereotyped perceptions, and limited information that can hinder women’s progress and representation, especially in engineering and technology fields.
Kharel described a pivotal moment during a rural health camp where hesitant girls became inspired after seeing women in visible STEM roles. Girls asked questions after seeing women doctors and volunteers confidently leading the work, and she recalls, "That moment showed me how powerful it is for young girls to see someone who looks like them in roles they once thought were out of reach."
Structured mentorship, as shown in global STEM networks, can drive confidence and retention. Mentorship initiatives such as Technovation and Girls Who Code document similar benefits, and regionally, female-led programs help inspire the next generation through visibility and practical guidance.
Hands-on laboratory work in Nepal and Texas honed Kharel’s capacity for both resourcefulness and accuracy. In Nepal, she states, "I learned to be resourceful, adaptable, and to find solutions even with limited tools."
Texas provided exposure to: "Structured systems, advanced technology, and teamwork in a fast-paced, high-standard environment." Kharel notes, "Together, these experiences taught me to approach problems with both creativity and precision, and to lead with empathy, collaboration, and a focus on making science practical and impactful for real people."
Researchers recommend adopting multifaceted strategies supported by advocacy to help women move into leadership and overcome barriers.
Kharel’s cross-cultural journey provides relatable guidance for young women in STEM. She recalls, "Every day felt like a question of ‘What should I do next?’ and ‘Which path is right for me?’ There were moments of confusion, self-doubt, and loneliness, but also moments of growth as I slowly learned to navigate a new system."
She now offers clarity and reassurance: "I use my cross-cultural journey to show young women that their background can be a strength, not a limitation." Evidence from structured programs demonstrates that mentorship by culturally diverse leaders supports mentees in research and confidence-building. Kharel’s first-hand approach aligns with best practices in mentorship and representation.
Community service taught Kharel, stating, "Real impact comes from listening, collaboration, and staying grounded in people’s needs." She applies these lessons in academia: "I carry these lessons into my academic and scientific pursuits by approaching problems with empathy, valuing diverse perspectives, and focusing on solutions that are practical, inclusive, and meaningful."
Best practices for STEM mentorship and community service stress the value of collaboration, inclusivity, and continuous improvement to achieve lasting outcomes for women in science.
Kharel’s goal is to foster inclusive environments and empower women across disciplines. "I started with a background in Biology, worked in hospital and stem cell laboratories, and now I am pursuing a Master’s in Artificial Intelligence."
She says, "I want to use my experiences to mentor and support them, showing that it is possible to grow across different fields and cultures." She envisions, “Learning and work environments where women feel encouraged, valued, and confident to lead and innovate."
The movement for equity in STEM worldwide is bolstered by robust evaluation, intentional mentorship, and intersectional support. By sharing her lived experience and leadership, Kharel demonstrates how crossing cultures, showing resilience, and advocating for others can build new pathways to inclusion for aspiring women in science.
Transforming STEM’s gender landscape will require more than statistics. The cumulative stories of women who bridge cultures, mentor from experience, and lead with empathy—including Kharel—serve to create opportunity, strengthen networks, and foster lasting impact for a truly representative next generation in science and technology.
\
:::tip This story was distributed as a release by Jon Stojan under HackerNoon’s Business Blogging Program.
:::
\
2026-03-10 15:00:07
:::info
:::
\
Computational catalysis is playing an increasingly significant role in the design of catalysts across a wide range of applications. A common task for many computational methods is the need to accurately compute the adsorption energy for an adsorbate and a catalyst surface of interest. Traditionally, the identification of low-energy adsorbate-surface configurations relies on heuristic methods and researcher intuition. As the desire to perform high-throughput screening increases, it becomes challenging to use heuristics and intuition alone. In this paper, we demonstrate machine learning potentials can be leveraged to identify low-energy adsorbate-surface configurations more accurately and efficiently. Our algorithm provides a spectrum of trade-offs between accuracy and efficiency, with one balanced option finding the lowest energy configuration 87.36% of the time, while achieving a ~2000× speedup in computation. To standardize benchmarking, we introduce the Open Catalyst Dense dataset containing nearly 1000 diverse surfaces and ~100,000 unique configurations.
\
The design of novel heterogeneous catalysts plays an essential role in the synthesis of everyday fuels and chemicals. To accommodate the growing demand for energy while combating climate change, efficient, low-cost catalysts are critical to the utilization of renewable energy1,2,3,4. Given the enormity of the material design space, efficient screening methods are highly sought after4,5,6,7. Computational catalysis offers the potential to screen vast numbers of materials to complement more time- and cost-intensive experimental studies.
A critical task for many first-principles approaches to heterogeneous catalyst discovery is the calculation of adsorption energies. The adsorption energy is the energy associated with a molecule, or adsorbate, interacting with a catalyst surface. Adsorbates are often selected to capture the various steps, or intermediates, in a reaction pathway (e.g., *CHO in CO2 reduction). Adsorption energy is calculated by finding the adsorbate-surface configuration that minimizes the structure’s overall energy. Thus, the adsorption energy is the global minimum energy across all potential adsorbate placements and configurations. These adsorption energies are the starting point for the calculation of the free energy diagrams to determine the most favorable reaction pathways on a catalyst surface8. It has been demonstrated that adsorption energies of reaction intermediates can be powerful descriptors that correlate with experimental outcomes such as activity or selectivity9,10,11,12,13. This ability to predict trends in catalytic properties from first principles is the basis for efficient catalyst screening approaches1,14.
Finding the adsorption energy presents a number of complexities. There are numerous potential binding sites for an adsorbate on a surface, and for each binding site there are multiple ways to orient the adsorbate (see bottom left in Fig. 1). When an adsorbate is placed on a catalyst’s surface, the adsorbate and surface atoms will interact with each other. To determine the adsorption energy for a specific adsorbate-surface configuration, the atom positions need to be relaxed until a local energy minimum is reached. Density Functional Theory (DFT)15,16,17 is the most common approach to performing this adsorbate-surface relaxation. DFT first computes a single-point calculation where the output is the system’s energy and the per-atoms forces. A relaxation then performs a local optimization where per-atom forces are iteratively calculated with DFT and used to update atom positions with an optimization algorithm (e.g., conjugate gradient18) until a local energy minimum is found. To find the global minimum, a strategy for sampling adsorbate-surface configurations and/or a technique such as minima hopping19,20 for overcoming energy barriers during optimization is required.
\
\n 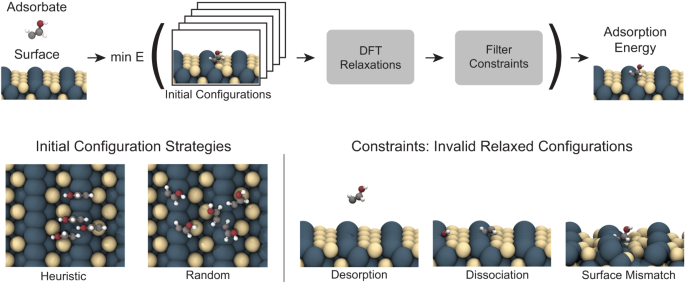
First, an adsorbate and surface combination are selected, then numerous configurations are enumerated heuristically and/or randomly. For each configuration, DFT relaxations are performed and systems are filtered based on physical constraints that ensure valid adsorption energies (i.e., desorption, dissociation, surface mismatch). The minimum energy across all configurations is identified as the adsorption energy.
Adsorption energy (ΔEads) is calculated as the energy of the adsorbate-surface (Esys) minus the energy of the clean surface (i.e., slab) (Eslab) and the energy of the gas phase adsorbate or reference species (Egas), as defined by Chanussot et al. and detailed in the Supporting Information (SI)2,4.

Relaxed adsorbate-surface structures must respect certain desired properties in order for their adsorption energy to be both accurate and valid. One example of a constraint is the adsorbate should not be desorbed, i.e., float away, from the surface in the final relaxed structure (Fig. 1, bottom right). In addition, if the adsorbate has multiple atoms it should not dissociate or break apart into multiple adsorbates because it would no longer be the adsorption energy of the molecule of interest19,21. Similarly, if the adsorbate induces significant changes in the surface compared to the clean surface, the Eslab reference would create a surface mismatch. It is important to note that if a relaxed structure breaks one of these constraints it does not necessarily mean the relaxation was inaccurate; these outcomes do arise but they lead to invalid or inaccurate adsorption energies as it has been defined.
Identifying the globally optimal adsorbate-surface configuration has historically relied on expert intuition or more recently heuristic approaches. Intuition and trial and error can be used for one-off systems of interest but it does not scale to large numbers of systems. Commonly used heuristics are often based on surface symmetry22,23. These methods have been used successfully in past descriptor-based studies9,10,24,25,26,27. More recently, a graph-based method has been used to identify unique adsorbate-surface configurations28. Nevertheless, as the complexity of the surfaces and adsorbates increase, the challenge of finding the lowest energy adsorbate-surface configuration grows substantially. This is especially challenging when the adsorbate is flexible, having multiple configurations of its own, such that there are many effective degrees of freedom in the system.
While DFT offers the ability to accurately estimate atomic forces and energies, it is computationally expensive, scaling O(N3) with the number of electrons. Evaluating a single adsorbate-surface configuration with a full DFT relaxation can take ~24 h to compute2,29. Since numerous configurations are typically explored to find the adsorption energy, all the DFT calculations involved can take days or even weeks. Hypothetically, if one were to brute-force screen 100,000 materials from the Materials Project database30 for CO2 Reduction Reaction (CO2RR) using 5 adsorbate descriptors, ~90 surfaces/material, and ~100 sites/surface, one would need ~4.5 billion CPU-days of compute, an intractable problem for even the world’s largest supercomputers. To significantly reduce the required computation, a promising approach is to accelerate the search of lowest energy adsorbate-surface configurations with machine-learned potentials.
Recently, machine learning (ML) potentials for estimating atomic forces and energies have shown significant progress on standard benchmarks while being orders of magnitude faster than DFT2,31,32,33,34,35,36. While ML accuracies on the large and diverse Open Catalyst 2020 Dataset (OC20) dataset have improved to 0.3 eV for relaxed energy estimation, an accuracy of 0.1 eV is still desired for accurate screening37. This raises the question of whether a hybrid approach that uses both DFT and ML potentials can achieve high accuracy while maintaining efficiency.
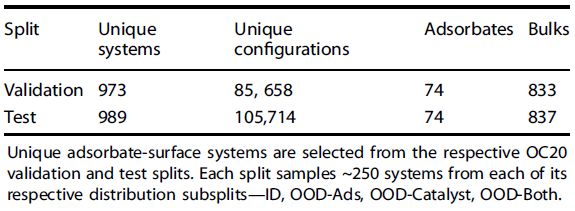
Assessing the performance of new methods for finding low-energy adsorbate-surface configurations is challenging without standardized validation data. It is common for new methods to be tested on a relatively small number of systems, which makes generalization difficult to evaluate19,28,38,39,40. While OC20 contains O(1M) “adsorption energies”, it did not sample multiple configurations per adsorbate-surface combination meaning the one configuration that was relaxed is unlikely to be the global minimum. This makes OC20 an inappropriate dataset for finding the minimum binding energy2. To address this issue, we introduce the Open Catalyst 2020-Dense Dataset (OC20-Dense). OC20-Dense includes two splits—a validation and test set. The validation set is used for development; and the test set for reporting performance. Each split consists of ~1000 unique adsorbate-surface combinations from the validation and test sets of the OC20 dataset. No data from OC20-Dense is used for training. To explore the generalizability of our approach, we take ~250 combinations from each of the four OC20 subsplits—In-Domain (ID), Out-of-Domain (OOD)-Adsorbate, OOD-Catalyst, and OOD-Both. For each combination, we perform a dense sampling of initial configurations and calculate relaxations using DFT to create a strong baseline for evaluating estimated adsorption energies.
We propose a hybrid approach to estimating adsorption energies that takes advantage of the strengths of both ML potentials and DFT. We sample a large number of potential adsorbate configurations using both heuristic and random strategies and perform relaxations using ML potentials. The best *k-*relaxed energies can then be refined using single-point DFT calculations or with full DFT relaxations. Using this approach, the appropriate trade-offs may be made between accuracy and efficiency.
Considerable research effort has been dedicated to determining the lowest energy adsorbate-surface configuration through the improvement of initial structure generation and global optimization strategies19,21,28,38,39,40,41. Peterson19 adopted the minima hopping method and developed a global optimization approach that preserves adsorbate identity using constrained minima hopping. However, the method relies entirely on DFT to perform the search, still making it computationally expensive. More recently, Jung et al.21 proposed an active learning workflow where a Gaussian process is used to run constrained minima hopping simulations. Structures generated by their simulations are verified by DFT and iteratively added to the training set until model convergence is achieved. The trained model then runs parallel constrained minima hopping simulations, a subset is refined with DFT, and the final adsorption energy identified. We note that prior attempts to use machine learning models to accelerate this process have typically relied on bespoke models for each adsorbate/catalyst combination, which limits broader applicability42,43. One possibility to greatly expand the versatility of these methods while continuing to reduce the human and computational cost is using generalizable machine learning potentials to accelerate the search for low-energy adsorbate-surface configurations.
The contributions of this work are threefold:
To evaluate methods for computing adsorption energies, we present the Open Catalyst 2020-Dense Dataset (OC20-Dense) that closely approximates the ground truth adsorption energy by densely exploring numerous configurations for each unique adsorbate-surface system. Each OC20-Dense split comprises ~1000 unique adsorbate-surface combinations spanning 74 adsorbates, 800+ inorganic bulk crystal structures, and a total of 80,000 + heuristically and randomly generated configurations. A summary of the two splits are provided in Table 1. The dataset required ~4 million CPU-hrs of compute to complete. A more detailed discussion on OC20-Dense can be found in “Methods”.
\ We report results on a wide range of GNNs previously benchmarked on OC20 to evaluate the performance of existing models on OC20-Dense. These include SchNet31, DimeNet++32,33, PaiNN44, GemNet-OC34, GemNet-OC-MD34, GemNet-OC-MD-Large34, SCN-MD-Large35, and eSCN-MD-Large45 where MD corresponds to training on OC20 and its accompanying ab initio Molecular Dynamics (MD) dataset. Models were not trained as part of this work; trained models were taken directly from previously published work and can be found at https://github.com/Open-Catalyst-Project/ocp/blob/main/MODELS.md. Of the models, (e)SCN-MD-Large and GemNet-OC-MD-Large are currently the top performers on both OC20 and Open Catalyst 2022 Dataset (OC22). Exploring the extent these trends hold for OC20-Dense will be important to informing how well progress on OC20 translates to more important downstream tasks like the one presented here.
Ideally, the ground truth for OC20-Dense would be the minimum relaxed energy over all possible configurations for each adsorbate-surface system. Since the number of possible configurations is combinatorial, the community has developed heuristic approaches to adsorbate placement on a catalyst surface22,23. When evaluating only heuristic configurations, we refer to this as DFT-Heuristic-Only (DFT-Heur). To add to the configuration space, we also uniformly sample sites on the surface at random with the adsorbate placed on each of those sites with a random rotation along the z axis and slight wobble around the x and y axis. When evaluating against both heuristic and random configurations, we refer to this as DFT-Heuristic-Only (DFT-Heur). Although computationally more expensive, this benchmark provides a more thorough search of configurations and a more accurate estimate of the adsorption energies than using only heuristic configurations, a common baseline used by the community. More details on the two benchmarks can be found in “Methods”.
We explore to what extent ML predictions can find the adsorption energy within a threshold of the DFT minimum energy, or lower. While a perfect ML surrogate to DFT will only be able to match DFT, small errors in the forces and optimizer differences have the potential to add noise to relaxations and result in configurations previously unexplored46. For each model, relaxations are performed on an identical set of adsorbate configurations. Initial configurations are created based off heuristic strategies commonly used in the literature22,23 and randomly generated configurations on the surface. ML-driven relaxations are run on all initial configurations; systems not suitable for adsorption energy calculations due to physical constraints are removed, including dissociation, desorption, and surface mismatch. An in-depth discussion on relaxation constraints can be found in “Methods”.
When evaluating performance, we define success as finding an adsorption energy within an acceptable tolerance (0.1 eV in this work2,37,46) or lower of the DFT adsorption energy in OC20-Dense. Note that the ground truth adsorption energies in OC20-Dense are an upper bound, since it is possible that a lower adsorption energy may exist. When evaluating ML-predicted adsorption energies, the results must be verified using a single-point DFT calculation, since an evaluation metric without a lower bound could be easily gamed by predicting low energies (see SI). To reliably evaluate ML we consider an ML adsorption energy successful if its within 0.1 eV of the DFT adsorption energy or lower, and a corresponding DFT single-point evaluation of the predicted ML structure is within 0.1 eV of the predicted ML energy. This ensures that a ML prediction not only found a low adsorption energy but is accurate and not artificially inflated. Results are reported in Table 2, where top OC20 models including eSCN-MD-Large and GemNet-OC-MD-Large achieve success rates of 56.52% and 48.03%, respectively. Energy MAE between ML and DFT adsorption energies are also reported in Table 2, correlating well with success rates and OC20 S2EF metrics.
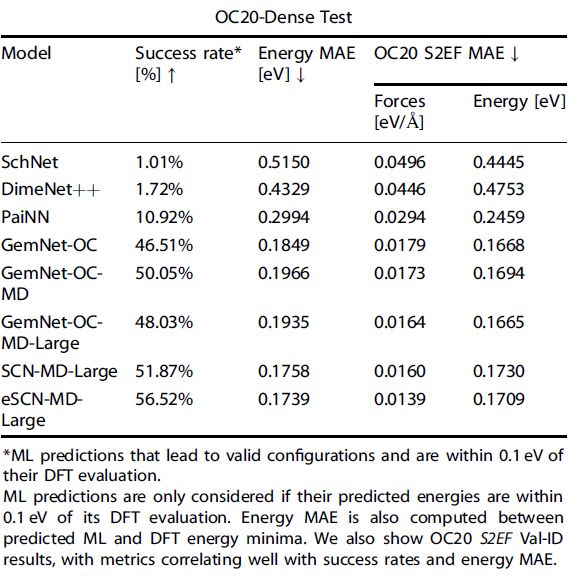
\ While the current state of models have made incredible progress37, higher success rates are needed for everyday practitioners. In a high-throughput setting where successful candidates go on to more expensive analyses or even experimental synthesis, a success rate of ~50% could result in a substantial waste of time and resources studying false positives. As model development will continue to help improve metrics, this work explores hybrid ML+DFT strategies to improve success rates at the cost of additional compute.
We introduce the AdsorbML algorithm to use ML to accelerate the adsorbate placement process (Fig. 2). For each model, we explore two strategies that incorporate ML followed by DFT calculations to determine the adsorption energy. We note that this strategy is general and can be used with any initial configuration algorithm.
Fig. 2: The AdsorbML algorithm.
Initial configurations are generated via heuristic and random strategies. ML relaxations are performed on GPUs and ranked in order of lowest to highest energy. The best k systems are passed on to DFT for either a single-point (SP) evaluation or a full relaxation (RX) from the ML-relaxed structure. Systems not satisfying constraints are filtered at each stage a relaxation is performed. The minimum is taken across all DFT outputs for the final adsorption energy.
In both approaches, the first step is to generate ML relaxations. However, rather than taking the minimum across ML-relaxed energies, we rank the systems in order of lowest to highest energy. The best k systems with lowest energies are selected and (1) DFT single-point calculations are done on the corresponding structures (ML+SP) or (2) DFT relaxations are performed from ML-relaxed structures (ML+RX). The first strategy aims to get a more reliable energy measurement of the ML-predicted relaxed structure, while the second treats ML as a pre-optimizer with DFT completing the relaxation. By taking the k lowest energy systems, we provide the model with k opportunities to arrive at acceptably accurate adsorption energy. As we increase k, more DFT compute is involved, but compared to a full DFT approach, we still anticipate significant savings. The adsorption energy for a particular system is obtained by taking the minimum of the best k DFT follow-up calculations.
In both strategies, ML energies are used solely to rank configurations, with the final energy prediction coming from a DFT calculation. While computationally, it would be ideal to fully rely on ML, the use of DFT both improves accuracy and provides a verification step to bring us more confidence in our adsorption energy predictions.
Our goal is to find comparable or better adsorption energies to those found using DFT alone in OC20-Dense. The metric we use to quantify this task is success rate, which is the percentage of OC20-Dense systems where our ML+DFT adsorption energy is within 0.1 eV or lower than the DFT adsorption energy. A validation of the ML energy is not included in these experiments since all final adsorption energies will come from at least a single DFT call, ensuring all values are valid. Another metric we track is the speedup compared to the DFT-Heur+Rand baseline. Speedup is evaluated as the ratio of DFT electronic steps used by DFT-Heur+Rand to the proposed hybrid ML+DFT strategy. A more detailed discussion on the metrics can be found in “Methods”. Unless otherwise noted, all results are reported on the test set, with results on the validation set found in the SI. When evaluating the common baseline of DFT-Heur that uses only DFT calculations, a success rate of 87.76% is achieved at a speedup of 1.81×.
The results of using single-point evaluations on ML-relaxed states are summarized in Fig. 3. eSCN-MD-Large and GemNet-OC-MD-Large achieve a success rate of 86+% at k = 5 with eSCN-MD-Large outperforming all models with a success rate of 88.27%, slightly better than the DFT-Heur baseline. Other models including SchNet and DimeNet++ do significantly worse with success metrics as low as 3.13% and 7.99%, respectively; suggesting the predicted relaxed structures are highly unfavorable. The speedups are fairly comparable across all models, ranging between 1400× and 1500× for k = 5, orders of magnitude faster than the DFT-Heur baseline. Specifically, eSCN-MD-Large and GemNet-OC-MD-Large give rise to speedups of 1384× and 1388×, respectively. If speed is of most importance, speedups as high as 6817× are achievable with k = 1 while still maintaining success rates of 82% for eSCN-MD-Large. At a more balanced trade-off, k = 3, success rates of 87.36% and 84.43% are attainable for eSCN-MD-Large and GemNet-OC-MD-Large while maintaining speedups of 2296× and 2299×, respectively. In Fig. 4, the minimum energy binding sites of several systems are compared as identified with ML+SP across different models.
For each model, DFT speedup and corresponding success rate are plotted for ML+RX and ML+SP across various best k. A system is considered successful if the predicted adsorption energy is within 0.1 eV of the DFT minimum, or lower. All success rates and speedups are relative to Random+Heuristic DFT. Heuristic DFT is shown as a common community baseline. The upper right-hand corner represents the optimal region—maximizing speedup and success rate. The point highlighted in teal corresponds to the balanced option reported in the abstract—a 87.36% success rate and 2290x speedup. A similar figure for the OC20-Dense validation set can be found in the SI.
Corresponding adsorption energies are shown in the bottom right corner of each snapshot. ML-relaxed structures have energies calculated with a DFT single-point, ML+SP. A variety of systems are shown including ones where ML finds lower, higher, and comparable adsorption energies to DFT. Notice that several of the configurations in the third and fourth systems are symmetrically equivalent, and that SchNet induces a large surface reconstruction in the third system resulting in the extremely large DFT energy (10.31 eV).
While single-point evaluations offer a fast evaluation of ML structures, performance is heavily reliant on the accuracy of the predicted relaxed structure. This is particularly apparent when evaluating the max per-atom force norm of ML-relaxed structures with DFT. SchNet and DimeNet++ have on average a max force, fmax, of 2.00 eV/Å and 1.21 eV/Å, respectively, further supporting the challenge these models face in obtaining valid relaxed structures. On the other hand, models like GemNet-OC-MD-Large and eSCN-MD-Large have an average fmax of 0.21 eV/Å and 0.15 eV/Å, respectively. While these models are a lot closer to valid relaxed structures (i.e., fmax ≤ 0.05 eV/Å), these results suggest that there is still room for further optimization. Results on DFT relaxations from ML-relaxed states are plotted in Fig. 3. eSCN-MD-Large and GemNet-OC-MD-Large outperform all models at all k values, with a 90.60% and 91.61% success rate at k = 5, respectively. Given the additional DFT costs associated with refining relaxations, speedups unsurprisingly decrease. At k = 5, we see speedups of 215× and 172× for eSCN-MD-Large and GemNet-OC-MD-Large, respectively. Both SchNet and DimeNet++ see much smaller speedups at 42× and 55×, respectively. The much smaller speedups associated with SchNet and DimeNet++ suggest that a larger number of DFT steps is necessary to relax the previously unfavorable configurations generated by the models. Conversely, eSCN-MD-Large’s much larger speedup can be attributed to the near relaxed states (average fmax ~0.15 eV/Å) it achieves in its predictions. With k = 1, speedups of 1064× are achievable while still maintaining a success rate of 84.13% for eSCN-MD-Large. At a more balanced trade-off, k = 3, success rates of 89.28% and 89.59% are attainable for eSCN-MD-Large and GemNet-OC-MD-Large while maintaining speedups of 356× and 288×, respectively.
The results suggest a spectrum of accuracy and efficiency trade-offs that one should consider when selecting a strategy. For our best models, ML+SP results are almost 8x faster than ML+RX with only a marginal performance decrease in success rates (3–4%), suggesting a worthwhile comprise. This difference is much more significant for worse models.
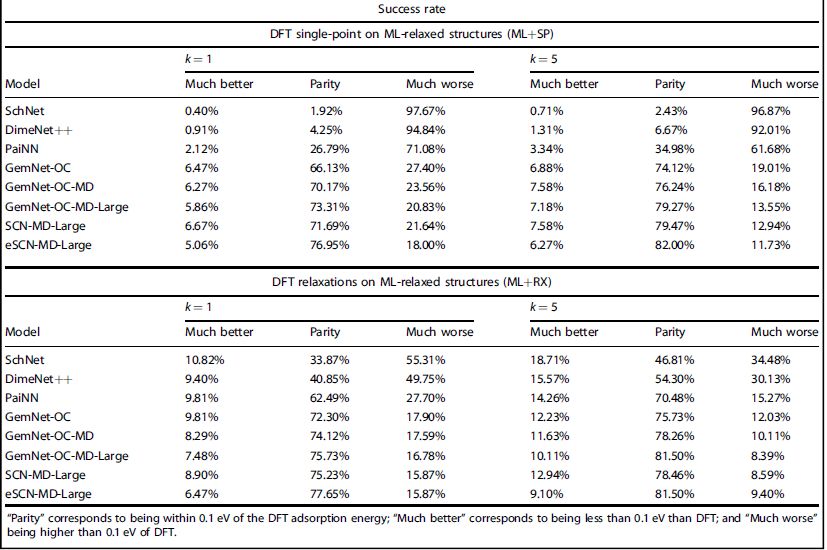
In Table 3, we measure the distribution of predictions that are much better, in parity, or much worse than the ground truth, where much better/worse corresponds to being lower/higher than 0.1 eV of the DFT adsorption energy. Across both strategies, we observe that the most accurate models do not necessarily find much better minima. For instance, at k = 5 ML+RX, eSCN-MD-Large finds 9.10% of systems with much lower minima, compared to DimeNet++ finding 15.57%. Similarly, while eSCN-MD-Large outperformed models in ML+SP, it observes less of an improvement with ML+RX; a consequence of the model arriving at a considerable local minima that a subsequent DFT relaxation has minimal benefit. This further suggests that some form of noise in models can aid in finding better minima. The full set of tabulated results for ML+SP and ML+RX experiments can be found in the SI for the OC20-Dense test and validation sets.
\
In addition, we evaluate success metrics across the different dataset subsplits. OC20-Dense uniformly samples from the four OC20 splits—ID, OOD-Adsorbate, OOD-Catalyst, and OOD-Both. Across our best models, we observe that performance remains consistent across the different distribution splits (Fig. 5). This suggests that for applications including adsorbates or surfaces that are not contained in OC20, AdsorbML still provides accurate and meaningful results. While we expect results to be consistent with OC20 where ID outperforms OOD, that is not necessarily the case here. eSCN-MD-Large, ML+SP at k = 5, achieves 86.00% on ID while a 88.35% success rate on OOD-Both, with similar trends on ML+RX. We attribute this discrepancy to the fairly small sample size per split (250). The full set of results can be found in the SI.
Fig. 5: ML+SP success rate at k = 5 across the different subsplits of the OC20-Dense test set and several baseline models.
Top performing models show marginal differences across the different distribution splits, suggesting good generalization performance to out-of-domain adsorbates and catalysts not contained in the OC20 training dataset.
\
Alongside the main results, we explore the performance of using only heuristic or only random ML configurations on the OC20-Dense validation set. Results are reported on SCN-MD-Large, for the ML+SP strategy. At k = 5, when only random configurations are used, success drops from 87.77% to 82.94%. More drastically, when only considering heuristic configurations, success drops significantly to 62.18%. This suggests that random configurations can have a larger impact. Additional results can be found in the SI.
We envision this work as an important but initial step towards reducing the computational cost of DFT for not just catalysis applications, but computational chemistry more broadly. AdsorbML provides a spectrum of accuracy and efficiency trade-offs one can choose depending on the application and computational resources available. For example, if we are interested in screening the largest number of CO2 reduction reaction catalysts possible, given a fixed compute budget, we could choose ML+SP at k = 2 for a 85% success rate while screening ~3400× more materials than would have been possible with DFT alone. On the other hand, if depth of study is more important, ML+RX is a good alternative as the structures are fully optimized with DFT and the computational speedup comes from reducing the total number of relaxation steps required. In this scenario, the ML potential serves as an efficient pre-optimization step. Even though ML models comprise a small portion of the overall compute (see SI for details), we expect these requirements to be reduced even further as more effort is placed on inference efficiency in the future.
One observation that merits additional studies is that ML models found much better minima between 5 and 15% of the time, depending on the efficiency trade-offs (Table 3). If our ML models were perfect there would be no instances with lower adsorption energies; however, implicit noise in the form of inaccurate force predictions allows the ML models to traverse unexplored regions of the potential energy surface. Exploring to what extent implicit and explicit noise46,47 impact ML relaxations and downstream tasks such as success rate is an important area of future research.
Another natural extension to this work is focusing on alternative methods of global optimization and initial configuration generation. Here, we focused on accelerating brute-force approaches to finding the global minimum by enumerating initial adsorbate-surface configurations. However, there are likely to be much more efficient approaches to global optimization such as minima hopping20, constrained optimization19,21, Bayesian optimization, or a directly learned approach. It is worth noting that while our enumeration spanned a much larger space than traditional heuristic methods, it was not exhaustive and all-encompassing. We found that increasing the number of random configurations beyond what was sampled had diminishing returns, as the change in success rate from heuristic + 80% random DFT to heuristic + 100% random DFT was only 1.6% (see the SI for more details). If screening more ML configurations continues to be advantageous, thinking about how we handle duplicate structures could further help accuracy and efficiency. We explore this briefly in the SI, where removing systems with nearly the same ML energies resulted in marginal benefit.
While current models like GemNet-OC and eSCN-MD-Large demonstrate impressive success rates on OC20-Dense, ML relaxations without any subsequent DFT are still not accurate enough for practical applications (Table 2). In order for future modeling work to address this challenge, there are a number of observations worth highlighting. First, there is a positive correlation between success rate on OC20-Dense and both the S2EF and relaxation-based Initial Structure to Relaxed Energy (IS2RE) OC20 tasks. Thus, relaxation-based IS2RE and S2EF metrics can be used as proxies when training models on OC20. Another important note on model development is that OC20-Dense’s validation set is a subset of the OC20 validation set; as a result, the OC20 validation data should not be used for training when evaluating on OC20-Dense. Lastly, it is strongly encouraged that results reported on the OC20-Dense validation set be evaluated using a DFT single-point calculation because the success rate metric can be manipulated by predicting only low energies. This could be done with as few as ~1000 single-point calculations. Alongside the release of the OC20-Dense test set, we will explore releasing a public evaluation server to ensure consistent evaluation and accessibility for DFT evaluation, if there’s interest.
Tremendous progress in datasets and machine learning for chemistry has enabled models to reach the point where they can substantially enhance and augment DFT calculations. Our results demonstrate that current state-of-the-art ML models not only accelerate DFT calculations for catalysis but enable more accurate estimates of properties that require global optimization such as adsorption energies. While the models used in this work are best suited for idealized adsorbate-surface catalysts, fine-tuning strategies can help enable applications to other chemistries including metal-organic frameworks and zeolites29. Similarly, the models used in this work were trained on a consistent level of DFT theory (revised Perdew–Burke–Ernzerhof, no spin polarization), generalizing to other functionals and levels of theory could also be enabled with fine-tuning or other training strategies. Given the timeline of ML model development, these results would not have been possible even a couple of years ago. We anticipate this work will accelerate the large-scale exploration of complex adsorbate-surface configurations for a broad range of chemistries and applications. Generalizing these results to more diverse materials and molecules without reliance on DFT is a significant community challenge moving forward.
The evaluation of adsorption energy estimations requires a ground truth dataset that thoroughly explores the set of potential adsorption configurations. While OC20 computed adsorption energies for O(1M) systems, the energies may not correspond to the minimum of that particular adsorbate-surface combination. More specifically, for a given catalyst surface, OC20 considers all possible adsorption sites but only places the desired adsorbate on a randomly selected site in one particular configuration. The tasks presented by OC20 enabled the development of more accurate machine-learned potentials for catalysis34,35,47,48,49, but tasks like IS2RE, although correlate well, are not always sufficient when evaluating performance as models are penalized when finding a different, lower energy minima—a more desirable outcome. As a natural extension to OC20’s tasks, we introduce OC20-Dense to investigate the performance of models to finding the adsorption energy.
OC20-Dense is constructed to closely approximate the adsorption energy for a particular adsorbate-surface combination. To accomplish this, a dense sampling of initial adsorption configurations is necessary. OC20-Dense consists of two splits—a validation and test set. For each split, ~1000 unique adsorbate-surface combinations from the respective OC20 validation/test set are sampled. A uniform sample is then taken from each of the subsplits (ID, OOD-Adsorbate, OOD-Catalyst, OOD-Both) to explore the generalizability of models on this task. For each adsorbate-surface combination, two strategies were used to generate initial adsorbate configurations: heuristic and random. The heuristic strategy serves to represent the average catalysis researcher, where popular tools like CatKit23 and Pymatgen22 are used to make initial configurations. Given an adsorbate and surface, Pymatgen enumerates all symmetrically identical sites, an adsorbate is placed on the site, and a random rotation along the z axis followed by slight wobbles in the x and y axis is applied to the adsorbate. While heuristic strategies seek to capture best practices, they do limit the possible search space with no guarantee that the true minimum energy is selected. To address this, we also randomly enumerate M sites on the surface and then place the adsorbate on top of the selected site. In this work, M = 100 is used and a random rotation is applied to the adsorbate in a similar manner. In both strategies, we remove unreasonable configurations—adsorbates not placed on the slab and/or placed too deep into the surface. DFT relaxations were then run on all configurations with the results filtered to remove those that desorb, dissociate or create surface mismatches. The minimum energy across those remaining is considered the adsorption energy. While random is meant to be a more exhaustive enumeration, it is not perfect and could likely miss some adsorbate configurations. The OC20-Dense validation set was created in a similar manner but contained notable differences, details are outlined in the SI.
The OC20-Dense test set comprises 989 unique adsorbate+surface combinations spanning 74 adsorbates and 837 bulks. Following the dense sampling, a total of 56,282 heuristic and 49,432 random configurations were calculated with DFT. On average, there were 56 heuristic and 50 random configurations per system (note—while M = 100 random sites were generated, less sites were available upon filtering.) In total, ~4 million hours of compute were used to create the dataset. All DFT calculations were performed using Vienna Ab initio Simulation Package (VASP)50,51,52,53. A discussion on DFT settings and details can be found in the SI.
To sufficiently track progress, we propose two primary metrics—success rate and DFT speedup. Success rate is the proportion of systems in which a strategy returns energy that is within σ, or lower of the DFT adsorption energy. A margin of σ = 0.1 eV is selected as the community is often willing to tolerate a small amount of error for practical relevance2,37. Tightening this threshold for improved accuracy is a foreseeable step once models+strategies saturate. While high success rates are achievable with increased DFT compute, we use DFT speedup as a means to evaluate efficiency. Speedup is measured as the ratio of DFT electronic, or self-consistency (SC), steps used by DFT-Heur+Rand and the proposed strategy. Electronic steps are used as we have seen them correlate better with DFT compute time than the number of ionic, or relaxation, steps. DFT calculations that failed or resulted in invalid structures were included in speedup evaluation as they still represent realized costs in screening. We chose not to include compute time in this metric as results are often hardware-dependent and can make comparing results unreliable. ML relaxation costs are excluded from this metric as hardware variance along with CPU+GPU timings make it nontrivial to normalize. While ML timings are typically negligible compared to the DFT calculations, a more detailed analysis of ML timings can be found in the SI. Metrics are reported against the rigorous ground truth—DFT-Heur+Rand, and compared to a community heuristic practice—DFT-Heur. Formally, metrics are defined in Equs. (2) and (3).
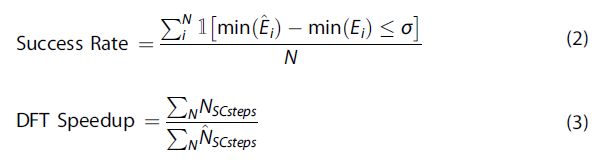
where i is an adsorbate-surface system, N the total number of unique systems, 𝟙 is the indicator function, is the proposed strategy, NSCsteps is the number of self-consistency, or electronic steps, and is the minimum energy across all configurations of that particular system. For both metrics, higher is better.
It is possible that some of the adsorbate-surface configurations we consider may relax to a state that are necessary to discard in our analysis. For this work, we considered three such scenarios: (1) desorption, (2) dissociation, and (3) significant adsorbate-induced surface changes. Desorption, the adsorbate molecule not binding to the surface, is far less detrimental because desorbed systems are generally high energy. Still, it is useful to understand when none of the configurations considered have actually adsorbed to the surface. Dissociation, the breaking of an adsorbate molecule into different atoms or molecules, is problematic because the resulting adsorption energy is no longer consistent with what is of interest, i.e., the adsorption energy of a single molecule, not two or more smaller molecules. Including these systems can appear to correspond to lower adsorption energies, but due to the energy not representing the desired system it can result in false positives. Lastly, we also discard systems with significant adsorbate-induced surface changes because, just as with dissociation, we are no longer calculating the energy of interest. In calculating adsorption energy, a term is included for the energy of the clean, relaxed surface. An underlying assumption in this calculation is that the corresponding adsorbate-surface system’s resulting surface must be comparable to the corresponding clean surface, otherwise this referencing scheme fails and the resulting adsorption energy is inaccurate. For each of these instances, we developed detection methods as a function of neighborhood connectivity, distance information, and atomic covalent radii. Depending on the user’s application, one may decide to tighten the thresholds defined within. Details on each of the detection methods and further discussion can be found in the SI.
The full open dataset is provided at https://github.com/Open-Catalyst-Project/AdsorbML.
All accompanying code is provided at https://github.com/Open-Catalyst-Project/AdsorbML.
\ \
:::info This paper is available on nature under CC by 4.0 Deed (Attribution 4.0 International) license.
:::
\
2026-03-10 14:30:07
:::info
:::
\
Many critics raise concerns about the prevalence of ‘echo chambers’ on social media and their potential role in increasing political polarization. However, the lack of available data and the challenges of conducting large-scale field experiments have made it difficult to assess the scope of the problem1,2. Here we present data from 2020 for the entire population of active adult Facebook users in the USA showing that content from ‘like-minded’ sources constitutes the majority of what people see on the platform, although political information and news represent only a small fraction of these exposures. To evaluate a potential response to concerns about the effects of echo chambers, we conducted a multi-wave field experiment on Facebook among 23,377 users for whom we reduced exposure to content from like-minded sources during the 2020 US presidential election by about one-third. We found that the intervention increased their exposure to content from cross-cutting sources and decreased exposure to uncivil language, but had no measurable effects on eight preregistered attitudinal measures such as affective polarization, ideological extremity, candidate evaluations and belief in false claims. These precisely estimated results suggest that although exposure to content from like-minded sources on social media is common, reducing its prevalence during the 2020 US presidential election did not correspondingly reduce polarization in beliefs or attitudes.
\
Increased partisan polarization and hostility are often blamed on online echo chambers on social media3,4,5,6,7, a concern that has grown since the 2016 US presidential election8,9,10. Platforms such as Facebook are thought to fuel extremity by repeatedly showing people congenial content from like-minded sources and limiting exposure to counterarguments that could promote moderation and tolerance11,12,13. Similarly, identity-reinforcing communication on social media could strengthen negative attitudes toward outgroups and bolster attachments to ingroups14.
To assess how often people are exposed to congenial content on social media, we use data from all active adult Facebook users in the USA to analyse how much of what they see on the platform is from sources that we categorize as sharing their political leanings (which we refer to as content from like-minded sources; see Methods, ‘Experimental design’). With a subset of consenting participants, we then evaluate a potential response to concerns about the effects of echo chambers by conducting a large-scale field experiment reducing exposure to content from like-minded sources on Facebook. This research addresses three major gaps in our understanding of the prevalence and effects of exposure to congenial content on social media.
First, we have no systematic measures of content exposure on platforms such as Facebook, which are largely inaccessible to researchers2. Web traffic data suggest that relatively few Americans have heavily skewed information diets15,16,17,18, but less is known about what they see on social media. Prior observational studies of information exposure on platforms focus on Twitter, which is used by only 23% of the public19,20,21,22, or the news diet of the small minority of active adult users in the US who self-identified as conservative or liberal on Facebook in 2014–201523. Without access to behavioural measures of exposure, studies must instead rely on survey self-reports that are prone to measurement error24,25.
Second, although surveys find associations between holding polarized attitudes and reported consumption of like-minded news26,27, few studies provide causal evidence that consuming like-minded content leads to lasting polarization. These observed correlations may be spurious given that the people with extreme political views are more likely to consume like-minded content28,29. In addition, although like-minded information can polarize30,31,32, most experimental tests of theories about potential echo chamber effects are brief and use simulated content, making it difficult to know whether these findings generalize to real-world environments. Previous experimental work also raises questions about whether such polarizing effects are common18,33, how quickly they might decay18,33, and whether they are concentrated among people who avoid news and political content28.
Finally, reducing exposure to like-minded content may not lead to a corresponding increase in exposure to content from sources with different political leanings (which we refer to as cross-cutting) and could also have unintended consequences. Social media feeds are typically limited to content from accounts that users already follow, which include few that are cross-cutting and many that are non-political22. As a result, reducing exposure to like-minded sources may increase the prevalence of content from sources that are politically neutral rather than uncongenial. Furthermore, if content from like-minded sources is systematically different (such as in its tone or topic), reducing exposure to such content may also have other effects on the composition of social media feeds. Reducing exposure to like-minded content could also induce people to seek out such information elsewhere online (that is, not on Facebook34).
In this study, we measure the prevalence of exposure to content from politically like-minded sources among active adult Facebook users in the US. We then report the results of an experiment estimating the effects of reducing exposure to content from politically like-minded friends, Pages and groups among consenting Facebook users (n = 23,377) for three months (24 September to 23 December 2020). By combining on-platform behavioural data from Facebook with survey measures of attitudes collected before and after the 2020 US presidential election, we can determine how reducing exposure to content from like-minded sources changes the information people see and engage with on the platform, as well as test the effects over time of reducing exposure to these sources on users’ beliefs and attitudes.
This project is part of the US 2020 Facebook and Instagram Election Study. Although both Meta researchers and academics were part of the research team, the lead academic authors had final say on the analysis plan, collaborated with Meta researchers on the code implementing the analysis plan, and had control rights over data analysis decisions and the manuscript text. Under the terms of the collaboration, Meta could not block any results from being published. The academics were not financially compensated and the analysis plan was preregistered prior to data availability (https://osf.io/3sjy2); further details are provided in Supplementary Information, section 4.8.
We report several key results. First, the majority of the content that active adult Facebook users in the US see comes from like-minded friends, Pages and groups, although only small fractions of this content are categorized as news or are explicitly about politics. Second, we find that an experimental intervention reducing exposure to content from like-minded sources by about a third reduces total engagement with that content and decreases exposure to content classified as uncivil and content from sources that repeatedly post misinformation. However, the intervention only modestly increases exposure to content from cross-cutting sources. We instead observe a greater increase in exposure to content from sources that are neither like-minded nor cross-cutting. Moreover, although total engagement with content from like-minded sources decreased, the rate of engagement with it increased (that is, the probability of engaging with the content from like-minded sources that participants did see was higher).
Furthermore, despite reducing exposure to content from like-minded sources by approximately one-third over a period of weeks, we find no measurable effects on 8 preregistered attitudinal measures, such as ideological extremity and consistency, party-congenial attitudes and evaluations, and affective polarization. We can confidently rule out effects of ±0.12 s.d. or more on each of these outcomes. These precisely estimated effects do not vary significantly by respondents’ political ideology (direction or extremity), political sophistication, digital literacy or pre-treatment exposure to content that is political or from like-minded sources.
Our analysis of platform exposure and behaviour considers the population of US adult Facebook users (aged 18 years and over). We focus primarily on those who use the platform at least once per month, who we call monthly active users. Aggregated usage levels are measured for the subset of US adults who accessed Facebook at least once in the 30 days preceding 17 August 2020 (see Supplementary Information, section 4.9.4 for details). During the third and fourth quarters of 2020, which encompass this interval as well as the study period for the experiment reported below, 231 million users accessed Facebook every month in the USA.
We used an internal Facebook classifier to estimate the political leaning of US adult Facebook users (see Supplementary Information, section 2.1 for validation and section 1.3 for classifier details; Extended Data Fig. 1 shows the distribution of predicted ideology score by self-reported ideology, party identification and approval of former president Donald Trump). The classifier produces predictions at the user level ranging from 0 (left-leaning) to 1 (right-leaning). Users with predicted values greater than 0.5 were classified as conservative and otherwise classified as liberal, enabling us to analyse the full population of US active adult Facebook users. A Page’s score is the mean score of the users who follow the Page and/or share its content; a group’s score is the mean score of group members and/or users who share its content. We classified friends, Pages or groups as liberal if their predicted value was 0.4 or below and conservative if it was 0.6 or above. This approach allows us to identify sources that are clearly like-minded or cross-cutting with respect to users (friends, Pages and groups with values between 0.4 and 0.6 were treated as neither like-minded nor cross-cutting).
We begin by assessing the extent to which US Facebook users are exposed to content from politically like-minded users, Pages and groups in their Feed during the period 26 June to 23 September 2020 (see Supplementary Information, section 4.2, for measurement details). We present estimates of these quantities among US adults who logged onto Facebook at least once in the 30 days preceding 17 August 2020.
We find that the median Facebook user received a majority of their content from like-minded sources—50.4% versus 14.7% from cross-cutting sources (the remainder are from friends, Pages and groups that we classify as neither like-minded nor cross-cutting). Like-minded exposure was similar for content classified as ‘civic’ (that is, political) or news (see Supplementary Information, section 4.3 for details on the classifiers used in this study). The median user received 55% of their exposures to civic content and 47% of their exposures to news content from like-minded sources (see Extended Data Table 1 for exact numbers and Supplementary Fig. 3 for a comparison with our experimental participants). Civic and news content make up a relatively small share of what people see on Facebook, however (medians of 6.9% and 6.7%, respectively; Supplementary Table 11).
However, patterns of exposure can vary substantially between users. Figure 1 provides the distribution of exposure to sources that were like-minded, cross-cutting or neither for all content, civic content and news content for Facebook users.
a, The distribution of the exposure of monthly active adult Facebook users in the USA to content from like-minded sources, cross-cutting sources, and those that fall into neither category in their Facebook Feed. Estimates are presented for all content, content classified as civic (that is, political) and news. b, Cumulative distribution functions of exposure levels by source type. Source and content classifications were created using internal Facebook classifiers (Supplementary Information, section 1.3).
Despite the prevalence of like-minded sources in what people see on Facebook, extreme echo chamber patterns of exposure are infrequent. Just 20.6% of Facebook users get over 75% of their exposures from like-minded sources. Another 30.6% get 50–75% of their exposures on Facebook from like-minded sources. Finally, 25.6% get 25–50% of their exposures from like-minded sources and 23.1% get 0–25% of their exposures from like-minded sources. These proportions are similar for the subsets of civic and news content (Extended Data Table 1). For instance, like-minded sources are responsible for more than 75% of exposures to these types of content for 29% and 20.6% of users, respectively.
However, exposure to content from cross-cutting sources is also relatively rare among Facebook users. Only 32.2% have a quarter or more of their Facebook Feed exposures coming from cross-cutting sources (31.7% and 26.9%, respectively, for civic and news content).
These patterns of exposure are similar for the most active Facebook users, a group that might be expected to consume content from congenial sources more frequently than other groups. Among US adults who used Facebook at least once each day in the 30 days preceding 17 August 2020, 53% of viewed content was from like-minded sources versus 14% for cross-cutting sources, but only 21.1% received more than 75% of their exposures from like-minded sources (see Extended Data Fig. 2 and Extended Data Table 2).
These results are not consistent with the worst fears about echo chambers. Even among those who are most active on the platform, only a minority of Facebook users are exposed to very high levels of content from like-minded sources. However, the data clearly indicate that Facebook users are much more likely to see content from like-minded sources than they are to see content from cross-cutting sources.
To examine the effects of reducing exposure to information from like-minded sources, we conducted a field experiment among consenting US adult Facebook users. This study combines data on participant behaviour on Facebook with their responses to a multi-wave survey, a design that allows us to estimate the effects of the treatment on the information that participants saw, their on-platform behaviour and their political attitudes (Methods).
Participants in the treatment and control groups were invited to complete five surveys before and after the 2020 presidential election assessing their political attitudes and behaviours. Two surveys were fielded pre-treatment: wave 1 (31 August to 12 September) and wave 2 (8 September to 23 September). The treatment ran from 24 September to 23 December. During the treatment period, 3 more surveys were administered: wave 3 (9 October to 23 October), wave 4 (4 November to 18 November) and wave 5 (9 December to 23 December). All covariates were measured in waves 1 and 2 and all survey outcomes were measured after the election while treatment was still ongoing (that is, in waves 4 and/or 5). Throughout the experiment, we also collected data on participant content exposure and engagement on Facebook.
In total, the sample for this study consists of 23,377 US-based adult Facebook users who were recruited via survey invitations placed at the top of their Facebook feeds in August and September 2020, provided informed consent to participate and completed at least one post-election survey wave (see Supplementary Information, sections 4.5 and 4.9).
For participants assigned to treatment, we downranked all content (including, but not limited to, civic and news content) from friends, groups and Pages that were predicted to share the participant’s political leaning (for example, all content from conservative friends and groups and Pages with conservative audiences was downranked for participants classified as conservative; see Supplementary Information, section 1.1).
We note three important features of the design of the intervention. First, the sole objective of the intervention was to reduce exposure to content from like-minded sources. It was not designed to directly alter any other aspect of the participants’ feeds. Content from like-minded sources was downranked using the largest possible demotion strength that a pre-test demonstrated would reduce exposure without making the Feed nearly empty for some users, which would have interfered with usability and thus confounded our results; see Supplementary Information, section 1.1. Second, our treatment limited exposure to all content from like-minded sources, not just news and political information. Because social media platforms blur social and political identities, even content that is not explicitly about politics can still communicate relevant cues14,35. Also, because politics and news account for a small fraction of people’s online information diets18,36,37, restricting the intervention to political and/or news content would yield minimal changes to some people’s Feeds. Third, given the associations between polarized attitudes and exposure to politically congenial content that have been found in prior research, we deliberately designed an intervention that reduces rather than increases exposure to content from like-minded sources to minimize ethical concerns.
The observed effects of the treatment on exposure to content from like-minded sources among participants are plotted in Fig. 2. As intended, the treatment substantially reduced exposure to content from like-minded sources relative to the pre-treatment period. During the treatment period of 24 September to 23 December 2020, average exposure to content from like-minded sources declined to 36.2% in the treatment group while remaining stable at 53.7% in the control group (P < 0.01). Exposure levels were relatively stable during the treatment period in both groups, except for a brief increase in treatment group exposure to content from like-minded sources on 2 November and 3 November, owing to a technical problem in the production servers that implemented the treatment (see Supplementary Information, section 4.11 for details).
Mean day-level share of respondent views of content from like-minded sources by experimental group between 1 July and 23 December 2020. Sources are classified as like-minded on the basis of estimates from an internal Facebook classifier at the individual level for users and friends, and at the audience level for Pages and groups. W1–W5 indicate survey waves 1 to 5; shading indicates wave duration. Extended Data Fig. 3 provides a comparable graph of views of content from cross-cutting sources. Note: exposure levels increased briefly on 2 and 3 November owing to a technical problem; details are provided in Supplementary Information, section 4.11.
Our core findings are visualized in Fig. 3, which shows the effects of the treatment on exposure to different types of content during the treatment period (Fig. 3a), the total number of actions engaging with that content (Fig. 3b), the rate of engagement with content conditional on exposure to it (Fig. 3c), and survey measures of post-election attitudes (Fig. 3d; Extended Data Table 3 reports the corresponding point estimates from Fig. 3; Supplementary Information, section 1.4 provides measurement details).
Average treatment effects of reducing exposure to like-minded sources in the Facebook Feed from 24 September to 23 December 2020. a–c, Sample average treatment effects (SATE) on Feed exposure and engagement. b, Total engagement (for content, the total number of engagement actions). c, Engagement rate (the probability of engaging conditional on exposure). d, Outcomes of surveys on attitudes, with population average treatment effects (PATEs) estimated using survey weights. Supplementary Information 1.4 provides full descriptions of all outcome variables. Non-bolded outcomes that appear below a bolded header are part of that category. For example, in d, ‘issue positions’, ‘group evaluations’ and ‘vote choice and candidate evaluations’ appear below ‘ideologically consistent views’, indicating that all are measured such that higher values indicate greater ideological consistency. Survey outcome measures are standardized scales averaged across surveys conducted between 4 November and 18 November 2020 and/or 9 December and 23 December 2020. Point estimates are provided in Extended Data Table 3. Sample average treatment effect estimates on attitudes are provided in Extended Data Fig. 4. All effects estimated using ordinary least squares (OLS) with robust standard errors and follow the preregistered analysis plan. Points marked with asterisks indicate findings that are significant (P P > 0.05 (all tests are two-sided). P values are false-discovery rate (FDR)-adjusted (Supplementary Information, section 1.5.4).
As seen in Fig. 3a, the reduction in exposure to content from like-minded sources from 53.7% to 36.2% represents a difference of 0.77 s.d. (95% confidence interval: −0.80, −0.75). Total views per day also declined by 0.05 s.d. among treated participants (95% confidence interval: −0.08, −0.02). In substantive terms, the average control group participant had 267 total content views on a typical day, of which 143 were from like-minded sources. By comparison, 92 out of 255 total content views for an average participant in the treatment condition were from like-minded sources on a typical day (Supplementary Tables 33 and 40).
This reduction in exposure to information from like-minded sources, however, did not lead to a symmetrical increase in exposure to information from cross-cutting sources, which increased from 20.7% in the control group to 27.9% in the treatment group, a change of 0.43 s.d. (95% confidence interval: 0.40, 0.46). Rather, respondents in the treatment group saw a greater relative increase in exposure to content from sources classified as neither like-minded nor cross-cutting. Exposure to content from these sources increased from 25.6% to 35.9%, a change of 0.68 s.d. (95% confidence interval: 0.65, 0.71).
Figure 3a also indicates that reducing exposure to content from like-minded sources reduced exposure to content classified as containing one or more slur words by 0.04 s.d. (95% confidence interval: −0.06, −0.02), content classified as uncivil by 0.15 s.d. (95% confidence interval: −0.18, −0.13), and content from misinformation repeat offenders (sources identified by Facebook as repeatedly posting misinformation) by 0.10 s.d. (95% confidence interval: −0.13, −0.08). Substantively, the average proportion of exposures decreased from 0.034% to 0.030% for content with slur words (a reduction of 0.01 views per day on average), from 3.15% to 2.81% for uncivil content (a reduction of 1.24 views per day on average), and from 0.76% to 0.55% for content from misinformation repeat offenders (a reduction of 0.62 views per day on average). Finally, the treatment reduced exposure to civic content (−0.05 s.d.; 95% confidence interval: −0.08, −0.03) and increased exposure to news content (0.05 s.d., 95% confidence interval: 0.02, 0.07) (see Supplementary Information, section 1.3 for details on how uncivil content, content with slur words and misinformation repeat offenders are measured).
We next consider the effects of the treatment (reducing exposure to content from like-minded sources) on how participants engage with content on Facebook. We examine content engagement in two ways, which we call ‘total engagement’ and ‘engagement rate’. Figure 3b presents the effects of the treatment on total engagement with content—the total number of actions taken that we define as ‘passive’ (clicks, reactions and likes) or ‘active’ (comments and reshares) forms of engagement. Figure 3c presents effects of the treatment on the engagement rate, which is the probability of engaging with the content that participants did see (that is, engagement conditional on exposure). These two measures do not necessarily move in tandem: as we report below, participants in the treatment group have less total engagement with content from like-minded sources (since they are by design seeing much less of it), but their rate of engagement is higher than that of the control group, indicating that they interacted more frequently with the content from like-minded sources to which they were exposed.
Figure 3b shows that the intervention had no significant effect on the time spent on Facebook (−0.02 s.d., 95% confidence interval: −0.050, 0.004) but did decrease total engagement with content from like-minded sources. This decrease was observed for both passive and active engagement with content from like-minded sources, which decreased by 0.24 s.d. (95% confidence interval: −0.27, −0.22) and 0.12 s.d. (95% confidence interval: −0.15, −0.10), respectively. Conversely, participants in the treatment condition engaged more with cross-cutting sources—passive and active engagement increased by 0.11 s.d. (95% confidence interval: 0.08, 0.14) and 0.04 s.d. (95% confidence interval: 0.01, 0.07), respectively. Finally, we observe decreased passive engagement but no decrease in active engagement with content from misinformation repeat offenders (for passive engagement, −0.07 s.d., 95% confidence interval: −0.10, −0.04; for active engagement, −0.02 s.d., 95% confidence interval: −0.05, 0.01).
When people in the treatment group did see content from like-minded sources in their Feed, however, their rate of engagement was higher than in the control group. Figure 3c shows that, conditional on exposure, passive and active engagement with content from like-minded sources increased by 0.04 s.d. (95% confidence interval: 0.02, 0.06) and 0.13 s.d. (95% confidence interval: 0.08, 0.17), respectively. Furthermore, although treated participants saw more content from cross-cutting sources overall, they were less likely to engage with the content that they did see: passive engagement decreased by 0.06 s.d. (95% confidence interval: −0.07, −0.04) and active engagement decreased by 0.02 s.d. (95% confidence interval: −0.04, −0.01). The number of content views per days active on the platform also decreased slightly (–0.05 s.d., 95% confidence interval: −0.08, −0.02).
Finally, we examine the causal effects of reducing exposure to like-minded sources on Facebook on a range of attitudinal outcomes measured in post-election surveys (Fig. 3d). As preregistered, we apply survey weights to estimate PATEs and adjust P values for these outcomes to control the false discovery rate (see Supplementary Information, sections 1.5.4 and 4.7 for details). We observe a consistent pattern of precisely estimated results near zero (open circles in Fig. 3d) for the outcome measures we examine: affective polarization; ideological extremity; ideologically consistent issue positions, group evaluations and vote choice and candidate evaluations; and partisan-congenial beliefs and views about election misconduct and outcomes, views toward the electoral system and respect for election norms (see Supplementary Information, section 1.4 for measurement details). In total, we find that 7 out of the 8 point estimates for our primary outcome measures have values of ±0.03 s.d. or less and are precisely estimated (exploratory equivalence bounds: ±0.1 s.d.; Supplementary Table 60), reflecting high levels of observed power. For instance, the minimum detectable effect in the sample for affective polarization is 0.019 s.d. The eighth result is a less precise null for ideologically consistent vote choice and candidate evaluations (0.056 s.d., equivalence bounds: 0.001, 0.111.)
We also tested the effects of reducing exposure to content from like-minded sources on a variety of attitudinal measures for which we had weaker expectations. Using an exploratory equivalence bounds test, we can again confidently rule out effects of ±0.18 s.d. for these preregistered research questions across 18 outcomes, which are reported in Extended Data Fig. 5 and Supplementary Table 47. An exploratory equivalence bounds analysis also rules out a change in self-reported consumption of media outlets outside of Facebook that we categorized as like-minded of ±0.07 s.d. (Supplementary Tables 59 and 67).
Finally, we examine heterogeneous treatment effects on the attitudes reported in Fig. 3d and the research questions across a number of preregistered characteristics: respondents’ political ideology (direction or extremity), political sophistication, digital literacy, pre-treatment exposure to content that is political, and pre-treatment levels of like-minded exposure both as a proportion of respondents’ information diet and as the total number of exposures (see Supplementary Information, section 3.9). None of the 272 preregistered subgroup treatment effect estimates for our primary outcomes are statistically significant after adjustment to control the false discovery rate. Similarly, an exploratory analysis finds no evidence of heterogeneous effects by age or number of years since joining Facebook (see Supplementary Information, section 3.9.5).
Many observers share the view that Americans live in online echo chambers that polarize opinions on policy and deepen political divides6,7. Some also argue that social media platforms can and should address this problem by reducing exposure to politically like-minded content38. However, both these concerns and the proposed remedy are based on largely untested empirical assumptions.
Here we provide systematic descriptive evidence of the extent to which social media users disproportionately consume content from politically congenial sources. We find that only a small proportion of the content that Facebook users see explicitly concerns politics or news and relatively few users have extremely high levels of exposure to like-minded sources. However, a majority of the content that active adult Facebook users in the US see on the platform comes from politically like-minded friends or from Pages or groups with like-minded audiences (mirroring patterns of homophily in real-world networks15,39). This content has the potential to reinforce partisan identity even if it is not explicitly political14.
Our field experiment also shows that changes to social media algorithms can have marked effects on the content that users see. The intervention substantially reduced exposure to content from like-minded sources, which also had the effect of reducing exposure to content classified as uncivil and content from sources that repeatedly post misinformation. However, the tested changes to social media algorithms cannot fully counteract users’ proclivity to seek out and engage with congenial information. Participants in the treatment group were exposed to less content from like-minded sources but were actually more likely to engage with such content when they encountered it.
Finally, we found that reducing exposure to content from like-minded sources on Facebook had no measurable effect on a range of political attitudes, including affective polarization, ideological extremity and opinions on issues; our exploratory equivalence bounds analyses allow us to confidently rule out effects of ±0.12 s.d. We were also unable to reject the null hypothesis in any of our tests for heterogeneous treatment effects across many distinct subgroups of participants.
There are several potential explanations for this pattern of null results. First, congenial political information and partisan news—the types of content that are thought to drive polarization—account for a fraction of what people see on Facebook. Similarly, social media consumption represents a small fraction of most people’s information diets37, which include information from many sources (for example, friends, television and so on). Thus, even large shifts in exposure on Facebook may be small as a share of all the information people consume. Second, persuasion is simply difficult—the effects of information on beliefs and opinion are often small and temporary and may be especially difficult to change during a contentious presidential election33,40,41,42,43. Finally, we sought to decrease rather than increase exposure to like-minded information for ethical reasons. Although the results suggest that decreasing exposure to information from like-minded sources has minimal effects on attitudes, the effects of such exposure may not be symmetrical. Specifically, decreasing exposure to like-minded sources might not reduce polarization as much as increasing exposure would exacerbate it.
We note several other areas for future research. First, we cannot rule out the many ways in which social media use may have affected participants’ beliefs and attitudes prior to the experiment. In particular, our design cannot capture the effects of prior Facebook use or cumulative effects over years; experiments conducted over longer periods and/or among new users are needed (we note, however, that find no evidence of heterogeneous effects by age or years since joining Facebook). Second, although heterogeneous treatment effects are non-existent in our data and rare in persuasion studies in general44, the sample’s characteristics and behaviour deviate in some respects from the Facebook user population. Future research should examine samples that more closely reflect Facebook users and/or oversample subgroups that may be particularly affected by like-minded content. Third, only a minority of Facebook users occupy echo chambers yet the reach of the platform means that the group in question is large in absolute terms. Future research should seek to better understand why some people are exposed to large quantities of like-minded information and the consequences of this exposure. Fourth, our study examines the prevalence of echo chambers using the estimated political leanings of users, Pages, and groups who share content on social networks. We do not directly measure the slant of the content that is shared; doing so would be a valuable contribution for future research. Finally, replications in other countries with different political systems and information environments will be essential to determine how these results generalize.
Ultimately, these findings challenge popular narratives blaming social media echo chambers for the problems of contemporary American democracy. Algorithmic changes that decrease exposure to like-minded sources do not seem to offer a simple solution for those problems. The information that we see on social media may be more a reflection of our identity than a source of the views that we express.
Participants in our field experiment are 73.3% white, 57.3% female, relatively highly educated (50.7% have a college degree), and 54.1% self-identify as Democrats or lean Democrat. They also use Facebook more frequently than the general Facebook population and are exposed to more content from politically like-minded sources (the phenomenon of interest), including civic and news content from like-minded sources, than are other Facebook users (Supplementary Tables 2 and 4–10). Our treatment effect estimates on attitudes therefore apply survey weights created to reflect the population of adult monthly active Facebook users who were eligible for recruitment (see Supplementary Information, section 4.7). The demographic characteristics of the weighted sample are similar to those of self-reported Facebook users in an AmeriSpeak probability sample (Extended Data Table 5).
Respondents were assigned to treatment or control with equal probability using block randomization (see Supplementary Information, section 4.5 for details; participants were blind to assignment). The Feed of participants in the control condition was not systematically altered. Owing to the difficulty of measuring the political leaning or slant of many different types of content at scale, we instead varied exposure to content based on the estimated political leaning of the source of the information. Using a Facebook classifier, we estimate the political leaning of other users directly (see Supplementary Information, section 1.3 for details). Building on prior research16,17,23,45,46, we estimate the political leanings of Pages and groups using the political leanings of their audience (group members and Page followers). We classify all users as liberal or conservative using a binary threshold to maximize statistical power, but results are consistent when we exclude respondents with classifications between 0.4 and 0.6 in an exploratory analysis (see Supplementary Information, sections 3.10 and 3.11).
We designed the study to provide statistical power to detect small effects. For instance, our power calculations showed that a final sample size of 24,480 would generate a minimum detectable effect of 1.6 percentage points on vote choice among likely voters (see Supplementary Information, section 4.5).
Randomization was successful: the treatment and control groups do not differ in their demographic characteristics at a rate above what would be expected by chance (see Supplementary Table 5). In total, 82.6% of experimental participants completed at least one post-election survey (23,377 valid completions out of 28,296 eligible participants; see Supplementary Information, section 2.1.3). The final sample consists of respondents who completed at least one post-election survey and did not delete their account or withdraw from the study before data were de-identified. Those who left the study prior to completing a post-election survey do not significantly differ from our final sample (see Supplementary Information, sections 2.1 and 1.2).
All analyses in the main text and in the Supplementary Information follow the preregistration filed at the Open Science Foundation (https://osf.io/3sjy2; see Supplementary Information, section 4.10 except for deviations reported in Supplementary Information, section 4.11). Treatment effect estimates use OLS with robust standard errors and control for covariates selected using the least absolute shrinkage and selection operator47 (see Supplementary Information, section 1.5.1). As preregistered, our tests of treatment effects on attitudes also apply survey weights to estimate PATEs (see Supplementary Information, section 4.7). Sample average treatment effects, which are very similar, are provided in Supplementary Information, sections 3.2–3.5.
We have complied with all relevant ethical regulations. The overall project was reviewed and approved by the National Opinion Research Center (NORC) Institutional Review Board (IRB). Academic researchers worked with their respective university IRBs to ensure compliance with human subject research regulations in analysing data collected by NORC and Meta and authoring papers based on those findings. The research team also received ethical guidance from Ethical Resolve to inform study designs. More detailed information is provided in Supplementary Information, sections 1.2 and 4.9.
All experimental participants provided informed consent before taking part (see Supplementary Information, section 4.6 for recruitment and consent materials). Participants were given the option to withdraw from the study while the experiment was ongoing as well as to withdraw their data at any time up until their survey responses were disconnected from any identifying information in February 2023. We also implemented a stopping rule, inspired by clinical trials, which stated that we would terminate the intervention before the election if we detected it was generating changes in specific variables related to individual welfare that were much larger than expected. More details are available in Supplementary Information, section 1.2.
None of the academic researchers received financial compensation from Meta for their participation in the project. The analyses were preregistered at the Open Science Foundation (https://osf.io/3sjy2). The lead authors retained final discretion over everything reported in this paper. Meta publicly agreed that there would be no pre-publication approval of papers for publication on the basis of their findings. See Supplementary Information, section 4.8 for more details about the Meta–academic collaboration.
Further information on research design is available in the Nature Portfolio Reporting Summary linked to this article.
De-identified data from this project (Meta Platforms, Inc. Facebook Intervention Experiment Participants. Inter-university Consortium for Political and Social Research [distributor], 2023-07-27. https://doi.org/10.3886/9wct-2d24; Meta Platforms, Inc. Exposure to and Engagement with Facebook Posts. Inter-university Consortium for Political and Social Research [distributor], 2023-07-27. https://doi.org/10.3886/9sqy-ny89; Meta Platforms, Inc. Ideological Alignment of Users in Facebook Networks. Inter-university Consortium for Political and Social Research [distributor], 2023-07-27. https://doi.org/10.3886/nvh0-jh41; Meta Platforms, Inc. Facebook User Attributes. Inter-university Consortium for Political and Social Research [distributor], 2023-07-27. https://doi.org/10.3886/vecn-ze56; Stroud, Natalie J., Tucker, Joshua A., NORC at the University of Chicago, and Meta Platforms, Inc. US 2020 FIES NORC Data Files. Inter-university Consortium for Political and Social Research [distributor], 2023-07-27. https://doi.org/10.3886/0d26-d856) are available under controlled access from the Social Media Archive (SOMAR) at the University of Michigan’s Inter-university Consortium for Political and Social Research (ICPSR). The data can be accessed via ICPSR’s virtual data enclave for university IRB-approved research on elections or to validate the findings of this study. ICPSR will accept and vet all applications for data access. Data access is controlled to protect the privacy of the study participants and to be consistent with the consent form signed by study participants where they were told that their data would be used for “future research on elections, to validate the findings of this study, or if required by law for an IRB inquiry”. Requests for data can be made via SOMAR (https://socialmediaarchive.org/); inquiries can be directed to SOMAR staff at [email protected]. ICPSR staff will respond to requests for data within 2–4 weeks of submission. To access the data, the home institution of the academic making the request must complete ICPSR’s Restricted Data Agreement. Source data are provided with this paper.
Analysis code from this study (Meta Platforms, Inc. Replication Code for U.S. 2020 Facebook and Instagram Election Study. Inter-university Consortium for Political and Social Research [distributor], 2023-07-27. https://doi.org/10.3886/spb3-g558) is archived at SOMAR, ICPSR (https://socialmediaarchive.org) and made available in the ICPSR virtual data enclave for university IRB-approved research on elections or to validate the findings of this study per the data availability statement above. The data in this study were analysed using R (version 4.1.1), which was executed via R notebooks on JupyterLab (3.2.3). The analysis code imports several R packages available on CRAN, including dplyr (1.0.10), ggplot2 (3.4.0), xtable (1.8-4), aws.s3 (0.3.22), glmnet (4.1.2), SuperLearner (2.0-28), margins (0.3.26) and estimatr (1.0.0).
01 November 2023
A Correction to this paper has been published: https://doi.org/10.1038/s41586-023-06795-x
Lazer, D. M. J. et al. Computational social science: Obstacles and opportunities. Science 369, 1060–1062 (2020).
de Vreese, C. & Tromble, R. The data abyss: How lack of data access leaves research and society in the dark. Political Commun. 40, 356–360 (2023).
Newport, F. & Dugan, A. Partisan differences growing on a number of issues. Gallup https://news.gallup.com/opinion/polling-matters/215210/partisan-differences-growing-number-issues.aspx (2017).
Iyengar, S., Lelkes, Y., Levendusky, M., Malhotra, N. & Westwood, S. J. The origins and consequences of affective polarization in the United States. Annu. Rev. Political Sci. 22, 129–146 (2019).
Finkel, E. J. et al. Political sectarianism in America. Science 370, 533–536 (2020).
Sunstein, C. R. Republic.com 2.0 (Princeton Univ. Press, 2009).
Pariser, E. The Filter Bubble: What The Internet is Hiding from You (Penguin, 2011).
Hosanagar, K. Blame the echo chamber on Facebook. but blame yourself, too. Wired https://www.wired.com/2016/11/facebook-echo-chamber/ (25 November 2016).
Knight, M. Explainer: How Facebook has become the world’s largest echo chamber. The Conversation https://theconversation.com/explainer-how-facebook-has-become-the-worlds-largest-echo-chamber-91024 (5 February 2018).
Johnson, S. L., Kitchens, B. & Gray, P. Facebook serves as an echo chamber, especially for conservatives. Blame its algorithm. Washington Post https://www.washingtonpost.com/opinions/2020/10/26/facebook-algorithm-conservative-liberal-extremes/ (26 October 2020).
Helberger, N. Exposure diversity as a policy goal. J. Media Law 4, 65–92 (2012).
Stroud, N. J. Polarization and partisan selective exposure. J. Commun. 60, 556–576 (2010).
Mutz, D. C. Cross-cutting social networks: Testing democratic theory in practice. Am Political Sci. Rev. 96, 111–126 (2002).
Settle, J. E. Frenemies: How Social Media Polarizes America (Cambridge Univ. Press, 2018).
Gentzkow, M. & Shapiro, J. M. Ideological segregation online and offline. Q. J. Econ. 126, 1799–1839 (2011).
Flaxman, S., Goel, S. & Rao, J. M. Filter bubbles, echo chambers, and online news consumption. Public Opin. Q. 80, 298–320 (2016).
Guess, A. M. (Almost) everything in moderation: New evidence on Americans’ online media diets. Political Sci. 65, 1007–1022 (2021).
Wojcieszak, M. et al. No polarization from partisan news. Int. J. Press/Politics https://doi.org/10.1177/1940161221104 (2021).
Barberá, P., Jost, J. T., Nagler, J., Tucker, J. A. & Bonneau, R. Tweeting from left to right: Is online political communication more than an echo chamber? Psychol. Sci. 26, 1531–1542 (2015).
Eady, G., Nagler, J., Guess, A., Zilinsky, J. & Tucker, J. A. How many people live in political bubbles on social media? Evidence from linked survey and Twitter data. SAGE Open 9, 2158244019832705 (2019).
Auxier, B. & Anderson, M. Social Media Use in 2021. https://www.pewresearch.org/internet/2021/04/07/social-media-use-in-2021/ (Pew Research Center, 2021).
Wojcieszak, M., Casas, A., Yu, X., Nagler, J. & Tucker, J. A. Most users do not follow political elites on Twitter; those who do show overwhelming preferences for ideological congruity. Sci. Adv. 8, eabn9418 (2022).
Bakshy, E., Messing, S. & Adamic, L. A. Exposure to ideologically diverse news and opinion on Facebook. Science 348, 1130–1132 (2015).
Prior, M. The immensely inflated news audience: Assessing bias in self-reported news exposure. Public Opin. Q. 73, 130–143 (2009).
Konitzer, T. et al. Comparing estimates of news consumption from survey and passively collected behavioral data. Public Opin. Q. 85, 347–370 (2021).
Garrett, R. K. et al. Implications of pro- and counterattitudinal information exposure for affective polarization: Partisan media exposure and affective polarization. Hum. Commun. Res. 40, 309–332 (2014).
Lu, Y. & Lee, JaeKook Partisan information sources and affective polarization: panel analysis of the mediating role of anger and fear. Journal. Mass Commun. Q 96, 767–783 (2019).
Arceneaux, K. & Johnson, M. Changing Minds or Changing Channels?: Partisan News in an Age of Choice (Univ. Chicago Press, 2013).
Levendusky, M. How Partisan Media Polarize America (Univ. of Chicago Press, 2013).
Levendusky, M. S. Why do partisan media polarize viewers? Am. J. Political Sci. 57, 611–623 (2013).
Levendusky, M. Partisan media exposure and attitudes toward the opposition. Political Commun. 30, 565–581 (2013).
Hasell, A. & Weeks, B. E. Partisan provocation: The role of partisan news use and emotional responses in political information sharing in social media. Hum. Commun. Res. 42, 641–661 (2016).
Guess, A. M., Barberá, P., Munzert, S. & Yang, J. H. The consequences of online partisan media. Proc. Natl Acad. Sci. USA 118, e2013464118 (2021).
Hobbs, W. R. & Roberts, M. E. How sudden censorship can increase access to information. Am. Pol. Sci. Rev. 112, 621–636 (2018).
DellaPosta, D., Shi, Y. & Macy, M. Why do liberals drink lattes? Am. J. Sociol. 120, 1473–1511 (2015).
Wells, C. & Thorson, K. Combining big data and survey techniques to model effects of political content flows in Facebook. Soc. Sci. Comput. Rev. 35, 33–52 (2017).
Allen, J., Howland, B., Mobius, M., Rothschild, D. & Watts, D. J. Evaluating the fake news problem at the scale of the information ecosystem. Sci. Adv. 6, eaay3539 (2020).
Farr, C. Jack Dorsey: “Twitter does contribute to filter bubbles” and “we need to fix it”. CNBC https://www.cnbc.com/2018/10/15/twitter-ceo-jack-dorsey-twitter-does-contribute-to-filter-bubbles.html (15 October 2018).
McPherson, M., Smith-Lovin, L. & Cook, J. M. Birds of a feather: Homophily in social networks. Annu. Rev. Sociol. 27, 415–444 (2001).
Gerber, A. S., Gimpel, J. G., Green, D. P. & Shaw, D. R. How large and long-lasting are the persuasive effects of televised campaign ads? Results from a randomized field experiment. Am. Political Sci. Rev. 105, 135–150 (2011).
Hill, S. J., Lo, J., Vavreck, L. & Zaller, J. How quickly we forget: The duration of persuasion effects from mass communication. Political Commun. 30, 521–547 (2013).
Coppock, A., Hill, S. J. & Vavreck, L. The small effects of political advertising are small regardless of context, message, sender, or receiver: Evidence from 59 real-time randomized experiments. Sci. Adv. 6, eabc4046 (2020).
Carey, J. M. et al. The ephemeral effects of fact-checks on COVID-19 misperceptions in the United States, Great Britain and Canada. Nat. Hum. Behav. 6, 236–243 (2022).
Coppock, A. Persuasion in Parallel: How Information Changes Minds about Politics (Univ. Chicago Press, 2022).
Golbeck, J. & Hansen, D. A method for computing political preference among Twitter followers. Social Netw. 36, 177–184 (2014).
Eady, G., Bonneau, R., Tucker, J. A. & Nagler, J. News sharing on social media: Mapping the ideology of news media content, citizens, and politicians. Preprint at https://doi.org/10.31219/osf.io/ch8gj (2020).
Bloniarz, A., Liu, H., Zhang, Cun-Hui, Sekhon, J. S. & Yu, B. Lasso adjustments of treatment effect estimates in randomized experiments. Proc. Natl Acad. Sci. USA 113, 7383–7390 (2016).
\
The Facebook Open Research and Transparency (FORT) team provided substantial support in executing the overall project. We are grateful for support on various aspects of project management from C. Nayak, S. Zahedi, I. Rosenn, L. Ahmad, A. Bhalla, C. Chan, A. Gruen, B. Hillenbrand, D. Li, P. McLeod, D. Rice and N. Shah; engineering from Y. Chen, S. Chen, J. Dai, T. Lohman, R. Moodithaya, R. Pyke, Y. Wan and F. Yan; data engineering from B. Xiong, S. Chintha, J. Cronin, D. Desai, Y. Kiraly, T. Li, X. Liu, S. Pellakuru and C. Xie; data science and research from H. Connolly-Sporing, S. Tan and T. Wynter; academic partnerships from R. Mersey, M. Zoorob, L. Harrison, S. Aisiks, Y. Rubinstein and C. Qiao; privacy and legal assessment from K. Benzina, F. Fatigato, J. Hassett, S. Iyengar, P. Mohassel, A. Muzaffar, A. Raghunathan and A. Sun; and content design from C. Bernard, J. Breneman, D. Leto and S. Raj. NORC at the University of Chicago partnered with Meta on this project to conduct the fieldwork with the survey participants and pair the survey data with web tracking data for consented participants in predetermined aggregated forms. We are particularly grateful for the partnership of NORC principal investigator J. M. Dennis and NORC project director M. Montgomery. The costs associated with the research (such as participant fees, recruitment and data collection) were paid by Meta. Ancillary support (for example, research assistants and course buyouts) was sourced by academics from the Democracy Fund, the Guggenheim Foundation, the John S. and James L. Knight Foundation, the Charles Koch Foundation, the Hewlett Foundation, the Alfred P. Sloan Foundation, the Hopewell Fund, the University of Texas at Austin, New York University, Stanford University, the Stanford Institute for Economic Policy Research and the University of Wisconsin-Madison.
\
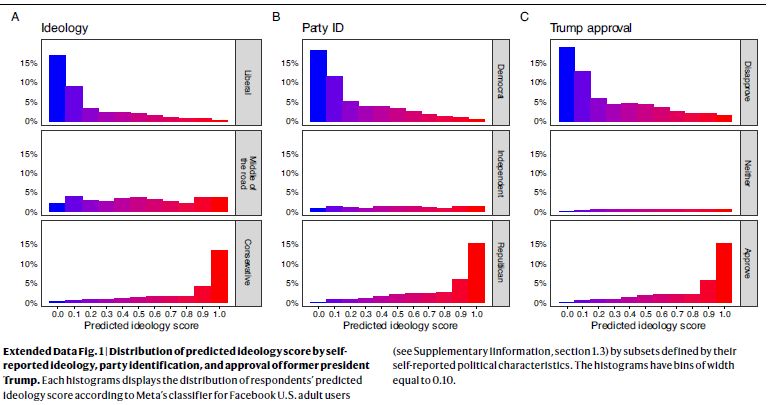
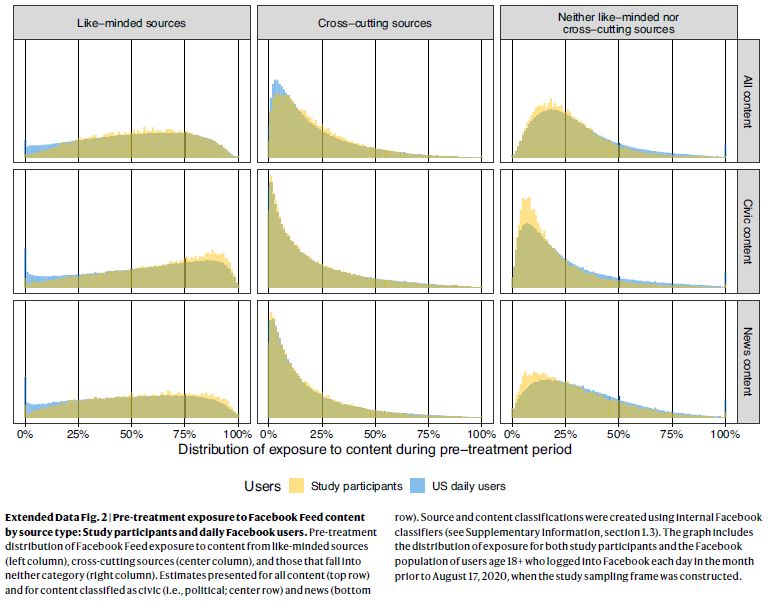
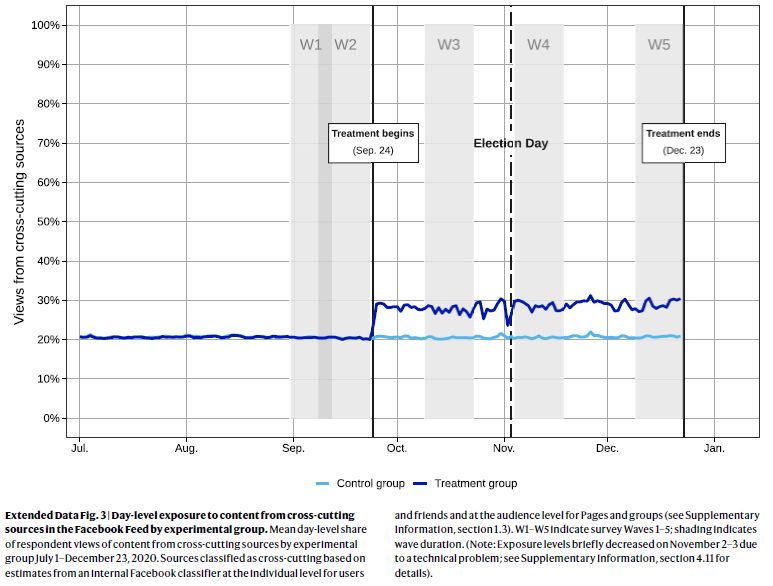
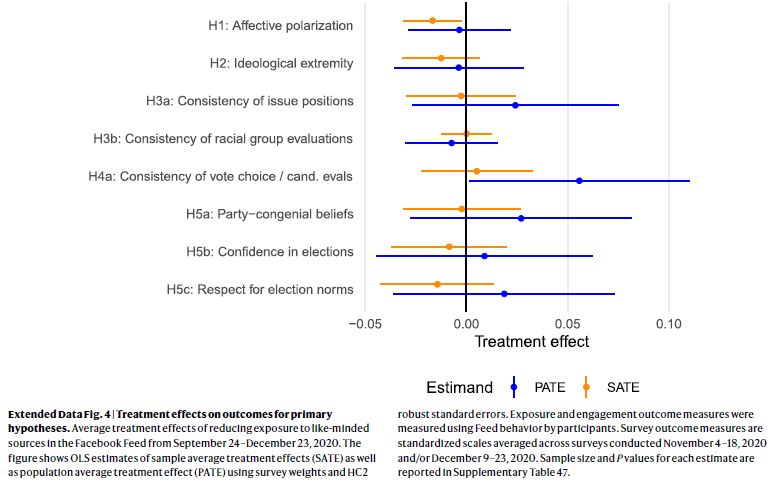
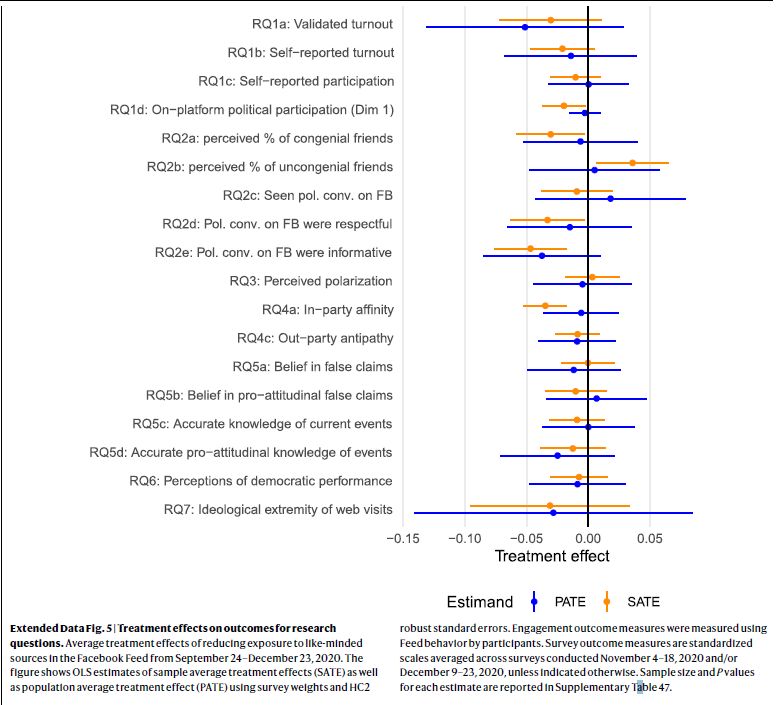
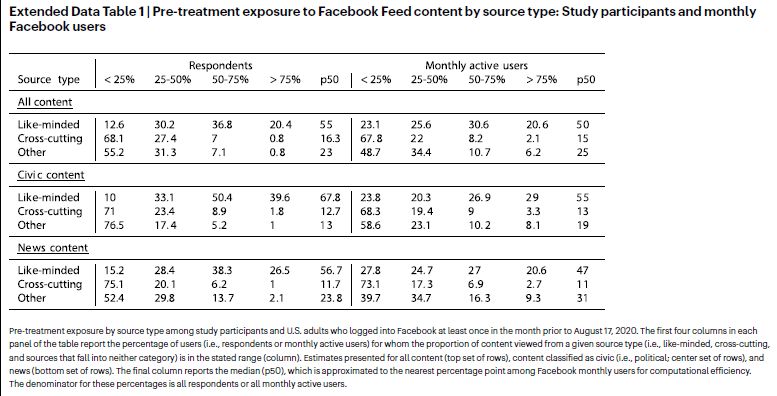
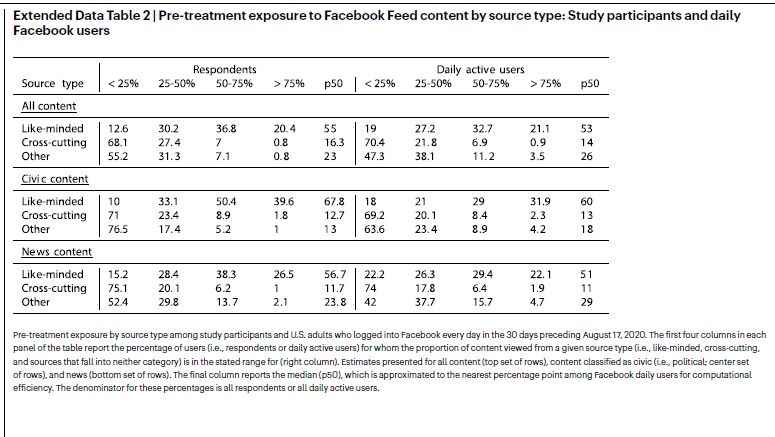
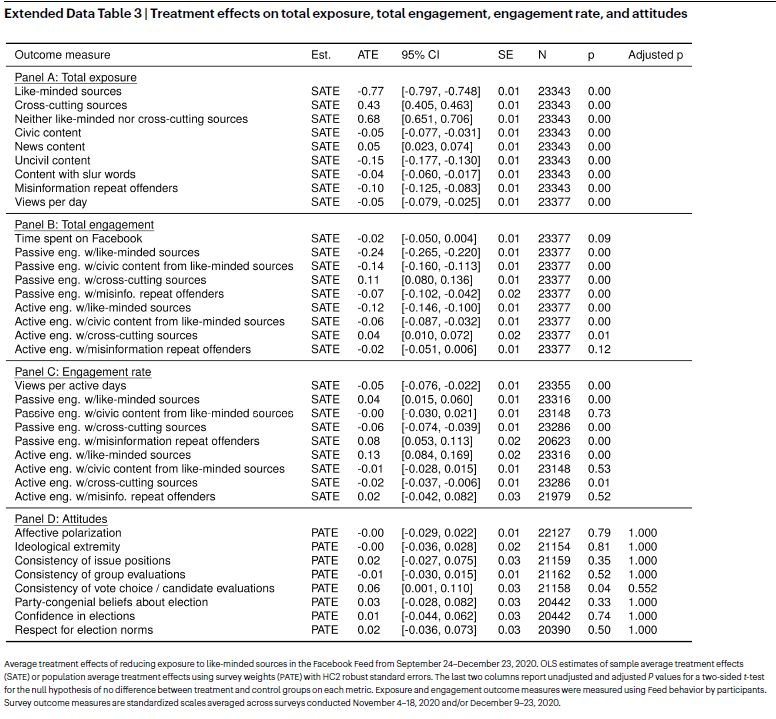
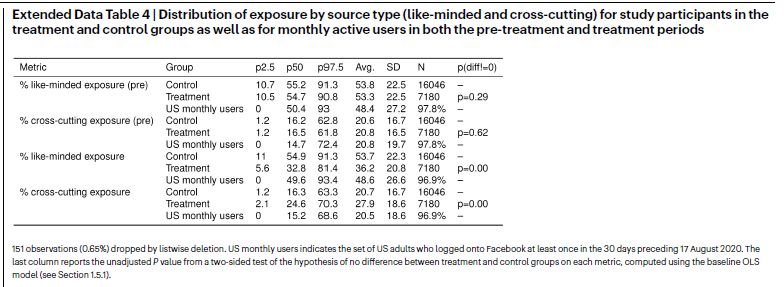
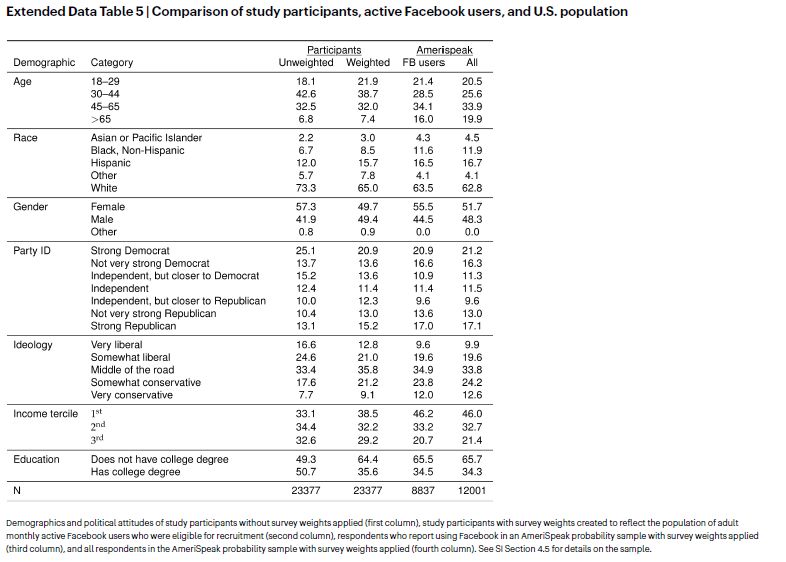
\
:::info This paper is available on nature under CC by 4.0 Deed (Attribution 4.0 International) license.
:::
\
2026-03-10 14:11:01
How are you, hacker?
🪐Want to know what's trending right now?:
The Techbeat by HackerNoon has got you covered with fresh content from our trending stories of the day! Set email preference here.
## SERP Benchmarks: Success Rates and Latency at Scale  By @brightdata [ 8 Min read ]
We benchmark SERP APIs for success rate,
speed, and stability under load. Learn which setup delivers consistent results for AI agents and deep research. Read More.
By @brightdata [ 8 Min read ]
We benchmark SERP APIs for success rate,
speed, and stability under load. Learn which setup delivers consistent results for AI agents and deep research. Read More.

By @pr-securitymetrics [ 2 Min read ] SecurityMetrics announces new CMMC tool for compliance and validation, helping primes and subcontracts streamline the CMMC process. Read More.

By @davidiyanu [ 8 Min read ] Kubernetes isn't breaking your multi-cloud strategy; your org structure is. A senior engineer explains why your deployment pipeline is fighting you. Read More.

By @playerzero [ 4 Min read ] AI-native teams replace 10x engineer dependency with distributed judgment, boosting resilience, speed, and scalable execution. Read More.

By @beldexcoin [ 5 Min read ] Dandelion++ enhances Beldex privacy by protecting transaction origins at the network layer, preventing timing analysis and metadata-based deanonymization. Read More.

By @stevebeyatte [ 5 Min read ] An in-depth guide to th 7 leading requirements management software solutions in 2026. Compare Jama Connect, DOORS, Polarion, and more to find the right fit. Read More.

By @thomascherickal [ 22 Min read ] OpenClaw has exposed the biggest issues in the hyperscaler companies, and it is the leader in AI agents. However, it is a security risk. Use local LLMs instead! Read More.

By @boostlegends1 [ 9 Min read ] Build full-stack web apps without coding. Fabricate uses AI to generate frontend, backend, databases, and payments from simple prompts in minutes. Read More.
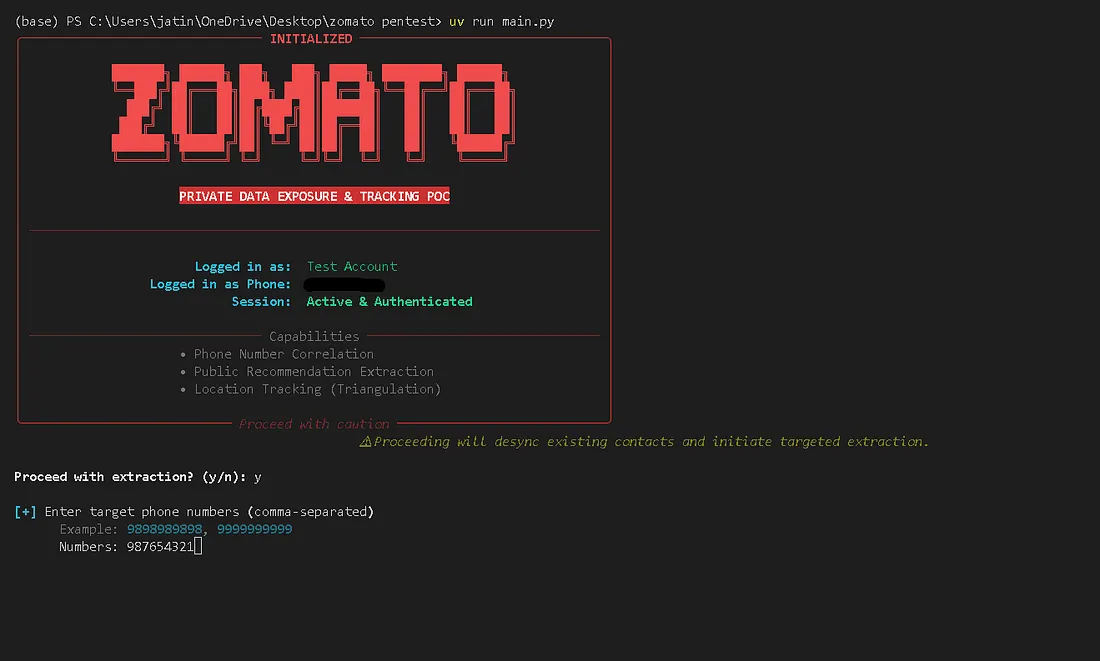
By @jatin-banga [ 12 Min read ] By uploading a phone number, bad actors can extract a user’’ restaurant recommendation history and restaurant coordinates. Read More.

By @joseh [ 4 Min read ] Batman Beyond, Batman Flashpoint, and Batman Inc. are some of the best batsuits in Batman: Arkham Knight Read More.

By @thomascherickal [ 14 Min read ] OpenClaw lets you run frontier AI models like Minimax M2.5 and GLM-5 100% locally on Mac M3 or DGX Spark — zero API costs, total privacy. Here's how. Read More.

By @mexcmedia [ 2 Min read ] MEXC reports 2.35M users across its AI trading suite, with 10.8M interactions and record activity during October’s flash crash. Read More.

By @alexcloudstar [ 11 Min read ] Cloudflare rebuilt Next.js on Vite in one week using AI. Faster builds, smaller bundles, one-command deploy to Workers. Meet vinext.. Read More.

By @jonstojanjournalist [ 4 Min read ] Learn how to use DomoAI from beginner to advanced, including 4K video, lip sync avatars, anime animation, and pro workflows. Read More.

By @manishmshiva [ 7 Min read ] A practical guide to Solana’s architecture, Proof of History, Rust-based development, and how it enables fast, low-cost decentralized applications. Read More.

By @150sec [ 6 Min read ] EU proposes AI Omnibus to delay high-risk AI rules to 2027 and centralize enforcement, reshaping how companies comply with the AI Act. Read More.
By @scylladb [ 9 Min read ] Tencent Games built a real-time CQRS analytics system with Pulsar and ScyllaDB to power global gameplay monitoring and risk control. Read More.
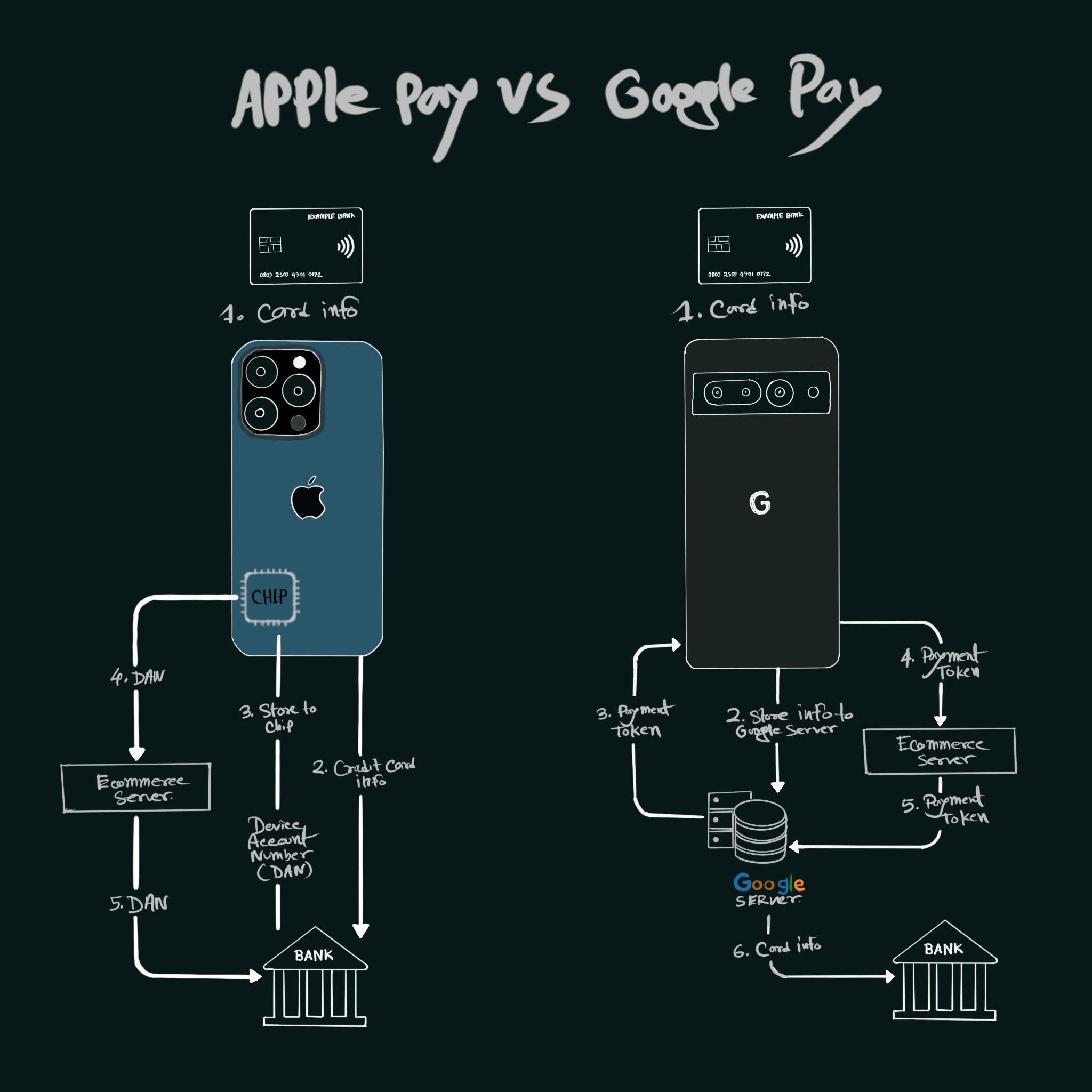
By @omotayojude [ 3 Min read ] Discover the technical differences between Apple Pay and Google Pay security. Learn how Device Account Numbers and cloud tokenization protect your money. Read More.

By @aimodels44 [ 2 Min read ] Qwen3.5-9B is a compact vision-capable LLM with 262K native context, MoE efficiency, strong math/coding, and 201-language support. Read More.

By @thegeneralist [ 8 Min read ]
AI isn’t being adopted so much as installed. Sci-fi saw the power structure first, and that lens helps explain AI, work, and who pays first. Read More.
🧑💻 What happened in your world this week? It's been said that writing can help consolidate technical knowledge, establish credibility, and contribute to emerging community standards. Feeling stuck? We got you covered ⬇️⬇️⬇️
ANSWER THESE GREATEST INTERVIEW QUESTIONS OF ALL TIME
We hope you enjoy this worth of free reading material. Feel free to forward this email to a nerdy friend who'll love you for it.
See you on Planet Internet! With love,
The HackerNoon Team ✌️
.gif)